 A massive database of more than 5 billion records collected from a range of previous data incidents was exposed on the web without a password or any other authentication required to access it, according to Comparitech researchers.
A massive database of more than 5 billion records collected from a range of previous data incidents was exposed on the web without a password or any other authentication required to access it, according to Comparitech researchers.
The database was stored by Cognyte, a cybersecurity analytics firm that stored the data as part of its cyber intelligence service, which is used to alert customers to third-party data exposures. If a client’s contact information appeared in the database, for example, they could receive an alert notifying them that one of their accounts had been compromised. Or if they use a password that has previously been breached, they could get a notification to change it.
Ironically, the database used to cross-check that personal information with known breaches was itself exposed. The information included names, passwords, email addresses, and the original source of the leak.
Cybersecurity expert Bob Diachenko, who leads Comparitech’s security research team, discovered the exposed data on May 29, 2021 and alerted Cognyte, who secured it three days later.
Cognyte gave Comparitech the following statement:
“Thanks to the information provided by the security researcher, Volodymyr “Bob” Diachenko, Cognyte was able to rapidly respond to and block a potential exposure. We appreciate such a responsible and constructive approach, which helps raising awareness and induces companies and organizations to implement security safeguards and better protect their data.”
Timeline of the exposure
The data was exposed for at least four days. Here’s what we know happened:
- May 28, 2021: The database was indexed by search engines.
- May 29, 2021: Diachenko discovered the database and immediately notified Cognyte as per our responsible disclosure policy.
- June 2, 2021: Cognyte secured the data.
We do not know if any other third parties accessed the data during the time when it was exposed, nor do we know for how long it was exposed prior to being indexed by search engines. Our honeypot experiments show that attackers can find and access exposed data in a matter of hours.
What information was exposed?
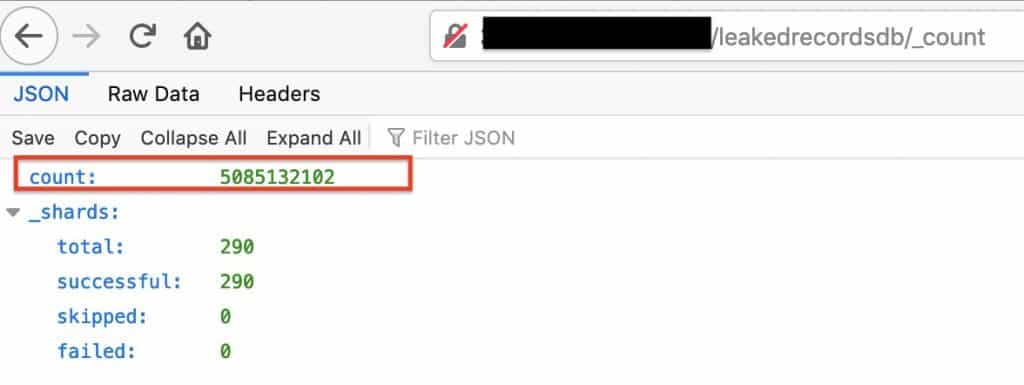
The data was stored on an Elasticsearch cluster. In total, it contained 5,085,132,102 records. Each contained all or some of the following information:
- Name
- Email address
- Password
- Data source
Not all of the data breaches from which the data was sourced included passwords, however we could not determine an exact percentage of records that contained a password.
Some of the previous data breaches from which data was sourced include:
- Zoosk
- Tumbler
- Antipublic
- MySpace
- Canva
- Verification.io
- iMesh
- Edmodo
- VK
- Exploit
- Master Breach Comp
- Rambler
- Onebip
- Scentbird
- Appen.com
- Toondoo
- Wishbown
- Wattpad
- Mathway
- Promo.com
- MGM
- Estante (Brazilian book shop)
Danger of exposed data
Although all of the data had presumably been breached before, it could still pose a risk to end users if any malicious actors accessed it.
The passwords are of particular concern. Even if the user has changed the password for the account in question, attackers can still use it to attempt logins on other accounts. This is called a credential stuffing attack, and it leverages the fact that many people reuse passwords across multiple accounts.
Once an attacker has broken into an account, they will take steps to lock out the genuine user by changing their password and account recovery settings. They can then use and abuse the account as if it were their own.
The data could also be used for phishing attacks, in which the attacker sends an email or message posing as an authority figure, such as someone at the company from which the data was stolen. Such a phishing email would instruct victims to click on a malicious link to a fake website where they enter their password or payment information.
About Cognyte
Israel-based Cognyte [NASDAQ:CGNT] describes itself on its website as “a global leader in security analytics software that empowers governments and enterprises with Actionable Intelligence for a Safer World. ” It goes on to say, “We help security organizations analyze and visualize disparate data sets at scale to help their teams find the needles in the haystacks.”
” It goes on to say, “We help security organizations analyze and visualize disparate data sets at scale to help their teams find the needles in the haystacks.”
The company claims to have more than 1,000 government and enterprise customers in more than 100 countries.
Cognyte was spun off from Verint, a customer engagement company, in 2021.
Why we reported this data incident
Comparitech researchers regularly scan the web for exposed databases containing personal information. When we find an unsecured database, we launch an investigation to determine who is responsible for it, who is potentially impacted, the types of data exposed, and the possible consequences for end users.
Once we identify whomever is responsible for the data, we immediately send them an alert per our responsible disclosure policy. Once the data has been secured and our investigation concludes, we publish an article like this one to raise awareness and curb harm to end users.
Previous data incidents
Comparitech has published several data incident reports like this one, including:
- British Gas software vendor exposes 3.6 million customer email addresses
- India visa agency exposes 6,500 traveler’s visa applications on the web
- Utah COVID-19 testing service exposes 50,000 patients’ photo IDs, personal info
- Car dealer marketing service Friendemic exposes 2.7 million consumer records
- Gym chain Town Sports exposes 600,000 records of members and staff
- Prison phone service Telmate exposes messages, personal info of millions of inmates
- Social media data broker exposes nearly 235 million scraped profiles
- UFO VPN exposes millions of logs including user passwords
- 42 million Iranian “Telegram” phone numbers and user IDs were breached
- Details of nearly 8 million UK online purchases leaked
- 250 million Microsoft customer support records were exposed online
- More than 260 million Facebook credentials were posted to a hacker forum
- Almost 3 billion email address leaked, many with corresponding passwords
- Detailed information on 188 million people was held in an unsecured database
- Over 2.5 million CenturyLink customer records leaked
L’article 5 billion records from previous data breaches leaked by cybersecurity company est apparu en premier sur Comparitech.


0 Commentaires