A vulnerability manager performs automated checks on system weaknesses for any computer system. You might have heard of “white hat hackers” – people who try to break into a system to check its resistance to attempts by real hackers.
A complete system test that white hat hackers perform is called penetration testing or pen-testing.
A vulnerability manager is an automated penetration tester. While penetration testing can use automated tools that string together system research and attack strategies, a vulnerability manager performs a whole series of tests, rolling on from one to the next without human intervention.
Here is our list of the seven best vulnerability managers:
- Netsparker EDITOR’S CHOICE (ACCESS FREE DEMO) This system focuses on securing applications developed in-house and is mainly concerned with code destined to operate online. In addition, the system can orchestrate with other security products to shut down detected vulnerabilities. Offered as a SaaS platform or for installation on Windows and Windows Server.
- Acunetix (ACCESS FREE DEMO) This security package has a lot of options. It can be used as an automated penetration testing tool, and there is also a version that operates as a full vulnerability scanner. Use it as a cloud service or install it onsite on Windows, macOS, or Linux.
- ManageEngine Vulnerability Manager Plus This package includes a vulnerability scanner and all of the tools you need to act on the discovered weaknesses. Available for Windows and Windows Server.
- Syxsense Secure A cloud platform provides a vulnerability scanner, a port scanner, a patch manager, and endpoint detection and response modules. The EDR software installs on Windows, macOS, and Linux.
- SecPod SanerNow Vulnerability Management This cloud-based system includes a vulnerability scanner and a linked patch manager, among other tools.
- OpenVAS This security system is free to use, and its full name is the Open Vulnerability Assessment System. Written for Linux but will run on Windows over a VM.
- Intruder.io A cloud platform that offers a range of security management services, including a monthly vulnerability scan.
A vulnerability manager is also known as a vulnerability scanner. This tool will work through a list of known hacker strategies. Essentially, that’s all that a white hat hacker does in a pen testing exercise.
Vulnerability management and pen testing
You might wonder, if vulnerability managers and pen testing perform the same task, when would you use each? As it is a software package, a vulnerability manager is cheaper than pen testers. On the other hand, the white hat hackers that perform pen-testing are highly skilled, and there aren’t many of them, so their rates are very high.
Given that vulnerability, managers are so much cheaper than pen testers; why bother with penetration testing? Although vulnerability managers have all of the techniques of hackers built into them, they don’t have intelligence. The vulnerability just looks for the system weaknesses that would let a hacker in. A pen tester can make instant decisions and take rough guesses that can shortcut procedural instructions.
The difference between vulnerability testing and penetration testing is that a vulnerability manager is organized, but a penetration tester is ingenious. You need both system checking strategies. Given the costs involved in penetration testing, it is conducted much less frequently than vulnerability scanning. Even vulnerability scanning doesn’t need to run continuously. A typical schedule for a vulnerability scan is once a month. You can then order an outside consultancy to perform penetration tests on your system once every six months or once a year.
The actual requirements for system security checks vary according to the system. For example, a very stable network with few innovations and a low rate of added software won’t need checks very often. On the other hand, a system that is constantly being expanded by an in-house development team will need more frequent inspections constantly expanding system.
The Best Vulnerability Managers
There are many vulnerability managers on the market today because it is a service that is very heavily in demand. Unfortunately, while some excellent tools are available, there are others that don’t cut the mustard, so you could get stuck with a vulnerability scan that is less than the best.
What should you look for in vulnerability management software?
We reviewed the market for vulnerability scanners and analyzed tools based on the following criteria:
- A vulnerability scanner that will run on demand and a schedule
- The most significant possible number of known vulnerabilities in the scanner’s checklist
- An easy-to-manage software package or cloud platform
- The ability to link the results of the scanner to remediation actions
- Process and results logging for later analysis
- A way to test the system for free with a trial period, a demo, or a money-back guarantee
- Good value for money, represented by extensive tests for a fair price
As well as taking into account these selection criteria, we made sure to find vulnerability managers that businesses that are all Windows or Linux-only can use.
