It isn’t always possible to block intrusion and other malicious activity on your network. Because of the inevitability of harmful events, your security strategy should be to track activity. If you can block intrusion, you should at least be aware that it has occurred.
Hackers keep abreast of the latest developments in cybersecurity and construct strategies to counter them. One of the biggest requirements of an advanced persistent threat (APT) is the ability to retain access. Cracking a system’s passwords requires great effort and investment. Once in, the hacker needs to squeeze value out of that access in order to recoup that investment. Covering tracks to evade detection is a key requirement of the APT strategy.
Log files record all actions on a system and SIEM systems exploit these data sources to identify malicious activity. Therefore, those log files are obvious targets for intruders who aim to hide their presence. Protecting files from tampering is now an essential part of cybersecurity. These files are the source material for security investigation and your entire system protection strategy will be useless if the records in those log files are not protected.
Here is our list of the six best file integrity monitoring tools:
- SolarWinds Security Event Manager EDITOR’S CHOICE A top SIEM system that integrates a file integrity manager to ensure that log files feeding event data into security assessments are not tampered with. Installs on Windows Server. Access a 30-day free trial.
- Datadog Security and Compliance Monitoring Be among the first to trial this new security service from the cloud-based Datadog system monitoring platform.
- ManageEngine EventLog Analyzer A suite of data security services that centers on log file management. This is available for Windows Server and Linux.
- Netwrix Auditor A package of access rights management and data protection service that includes a file integrity monitor. Installs on Windows Server.
- OSSEC A free, open-source host-based intrusion detection system (HIDS) that includes file integrity monitoring. Installs on Windows, Linux, Unix, or macOS.
- Samhain File Integrity A free, open-source file integrity monitor and HIDS. This system is written for Linux, Unix, and macOS and can run on Windows over Cygwin.
File integrity monitoring
File integrity monitoring (FIM) is the field of protecting files from tampering. Typically, there are two methods for protecting files. The first is to calculate a checksum on the properties of a file whenever it is written to by an authorized process. The second is to take a copy of the file and then repeatedly compare the live file to the backup.
Some systems will just alert you to any unauthorized change, in which case, you will need to have separate backup and restore procedures in place. Early APT incidents took years to discover, giving hackers free rein to exploit system resources and interfere with the operations of the business. File tampering is a telltale sign of malicious activity, so the notification of unauthorized changes to files at least gives you a heads up that something is going on as soon as the intruder starts trying to hide.
Systems that can restore files to their original state are preferable to those that just detect unauthorized change. The ability to see exactly which records an intruder changed lets your security software know exactly which accounts have been compromised and that speeds up the processes to throw that intruder out.
Security requirements
Although, as explained, FIM is an important system protection strategy, you might be driven to investigate FIM systems because of a requirement imposed by a data security standard.
If your business has discovered that it is increasingly difficult to win business without complying with a specific security standard, you might be in the process of instituting all of the systems necessary for compliance.
FIM is a requirement of PCI-DSS and NERC-CIP and it is also considered a best practice for FISMA, SOX, HIPAA, and GLBA. If you are implementing one of these standards, you need to be sure that the FIM system that you choose complies with the requirements of that standard.
Choosing a file integrity monitoring tool
A full-featured system sounds like the best option. However, there are downsides to comprehensive security systems. If every log file on your system is copied, you will need a very large amount of disk space. Logfiles already require a lot of room to store and doubling the volume of log files makes that problem worse.
Although small networks don’t produce too much log traffic, larger systems can generate a very large amount. Processing those logs meaningfully requires a lot of processing power. The perfect security system with an active, live FIM would end up requiring more processing power and file space than the original system. Your business would end up spending more money on log file management than your core operations. So, clearly, the best FIM systems involve some sort of compromise.
In order to keep security services manageable, you need a FIM that is able to be smart. You need to find a system that can protect your files without taking over the entire purpose of your IT system. One key compromise is the choice over whether FIM actions are performed in real-time or periodically. Another strategy to look out for is a log management system that can identify which log messages are important and which are of little use for security purposes. Cutting down the volume of records that need to be protected makes FIM manageable.
