McAfee Total Protection for Data Loss Prevention (McAfee Total Protection for DLP) is one of the most prominent data protection systems on the market
This system is a good option for protecting personally identifiable information (PII), subject to stringent legal protection in most developed economies. However, you could benefit from this tool even if your business doesn’t hold the personal information of individuals because it is also a good tool for protecting intellectual property and trade secrets, such as price lists, supplier agreements, and manufacturing specifications.
McAfee is a leading name in the field of cybersecurity. The founder, the eccentric John McAfee, invented the concept of anti-virus. The company began operations in 1987, and John McAfee left the company and sold off the remainder of his holdings in 1994. So, this business has been around for a long time and has been through many transformations over the years.
The business today is partly owned by Intel Corporation but operates as an independent enterprise. The company operates from its headquarters in San Jose, California, and has offices around the world and a prominent presence on the World Wide Web. The company, officially called McAfee Corp., is listed on Nasdaq and, as of August 2021, has a market valuation of $12.8 billion.
What does McAfee Total Protection for DLP do?
McAfee Total Protection for Data Loss Prevention runs on your site and observes activities on your network and all endpoints. There is a central server system for the appliance, and this needs to be set up for the SLP to function. Much of this setup is automated and constantly revised during the system’s operating life.
There are four units to McAfee Total Protection for DLP:
- McAfee DLP Discover
- McAfee DLP Prevent
- McAfee DLP Endpoint
- McAfee DLP Monitor
The system can cover cloud resources as well as on-site systems. On installation, it can search for records of past data access events. It will offer analysis that will inform you of security weaknesses and feed into the automated setup processes of the DLP.
The set-up processes involve examining user accounts, creating security policies, and the discovery and classification of data. Once all of these steps have been undertaken, the system can start to monitor data access and movements according to the specifications of the security policies.
Here is more information about the three units of McAfee Total Protection for DLP and how they interact.
McAfee DLP Discover
McAfee DLP Discover operates through endpoint agents to locate all data stores. It then examines each instance and field of data to assess its sensitivity. There is a built-in data classification system in the McAfee DLP solution. However, it requires a degree of manual involvement, which businesses with a lot of data to sift through might find burdensome. However, it is possible to associate an automated third-party classification system of your choice to take care of that problem.
The central dashboard controls all of the activities of the endpoint agents to interpret the security policies. In addition, you should set up before triggering the data discovery search. These policies can be organized to meet the requirements of data security standards.
McAfee defines its data management strategy in three steps:
- Inventory Locates data stores
- Categorization Identifies which data instances are high priority sensitive data
- Remediation Indexes and maps sensitive data instances
The Inventory step can search through files, databases, and cloud platforms. It can also scan through images of documents, pictures, screenshots, and forms, using OCR.
The Categorization service can identify related fields. These might not constitute PII in isolation but will represent a breach if released together. The Discover service conducts fingerprinting to identify these high-priority field combinations. Fingerprinting moves into the Remediation step, which produces a definitive landscape to which the security policies should be applied.
McAfee DLP Prevent
McAfee DLP Prevent applies the security policies over access controls you set up in the dashboard to the Discover module’s sensitive data. This system monitors all data movement utilities that are launched from endpoints, including email and messaging systems. The module also extends to the monitoring of data accessing applications that are resident on cloud servers.
DLP Prevent offers a range of remediation actions, including encryption, redirection, blocking, and quarantining. In addition, security policies can apply different actions to different sensitivity levels and user types.
Other McAfee DLP Prevent package facilities include performance and event analysis that can also examine logs of data breaches that occurred before the McAfee system was installed. Information gleaned from these studies can help you adjust your security policies, prove conformance with data security standards, or assess SLA goal achievement.
McAfee DLP Endpoint
All of the actions initiated in the Discover and Prevent modules are implemented by endpoint agents, which are installations of McAfee DLP Endpoint. These agents collect data, including sensitive data locations for transfer to the Discover and Prevent services’ server systems and display in the system dashboard, which McAfee ePO implements.
McAfee MVISION Cloud manages cloud resources. Linking the cloud service and the endpoint system together in the ePO-provided dashboard of the DLP system provides a unified view of all data locations used by the enterprise. Additionally, you can link a third-party user and entity behavior analytics (UEBA) system to identify account takeover and insider threats.
On discovering an unauthorized or inappropriate attempt to access, change, copy, or move data, the McAfee DLP Endpoint system alerts the DLP Incident Manager in the ePO dashboard.