1. Netsparker (ACCESS FREE DEMO)
Netsparker is probably the best vulnerability management tool available for DevOps environments. This is mainly a good choice for the developers of Web applications. The Netsparker tool can offer security advice at every stage of the CI/CD pipeline. The package includes Dynamic Application Security Testing (DAST) and Interactive Application Security Testing (IAST). It is suitable for developers during the build phase, by acceptance testers, when pushing through new development, and by the operations team to check on live systems.
Vulnerability scans by Netsparker work through the Common Vulnerabilities and Exposures (CVE) list produced by The Mitre Corporation. As Netsparker is geared towards developers of Web applications, these reported exploits are not enough. The system also has its method of heuristics that examines code under development for possible pitfalls and security glitches.
For an idea of what this service assesses, think of the coupling between functions and how data exchanges can be manipulated. With code under development, these weaknesses are not necessarily “known exploits” and would pass checks that just look for specific CVEs. However, the connections between modules are known to provide gaps that hackers will gladly squeeze into if it gives them a way in, so Netsparker can spot those potential hazards before too much work has gone into developing the function.
Integration testing and acceptance testing need to look further at how the new code fits into the existing structure of a Web application or site. So, this offers another point in the pipeline where Netsparker can help. It is even possible to automate the code movement through the testing phase by utilizing the integrations available in Netsparker.
At the point of sandboxing a new application, Netsparker will assess the required system settings that support the software. In addition, it will be looking at how the code uses system resources and examining whether the requirements for the software introduced system security vulnerabilities.
Once the code goes live, Netsparker will continue to scan it, examining whether the live environment intrudes new vulnerabilities in the package or whether the new code weakens the security of an existing application.
As it is very focused on in-house development, Netsparker is not so hot on patch management. When the software developers are in the back office, there is no point in looking to the supplier for a patch. However, the Netsparker system can orchestrate responses to weaknesses with other security tools already operating on the network, particularly for the third-party software that the business uses.
Netsparker is available as a cloud platform, and it is also possible to get the system as a software package for installation. The on-premises version runs on Windows and Windows Server. In addition, you can access a demo to assess Netsparker.
Pros:
- Designed to support the CI/CD pipeline
- Integrates with project management tools
- Offers DAST and IAST system tests
- Suitable for operations as well as developers
- Monitors for CVEs and also identifies vulnerable code
- Available as SaaS or for an on-premises installation
Cons:
- It doesn’t include a patch manager
EDITOR’S CHOICE
Netsparker offers comprehensive applications security checks for AppSec, DevSecOps, and DevOps teams. This service can be used for the development pipeline and to re-assess applications that are already live. The service includes Dynamic Application Security Testing and Interactive Application Security Testing to ensure that your new applications and Web pages are fully secure. Netsparker will also scan all of your internal networks to secure the hardware and software that your company uses in-house.
Get a demo: netsparker.com/get-demo/
Operating system: Windows, Windows Server, or Cloud
2. Acunetix (ACCESS FREE DEMO)
Acunetix is a very flexible service because it is offered in three versions, each with different levels of automation, so depending on which edition you go for, you get an automated penetration testing tool or a vulnerability scanner.
This is primarily a Web application scanner. It looks for the OWASP Top 10 in Web applications. These are known tricks that hackers use, such as SQL injection and cross-site scripting. The tool will also scan through look services that support APIs, looking at microservices and serverless systems. In total, Acunetix scans for more than 7,000 Web vulnerabilities – that facility is included in all editions of the product.
Other services in the Acunetix bundle include an Interactive Applications Security Tester (IAST), called AcuSensor, the Acunetix Deep Scan crawler, and the Acunetix Out-of-Band Vulnerability Tester. These tools are available in all editions and can be run on demand. The plans also include a Web application discovery module that chains all services from a starting point in a user-facing system, such as a Web page. In addition, the local services vulnerability scanner will read through code written in JavaScript, .NET framework, and PHP.
The three different versions lend themselves to different deployment scenarios. For example, the Standard edition performs scans on-demand so that penetration testers would use this version. The two higher versions, called Premium and Acunetix 360, offer continuous automated vulnerability scanning.
Those two higher versions are both suitable for businesses that follow data privacy standards. They count towards compliance with PCI DSS, HIPAA, and ISO 27001. The Premium plan is ideal for IT operations departments because it also scans the internal network and internet-accessed Web applications. This network vulnerability scanner looks for more than 50,000 known vulnerabilities.