The best file integrity monitoring tools
With the criteria for intelligent FIM strategies in mind, we have identified the file integrity monitors that are worth trialing.
1. SolarWinds Security Event Manager (FREE TRIAL)
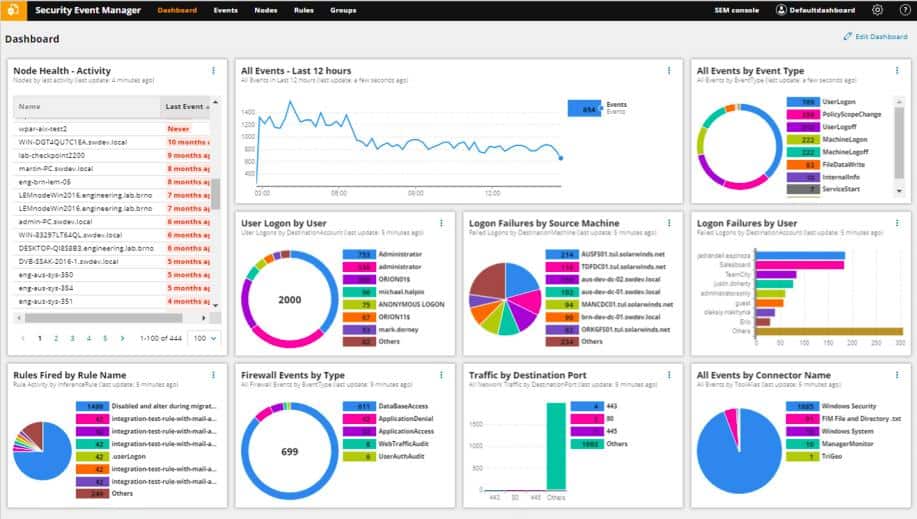
SolarWinds Security Event Manager is not primarily a FIM system. It is a SIEM service that exploits log messages to search for malicious activity. However, this service has file integrity monitoring integrated into it.
The FIM strategy of the SolarWinds Security Event Manager creates efficiency. This is because the process integrates its own log file server. This is the system that collects log messages, sorts and filters them for relevance, and then stores them. So, it is able to identify which log messages are potentially important and which don’t really relate to security.
The Security Event Manager operates three functions simultaneously: it examines event records live as they arrive, it stores log messages for analysis, and for standards compliance, and it also works out which log records need to be protected against tampering.
The Security Event Manager is suitable for businesses that are enrolled in SOX, HIPAA, PCI DSS, NERC CIP, FISMA, and SANS Critical Security Controls programs. This is on-premises software that installs on Windows Server. SolarWinds offers the Security Event Manager on a 30-day free trial.
EDITOR'S CHOICE
SolarWinds Security Event Manager is our top pick for a file integrity monitoring tool because it integrates FIM into its SIEM data collection processes. This early integration of file integrity management offers a solution to the problem of heavy processing power required for full, live log file protection. The system is able to identify key log records that require full protection, thus reducing the volume of data that needs to be duplicated for backup.
