Egregor first emerged in September 2020, so this is a recently created ransomware threat that could still threaten your business.
However, Egregor isn’t just a ransomware system; it also allows hackers long-term stealth access to company resources. This is an attack strategy that is known as an Advanced Persistent Threat (APT)
In an APT, a hacker can spend months accessing a system without being detected. Unfortunately, there is evidence that this is the case with the hackers that use Egregor. In addition, the Egregor hackers are also known for stealing data and using it for blackmail. In short, Egregor is an all-around security nightmare.
Egregor is a particular headache for businesses bound to follow data privacy standards, such as HIPAA, PCI DSS, or GDPR. This is because the hackers routinely publish part of the data they steal before the ransomware encryption takes effect. This event causes victim companies to be fined for insufficient data protection, and they are also liable to be sued by the people to whom the stolen data relates. In these instances, not paying the ransom and restoring from backup is not an option because the group will then go on to release all of the stolen data.
What does Egregor mean?
The name Egregor comes from both Ancient Greek and Eastern mysticism. It refers to a group effort to conjure up a magical spirit. It can also refer to a psychic connection between members of a group. The word is also sometimes spelled as egregore.
Where does Egregor ransomware come from?
Cybersecurity analysts don’t have an obvious idea of where the hacker group behind Egregor operates. However, it is strongly suspected that this is the group behind Maze, in which case, these are Russian hackers. Furthermore, the Egregor ransomware first appeared close to the time that the Maze group shut down. This leads analysts to believe that either the same group or some of the developers behind Maze left to form their group.
The Maze system was very well written. These programmers know what they are doing. Also, if this is the Maze group, the Egregor system won’t ever launch against targets in Russia or its allied nations.
As well as having code in common with Maze, Egregor seems to be based on another ransomware system called Sekhmet.
Egregor is made available to other hacker groups on a Ransomware-as-a-Service (RaaS) basis. That means that the hacker group that owns the software doesn’t launch attacks. Instead, it lets other hacker groups access the system through a user portal, and the developers expect a cut of the profits.
How does an Egregor ransomware attack begin?
Unfortunately, because there are so many different groups that use the Egregor service, there is no single attack vector. The RaaS package has an infection tool, but many other users choose their method of entry.
The Egregor ransomware seems to be connected to the QakBot virus. This is a botnet system that gets delivered through phishing emails. It is possible that QakBot isn’t part of the RaaS system but is used by one of the associates of Egregor that use QakBot for entry then manually drops Egregor installers onto the victim system. Additionally, QakBot is known to use DocuSign notifications to infect target computers.
Once the QakBot system has been installed, it creates a backdoor that allows hackers to enter and explore the system. Only high-status targets are then infected with Egregor, while the remainder becomes part of the QakBot botnet.
Other entry methods include an infected Adobe Flash Player installer or infected websites that instruct the visitor to install a browser update. In all cases, the decision to continue to an Egregor infection seems to be made manually. The ransomware is not an automatic follow-on from an initial entry method.
What happens in an Egregor ransomware attack?
One of the most dangerous aspects of Egregor ransomware is that, unlike most ransomware systems, it doesn’t trigger immediately. Effectively, the primary mechanism of Egregor provides remote access Trojan. Hackers using the system can explore the system for months before activating the ransomware’s encryption. This gives them time to acquire user accounts and access rights for different computers across the victim network.
An Egregor invasion is brutal to spot in its early stages because it is an advanced persistent threat, in which the hacker uses hijacked user accounts to look around in the system.
A standard part of an Egregor attack is the extraction of data. This must form part of the RaaS toolkit because no matter what method the attacker uses to get on the system, the Rclone service is always used to steal data and transfer it to the command and control (C&C) server.
The programs that implement the Egregor ransomware attack are DLLs and are not compiled systems. Therefore, the text of the programs would be visible and easy to search through by anti-malware systems. To combat this, the packer encrypts the ransomware files and only decrypts them in sequence as each unit is needed for the attack. The encryption cipher used for this protection is Salsa20.
Once vital information has been stolen, the hackers can relax a little. While most ransomware attacks need to seek out and infect backup stores, that effort is not critical to an Egregor ransomware attack. If the hackers can find and extract stores of personally identifiable information (PII), they have the victim trapped. Disclosure of PII can ruin a business. The threat of releasing that data is more of an incentive for payment for the possibility of data being permanently inaccessible through encryption.