Both of the higher versions can be used for DevSecOps environments. However, the Acunetix 360 edition is more suitable for the CI/CD pipeline operating scenario because it includes a workflow creation and management system. In addition, constantly expanding system Acunetix offers static, dynamic, and interactive application testing features. These plans also include integrations for orchestrated development management, connecting through to tools such as GitLab, Jira, Jenkins, and Bugzilla.
One of the shortfalls of Acunetix is that it doesn’t include an associated patch manager or configuration manager to fix the problems that it discovers automatically. However, this package is more aimed at Web applications than standard third-party software packages, and that operating environment doesn’t usually produce software updates. However, if you opt for the Premium edition to secure your network, you can connect Acunetix results to a third-party patch manager.
Pros:
- Options for on-demand or continuous scanning
- Scans for OWASP Top 10 and other Web vulnerabilities
- DAST, SAST, and IAST scanning
- An option for network vulnerabilities
- Suitable for CI/CD pipelines
- Integrations with project management tools
Cons:
- No patch manager
Acunetix is offered on the Software-as-a-Service model from a cloud host. However, you can also opt to install the software on your host. The package will run on Windows, macOS, and Linux. You can assess Acunetix by accessing the demo system.
3. ManageEngine Vulnerability Manager Plus
ManageEngine Vulnerability Manager Plus is the ultimate vulnerability management tool because it doesn’t just discover system security weaknesses; it fixes them. While it is common for a vulnerability management package to include both a vulnerability scanner and a patch manager, Vulnerability Manager Plus has many more utilities that act on the vulnerability scan results.
The vulnerability scanner in the Vulnerability Manager Plus bundle scans operating systems, software, and system settings, looking for loopholes known as entry points for hackers. In addition to these standard checks, this scanner assesses other issues not yet listed as known hacker exploits that could be used for attacks. This protects your system against zero-day attacks, which are new strategies that no one has tried yet.
While many vulnerability management services give your system a scan once a month, the ManageEngine system runs every 90 minutes. First, it checks the network for all devices, so it can enroll new devices that you add between scans – you don’t have to set up that new device in the scanner dashboard. Next, the scanner ranks all of the system weaknesses and displays them all in a list ordered by priority.
If you gave the system permission, Vulnerability Management Plus would automatically trigger other modules to fix the problems that it discovers. But, first, it will run the automated Patch Manager. This service is included in the ManageEngine bundle, but it isn’t tied to the vulnerability manager. You can also use it yourself outside of the processes of Vulnerability Manager Plus.
The Patch Manager checks for patch availability, store the downloaders for them and then schedules them for installation. That schedule will work on a series of windows that you specify so that installation doesn’t disrupt normal office activities. It also orders patches accounting for any patch dependencies. Finally, if there is no patch available for the discovered vulnerability, Vulnerability Manager Plus provides a script that will implement a workaround.
Many system weaknesses are due to poorly managed device settings. Vulnerability Manager Plus includes a Configuration Manager that will reorganize those settings and then prevent changes to them. It will also examine all ports and ensure that those not in use are closed. Those that need to be opened will be password protected where possible.
The vulnerability scanner also produces a risk assessment of all of the software that it discovers. In some cases, it will show that a package makes the entire system vulnerable to attack and should be removed.
Pros:
- Performs vulnerability scans every 90 minutes
- Discovers all of the devices connected to the network
- Includes all of the utilities needed to repair discovered weaknesses
- Automatically launches repair actions
- Includes a patch manager and a configuration manager
- Allows the system administrator to decide which actions should be automated
Cons:
- No cloud service version
Vulnerability Manager Plus installs on Windows and Windows Server. It is available in three editions: Free, Professional, and Enterprise. The Free version is limited to managing 25 devices. The Professional edition is suitable for handling a LAN, and the Enterprise edition will cover multiple sites. You can get a 30-day free trial of the Professional edition.
4. Syxsense Secure
Syxsense Secure is a cloud platform that offers a bundle of system security services, including a vulnerability scanner. Other utilities in the package include a patch manager, endpoint detection and response (EDR) system, and a port scanner.