Start 30-day Free Trial: solarwinds.com/security-event-manager/registration
OS: Windows Server
2. Datadog Security and Compliance Monitoring
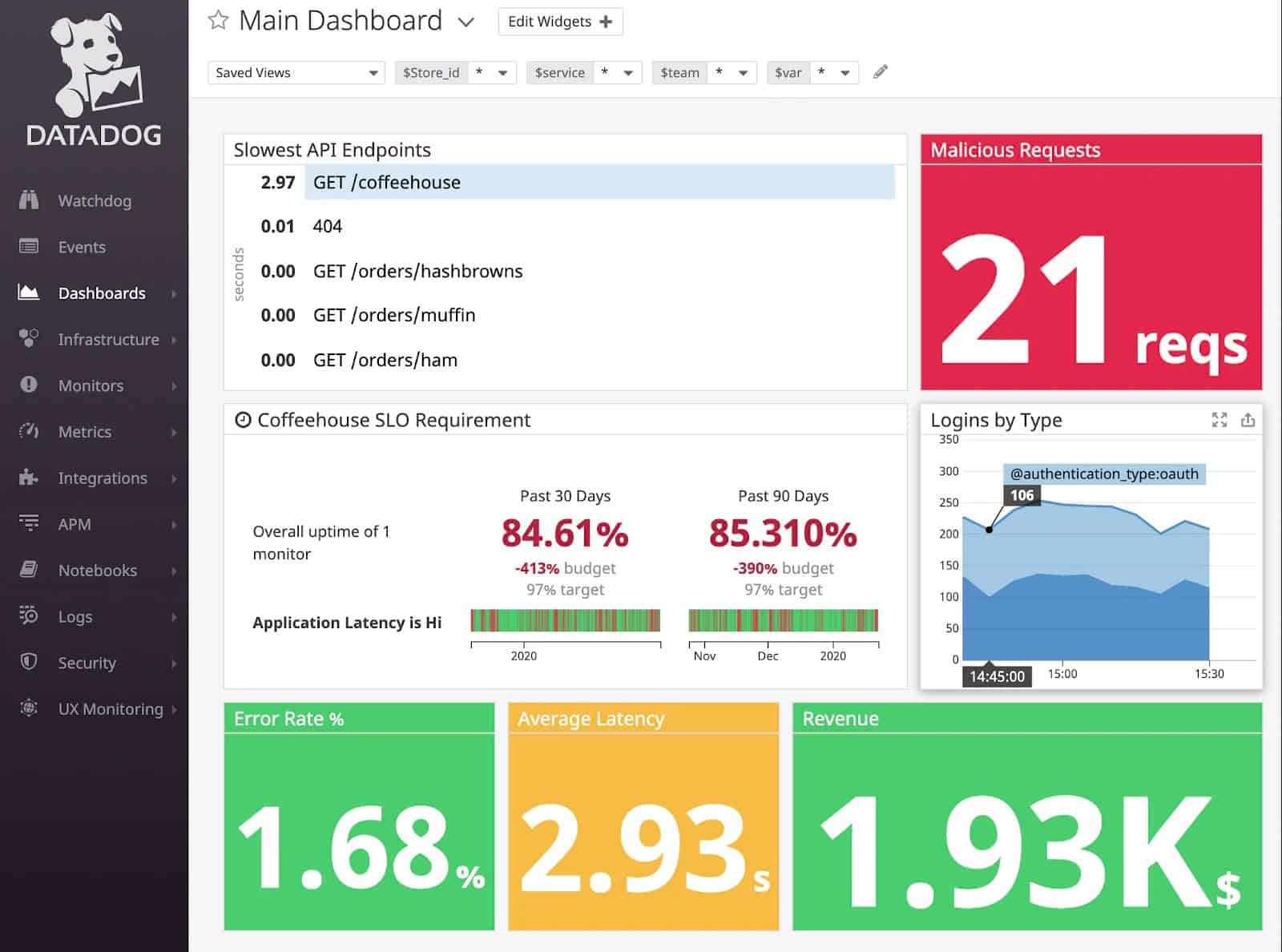
Datadog is a cloud platform of monitoring tools for a wide range of systems including networks, servers, applications, and websites. The platform doesn’t have a security service, such as a SIEM system. However, there is a new security system that Datadog has just put together and it is currently under Beta release.
You won’t see the Datadog Security and Compliance Monitoring explained on the main sales pages of the Datadog website. Instead, you need to request to be enrolled in the service. The security system is fully developed and includes sophisticated screens, showing recent security events.
This Datadog service is very similar to the SolarWinds Security Event Manager in that it combines log file collection with security detection.
The service applies detection rules to all incoming event messages and identifies records that require further investigation. Those events that could potentially indicate intrusion if combined with later events are put to one side for storage. The system then looks out for expected indicators to either strengthen or allay suspicion. Those stored records of potential threat indicators are protected by FIM. Thus, the processing load and storage demands of file integrity monitoring are greatly reduced.