McAfee DLP Monitor
McAfee DLP Monitor provides live scanning of network traffic that adds extra security to the controls provided by MacAfee DLP Endpoint. The behavior of this service is controlled by the security policies that you specify in the dashboard. In addition, this monitor contributes to the data pool used by the performance analysis service in the DLP. This acts like a SIEM.
McAfee Total Protection for DLP deployment options
McAfee DLP Prevent and McAfee DLP Monitor are available as physical or virtual appliances. The ePO software installs on Windows Server, and the McAfee DLP Endpoint system is available for Windows and macOS.
McAfee Total Protection for DLP pros and cons
We examined the functionality of McAfee Total Protection for DLP and identified its strengths and weaknesses.
Pros:
- Performs an automated and continuous discovery and classification cycle
- Includes analytical functions that act as a SIEM
- Options to encrypt files to enforce security
- Unifies the monitoring of data on-site and in the Cloud
- Delivered as a physical or virtual appliance
Cons:
- No endpoint agent for Linux
Alternatives to McAfee Total Protection for DLP
The absence in McAfee Total Protection for DLP of endpoint agents for Linux is a big problem. If you have devices that run Linux, you can’t afford to just leave them out of your data protection program. Therefore, you will need to know about some alternative data loss prevention systems.
What should you look for in a McAfee Total Protection for DLP alternative?
We reviewed the market for data loss prevention systems and analyzed the options based on the following criteria:
- The ability to monitor devices running Windows, macOS, and Linux
- The option to combine monitoring for on-site and cloud resources
- Sensitive data discovery and classification service
- File integrity management
- Nice to have an integrated intrusion detection system
- A cost-free assessment opportunity in the form of a free trial or a demo system
- Value for money, represented by a fair price for the breadth of services offered
With these selection criteria, we have formulated a range of options.
Here is our list of the four best alternatives to McAfee Total Protection for DLP:
- ManageEngine DataSecurity Plus A combined vulnerability manager that gives recommendations for security tightening and data loss prevention service. It runs on Windows Server.
- Endpoint Protector This system combines a cloud-based server with endpoint resident agents to provide constant protection that can continue online and an instantly updated threat protection system on the cloud.
- Digital Guardian DLP This data loss prevention platform monitors endpoints and networks to control and block data movements. This is a cloud-based system with endpoint agents for Windows, macOS, and Linux.
- Teramind DLP A cloud-based data loss prevention system that includes user and entity behavior analytics and insider threat assessments.
You can read more about each of these options in the following sections.
1. ManageEngine DataSecurity Plus
ManageEngine DataSecurity Plus comprises four modules that each focus on a different aspect of sensitive data management. For example, the Data Loss Prevention module offers a data discovery and classification service and a security policy creation tool. It is possible to tailor this tool to the requirements of data privacy standards.
This system includes an auditor for Active Directory that will reorganize user accounts to improve security and monitoring opportunities. The combination of tight access control, data classification, and security policies form the operational workflows of this system.
Pros:
- Sensitive data discovery and classification
- Active Directory auditing
- File integrity monitoring and data exfiltration controls
Cons:
- Each module is priced separately
The package implements file integrity monitoring and controls activities USB ports, emails, and file transfer systems. ManageEngine DataSecurity Plus installs on Windows Server, and it is offered on a 30-day free trial.