The vulnerability scanner will run at a frequency that you decide, and you can also choose whether to let it automatically trigger the activities of the patch manager. All of the actions performed by all services in the Syxsense Secure package are displayed live on the screen, and those records stay there for you to check on statuses when the scan runs overnight. Syxsense also documents all of its findings by writing to log files. This service complies with all of the requirements of data privacy standards, including PCI DSS, HIPAA, and GDPR.
The patch manager is triggered by the bundle’s vulnerability scanner and device discovery, and software scanning service. The system compiles a software inventory and keeps a check on the availability of updates for those packages.
You set up maintenance windows in the Syxsense dashboard and, when patches are available, the patch manager will schedule them to run at the next open window. Syxsense hosts the Secure system, and that package includes 100GB of storage space for patch installers and log files.
The Syxsense Secure system relies on on-premises agents to implement searches and patches. The EDR module supplies this function. This has to be installed on each endpoint, available for Windows, macOS, and Linux. The EDR is a malware detector that scans new files, watches all processes, and monitors the system registry for changes. In addition, the EDR will automatically implement actions on the protected device to shut down malicious activity. This service also monitors the resource usage on the device.
Pros:
- A package of many security systems built around a vulnerability scanner
- A patch manager that can be launch automatically by the vulnerability scanner
- Endpoint detection and response to protect against malware
- Extensive system audit and logging
- Cloud storage space for log files and patch installers
Cons:
- Overlooks configuration management
Syxsense Secure is available for a 14-day free trial.
5. SecPod SanerNow Vulnerability Management
SecPod SanerNow is a SaaS platform that offers a selection of security services, including a vulnerability manager and a patch manager. These two modules can be set up to work in concert so any software weaknesses that the vulnerability scanner discovers can be fixed automatically with available patches.
The SanerNow Vulnerability Manager has an extensive database of weaknesses to look out for. It contains more than 125,000 known vulnerabilities. This database is constantly updated, so it includes all of the latest exploits used by hackers. Despite having so much to search for, a typical SanerNow scan only takes about five minutes.
The vulnerability scanner reaches out over the network to all endpoints running Windows, macOS, or Linux. It scans each device’s ports and then its settings. The service examines the status of the operating system and then moves on to log all of the software installed on the device. This scan records version numbers and explores the package’s operating settings to spot entry points for hackers.
If the operating systems or software are out of date, the patch manager kicks in and searches supplier sites for patches. If any are available, the patch manager copies over the installers and stores them. Finally, the patches are queued up for installation at the next available maintenance window.
Pros:
- A package of a vulnerability scanner and a patch manager
- A threat detection and response module is also available
- A hosted service with storage space included
Cons:
- It doesn’t have a configuration manager
SecPod SanerNow is available for a 30-day free trial.
6. OpenVAS
The full name of OpenVAS is the Open Vulnerability Assessment System. This is an open-source project, which means it is free to use. You might not jump straight to this option because some businesses have a policy of only using software that is professionally supported. OpenVAS doesn’t have that feature. However, as it is free, you could install it and use it as a benchmark to judge the other vulnerability management tools you test. It isn’t reasonable to expect that a paid product should be better than this free scanner.
The active community that uses OpenVAS is contactable through a community message board. That can be a good source of guidance on using the tool and vulnerability assessments in general. In addition, the vulnerability database is composed of network vulnerability tests (NVTs). Other users of OpenVAS supply these, and the list includes more than 50,000 conditions.
There is a paid version of OpenVAS, which is called Greenbone Vulnerability Management. That has a commercially gathered NVT database and also provides professional support. However, that product is challenging to acquire because Greenbone doesn’t sell its products direct.
OpenVAS installs on Linux, and it is integrated into Kali Linux. Therefore, it is possible to run it on Windows over a VM. This system has a GUI interface and can also be used as a command-line utility.
Pros:
- Open source and, therefore, adaptable
- Free to use
- Suitable constantly expanding system as an introduction to vulnerability scanning
Cons:
- No associated patch manager
- No professional support
The vulnerability scanner is integrated into Greenbone Security Manager as the trial version, which you can download for free.