Use this form to request special access to the Datadog Compliance Monitoring system.
3. ManageEngine EventLog Analyzer
ManageEngine EventLog Analyzer is a SIEM tool that protects its log files with file integrity monitoring. This protection extends to critical system files and folders. The tool will record all changes, such as deletion or alteration of records and even the alteration of file and folder access permissions. These changelogs identify the time of the change and the user account responsible for the alteration.
The security service runs two levels of file integrity monitoring. It executes periodic checks on all files for changes and records what those changes were – it doesn’t offer any rollback option on these files. Critical files are subjected to live monitoring, so any changes to those files and folders generate alerts. These critical file changes are reported with before and after snapshots, so those changes can be reversed.
The FIM functions and auditing features of ManageEngine EventLog Analyzer help with compliance to PCI-DSS, SOX, HIPAA, and FISMA. Reports can be extracted into CSV files for further analysis or produced as PDF presentations.
The EventLog Analyzer isn’t just a file integrity monitor. Its functions offer a range of system protection measures, which include User and Entity Behavior Analytics (UEBA) to help you spot compromised accounts and endpoints that are being manipulated. The combination of functions in one package creates greater efficiency and enables the security service to provide several services with the same procedures, simultaneously optimizing the use of CPU, memory, and storage space.
The ManageEngine system is available in three editions. These are: Free, Premium, and Distributed. The Free edition is limited to monitoring five log sources and it doesn’t include file integrity monitoring. The difference between the Premium and Distributed editions is that the Premium service covers one site, but the Distributed plan will monitor activities on many sites.