An Egregor ransomware infection starts in many different ways. First, it evolves into a botnet infection or becomes an advanced persistent threat and then a data theft event. Finally, the ransomware is almost a coverup operation – like a thief or a murderer setting fire to the crime scene to destroy evidence.
Egregor ransomware encryption
Egregor uses ChaCha20 and RSA encryption. This is the same combination that both Maze and Sekhmet use. When the encryption process triggers, infected drives will all get encrypted simultaneously because they drop the Egregor ransomware on each computer they manage to break into.
The ChaCha20 encrypts each file on a drive, and the ransomware adds an extra extension to the file names. This is a random series of characters that can be four or five characters in length. A different extension character combination is used for each file. The program then stores the path and name of each file in a list and encrypts that text file with RSA encryption.
RSA is a public-key encryption system. This means that the keys used to encrypt and decrypt the files are different. You cannot derive the decryption key if you know the encryption key; thus, the encryption key can safely be made public while the decryption key is kept private. The RSA encryption for each attack seems to be the same system-wide. While the encryption key is held on the victim’s computer, the decryption key is only available on the C&C server.
Only working files containing data get encrypted, so the computer can still be used afterward. The encryption software does no continue in service, so any new files generated after the attack will not be automatically encrypted. However, the hackers still have access to your system so that those new files could be detected and stolen.
The Egregor ransom
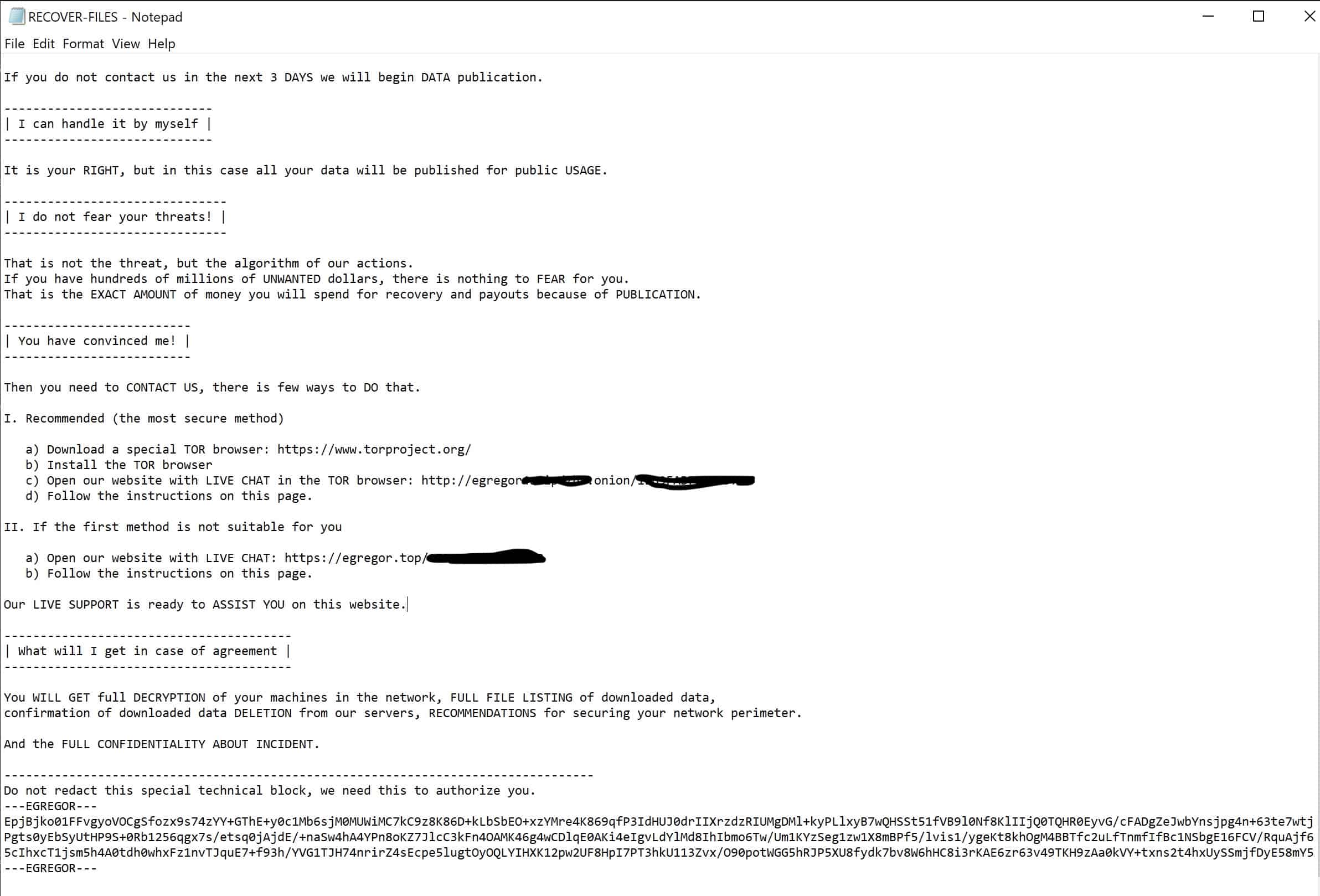
Egregor drops two files on the computer. One is a text file called RECOVER-FILES.txt; the other is an HTA file displayed as the wallpaper of the infected computer.