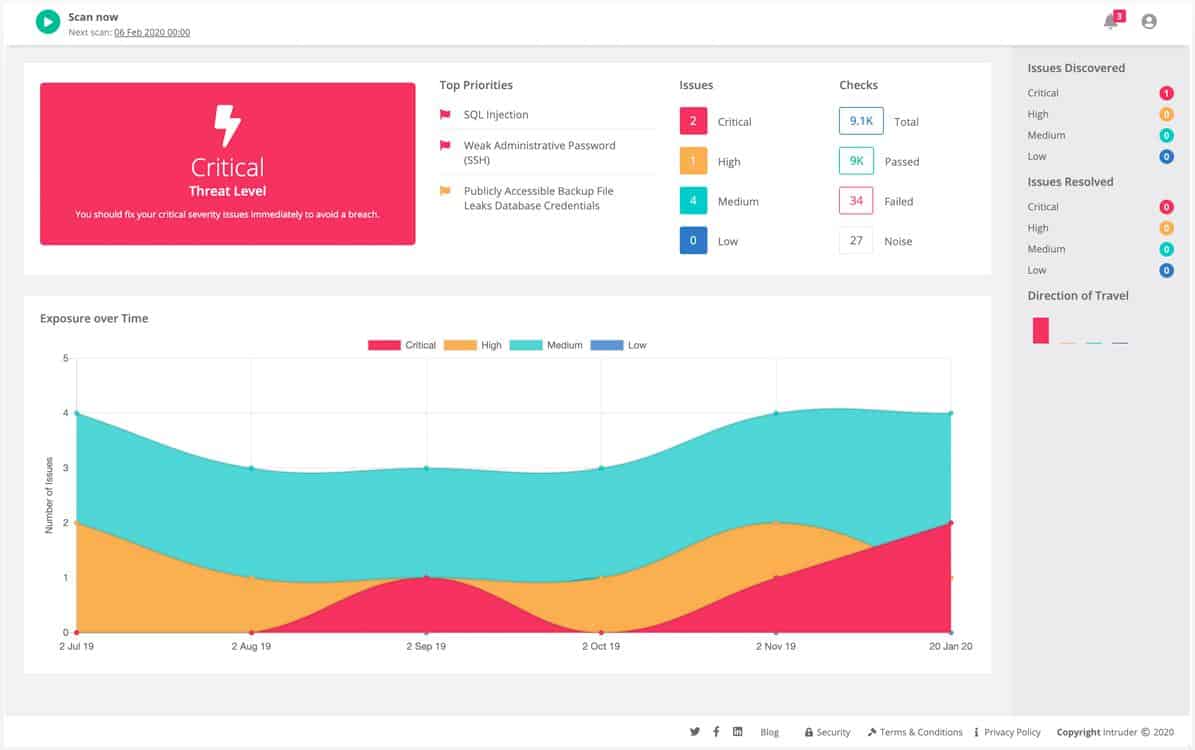
7. Intruder.io
Intruder.io offers a range of plans from its cloud platform. Services from this provider start with a monthly vulnerability scan with accounts specifying the number and location of hosts to scan. These vulnerability scans check websites for known exploits and also examine your network’s external profile. Once your vulnerability to outsiders has been assessed, the system conducts tests from within the network. In total, Intruder.io has a database of around 9,000 vulnerabilities to look for.
The standard vulnerability scanning service is called the Essential edition. You can add on the ability to launch vulnerability scans on demand by choosing the higher Pro edition. This service also monitors possible problems with SSL certificates and examines cloud resources as well as on-premises services. The Pro plan also releases research data on emerging threats to look out for.
The highest plan of Intruder.io is called the Verified edition. This gives you all of the vulnerability scanning features of the Pro edition plus the services of a human penetration testing team.
Pros:
- A choice of service levels from a regular scan up to pen testing
- A hosted system that is managed and kept up to date
- A database of 9,000 exploits that covers websites as well as on-site equipment and software
Cons:
- This service is quite pricey
You can get a 30-day free trial of their Pro edition.
L’article 7 Best Vulnerability Management Tools Reviewed in 2021 est apparu en premier sur Comparitech.


0 Commentaires