The software for the EventLog Analyzer installs on Windows Server or Linux and you can experience it on a 30-day free trial.
4. Netwrix Auditor
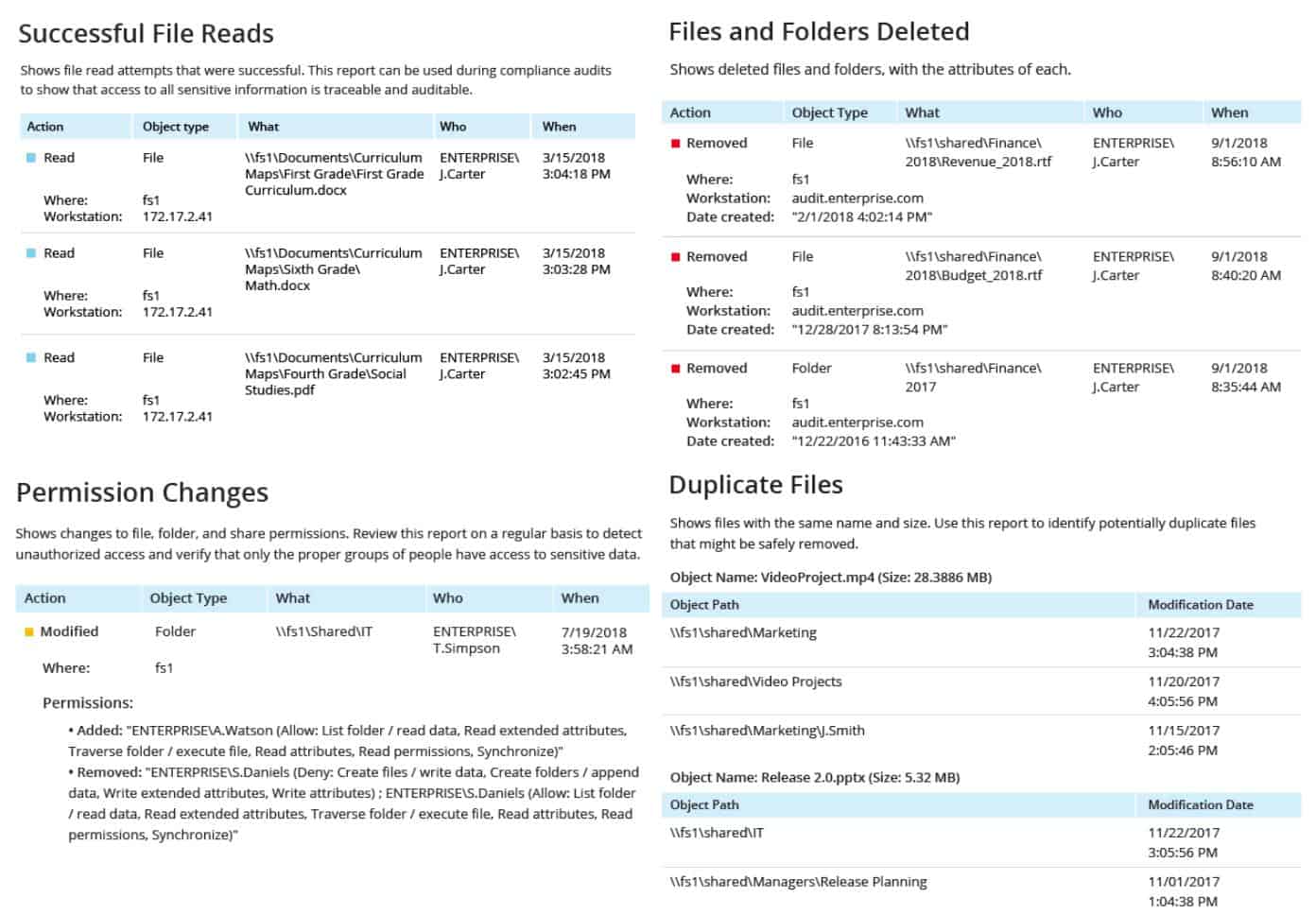
Netwrix Auditor for Windows File Servers includes a comprehensive file integrity monitor that logs the creation, modification, and deletion of files and folders. This tool is a good auditor for those who need to comply with PCI DSS, HIPAA, and FISMA.
The Netwrix Auditor tool is purely and monitoring and reporting system. It doesn’t perform file backup and restore functions. However, for the sake of most security standards, you don’t need to protect those files, just report on access attempts and changes to data.
As well as reporting on changes to files and folders, the Netwrix Auditor service can be set up to report on file access. This monitoring service doesn’t apply to all files and folders – that would be an unwieldy system. Instead, it identifies stores of sensitive data and monitors those.
The file integrity monitoring service in Netwrix Auditor is part of a wider collection of security monitoring and reporting features. As well as observing changes to sensitive files, this tool will help you tighten up access rights by improving the granularity of the user groups that you maintain in Active Directory. By combining access rights management with file integrity monitoring and event audit reporting, Netwrix Auditor provides all of the data protection services that you need for standards compliance.
Netwrix Auditor is delivered as on-premises software for installation on Windows Server. You can test this file integrity monitoring tool on a 20-day free trial.