The screen includes a form to communicate with the hackers. This connects to the C&C server, which is part of the RaaS system. That connection doesn’t always work, but the text file provides a second and third method for communication. The text file contains instructions. This file also contains the RSA public key for the attack.
The message gives instructions on how to communicate with the hackers through a Tor browser. There is also an option to communicate through a chat facility.
Protecting against Egregor ransomware
Although user education and competent anti-malware are essential strategies to protect from all types of malware, with Egregor, you need to have specific cyber-protection systems to prevent an attack from happening. The hackers for Egregor will publish part of your data if you don’t pay within three days. Even a partial release of PII from your system would be catastrophic.
In February 2021, several hackers associated with Egregor were arrested in Ukraine. However, these were some of the affiliate hackers that use the RaaS, not the ransomware owners. The RaaS platform was taken offline for a while after the arrests, but this seems to have been a precaution, and the system is still live. Egregor, therefore, is still a threat to your business.
There is no way to prevent the publication without paying, so there are specific strategies that you need to put in place to keep Egregor from harming your business.
Here are two essential security packages that you should consider:
1. CrowdStrike Falcon Insight (FREE TRIAL)
CrowdStrike Falcon Insight is a thorough protection system against Egregor ransomware because it focuses security activity on endpoints, which are the main entry points for the Egregor hackers. The Insight system coordinates monitoring activities between all of the endpoints on a network, enabling it to spot irregular activity as it spreads and informs all endpoints once one device has been compromised. While the endpoint detection and response (EDR) software is installed on each device, a cloud-based coordinating module gathers threat intelligence and performs different threat detection processes.
The endpoint-resident module is also available as a standalone package called Falcon Prevent. The benefit of having this software running on each device is that it can protect each endpoint should the connection to the network get dropped.
Detection systems in Falcon Insight rely on spotting abnormal behavior, which is the ideal strategy to adopt when you need to combat advanced persistent threats, such as the research phase of an Egregor attack. Automated remediation actions in the package can shut down data theft as well as encryption activity.
You can get a 15-day free trial of Falcon Prevent.
2. ManageEngine DataSecurity Plus
ManageEngine DataSecurity Plus focuses on the protection of sensitive data. His is an essential requirement for protection against Egregor ransomware because if the PII your company holds is stolen, you have no way of avoiding paying the ransom. If you retain PII and follow a data privacy standard, such as PCI DSS, HIPAA, or GDPR, you will need the functions offered by DataSecurity Plus anyway.
The first helpful service this package performs is an eDiscovery sweep. This locates all of your data stores and identifies data that is considered to be sensitive. It then classifies each data collection by a sensitivity ranking.
Step one in PII protection is knowing where that data is. The discovery process is continuous, so any new files or databases created with PII within will be added to the DataSecurity Plus monitoring system’s records. The next priority is to protect those data stores, and DataSecurity Plus includes a file integrity monitor (FIM) to do just that. This system will raise an alert if any categorized datastore is accessed by unauthorized users or modified. It is also able to implement automated actions to protect data. These actions include isolating the device from the network to prevent any transfers.
ManageEngine DataSecurity Plus provides ongoing monitoring of system activity around identified stores of sensitive data. It is available for a 30-day free trial.
L’article What is Egregor Ransomware & How to Protect Against It? est apparu en premier sur Comparitech.




0 Commentaires