5. OSSEC
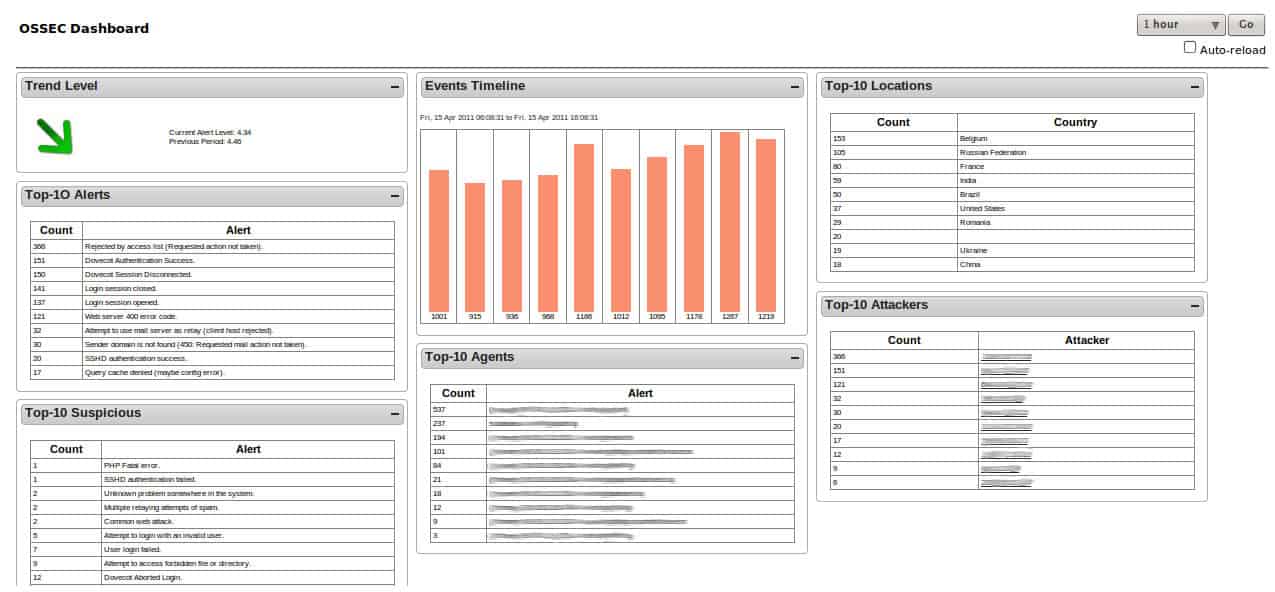
The OSSEC system is a seminal host-based intrusion detection system (HIDS). The software is actually owned by Trend Micro. However, it is free to use and it includes a file integrity monitor.
Host-based intrusion detection systems collect and analyze log files. The integrity of those files is crucial to the successful detection of interlopers because much of the real work of these systems occurs on historical records. The FIM tool built into OSSEC is called Syscheck.
Not every intrusion can be identified immediately, seemingly innocent acts only indicate malicious activities when they are identified in combination. Thus, the HIDS needs to keep records of activities and re-scan them as new log messages arrive.
Syscheck runs on a cycle, scanning files for changes every six hours. This strategy reduces the amount of demand the system places on your CPU. However, the trade-off for that system resource efficiency is a delay in detecting unauthorized file changes.
The OSSEC system’s server program installs on Linux, macOS, and Unix and there is an agent program for monitoring Windows systems. The server can also run on top of VMWare, which is probably a better option for those who don’t have any Linux servers on-site.
6. Samhain File Integrity
Samhain is another free open-source HIDs. However, the file integrity monitoring service of this system gets equal billing – it is advertised as a file integrity monitor and host-based intrusion detection system.
The FIM in Samhain works on a checksum system. This calculates a value based on various attributes of the file and stores those sums in a table. The service periodically recalculates those sums and if the result comes out differently for a file, the system can tell that the contents of the file have changed. This is a good system from the aspect of confidentiality because it doesn’t need the FIM to get access to data. However, this also means that there are no data restore capabilities in the tool.
The HIDS part of Samhain relies on logfiles. The file integrity service isn’t limited to just monitoring the HIDs source log files – it will perform integrity checks on stores of files that hold sensitive data as well.
The system can be set to run continuously in memory or it can be launched periodically. The live running version will give instant notifications to system administrators whenever a file is changed.
Other security features in this package include rootkit detection and the identification of hidden or fake processes. The service will also scan for open ports. A nice feature of Samhain is that it has a “stealth mode” that enables it to run in secret. This helps it avoid detection by hackers who might try to kill detection systems so that they can remain hidden.
The Samhain software is available for Linux, Unix, and macOS. It is possible to run an agent program on Windows systems over a Cygwin interpreter. However, you will still need to have the main server system of Samhain running on another server that has Linux, Unix, or macOS as the operating system.
L’article 6 Best File Integrity Monitoring Tools est apparu en premier sur Comparitech.


0 Commentaires