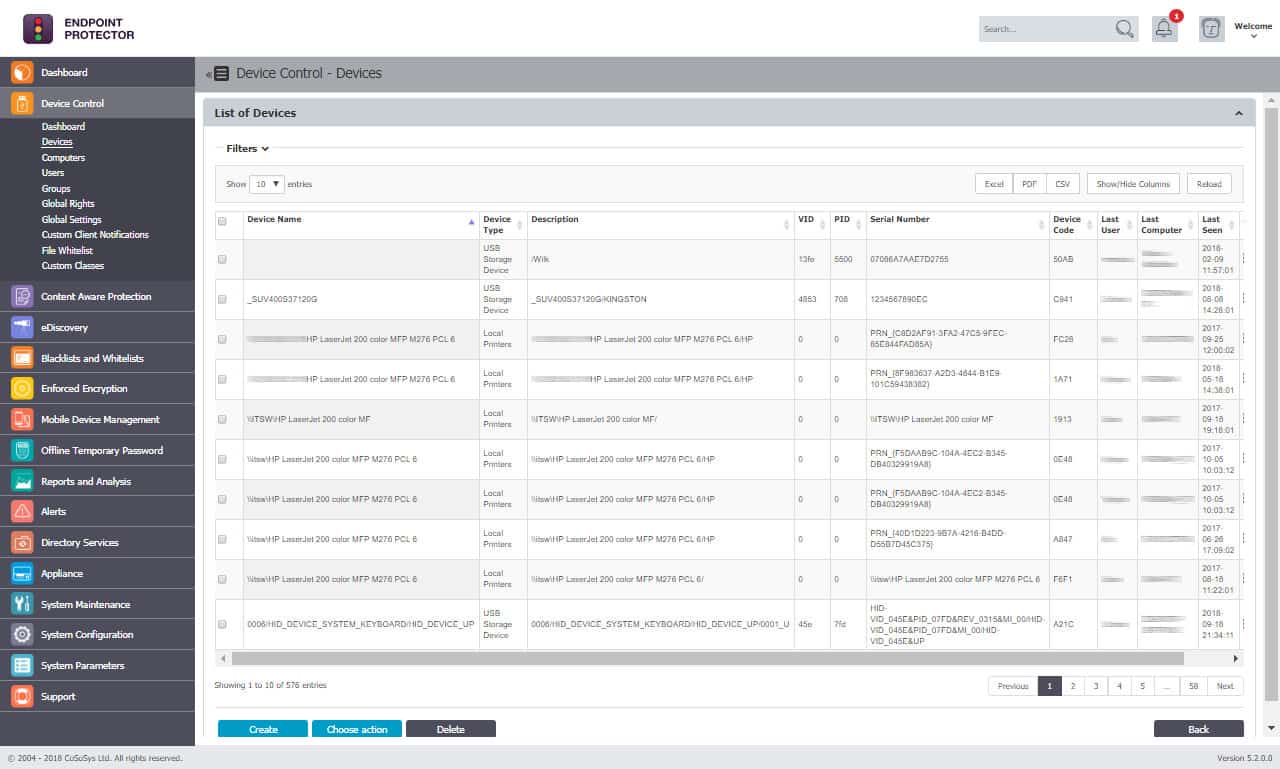
2. Endpoint Protector
Endpoint Protector has endpoint agents for Windows, macOS, and Linux, coordinated from a cloud-based server. In addition, the controller includes a dashboard where you set up your security policies for supervision through the DLP service.
The endpoint agents offer all data protection functionality, so they continue to operate effectively even when the device is disconnected from the network. The cloud service gathers event data from endpoint agents and searches for combined threats. This is a lot like a SIEM configuration.
When beginning operations, you have to enroll devices in the program. However, those devices do not all need to be on the same network, and it is also possible to include cloud resources in the monitoring service.
On starting service, the server will scan and assess your access rights management system, producing suggestions of changes that can be made to tighten security. After installing endpoint agents, the server sends out instructions to starts a sensitive data discovery sweep. The types of data that the endpoint agents look for are modified according to the security policies that you create.
The discovery scan identifies all data and then classifies those instances to work out sensitive data that needs to be protected. The discoverer will then grade the sensitivity of each piece of data and apply the level of protection that is specified in the security policies.
Steps that can be taken to enforce security include the encryption of files to regulate access. The DLP also controls data movement onto printers and removable storage and through emails and file transfers.
The endpoint agents implement user and entity behavior analytics (UEBA). This profiles each user’s behavior and the activity of system processes. With this intelligence, the DLP can establish a baseline of regular activity. Deviations from this standard raise an alert.
Endpoint Protector is a great pick as an alternative to McAfee Total Protection for Data Loss Prevention because it has endpoint agents for Windows, macOS, and Linux. There is also a mobile operating system version, and the service can include the supervision of all platforms plus cloud resources in a unified security monitoring system. In addition, this data protection system includes controls over data exfiltration channels and performs UEBA to identify threats.
Pros:
- Sensitive data discovery and classification service
- Data access controls
- Control of exfiltration channels
- Threat hunting
- Unifies cloud and site security monitoring
Cons:
- Not offered as an appliance
There are several deployment options for the server of Endpoint Protector. It is offered as a hosted SaaS platform, and it can also be accessed in the Marketplace of AWS, GCP, and Azure. The code can also be run on-site over a VM. Experience Endpoint Protector for free by accessing a demo.
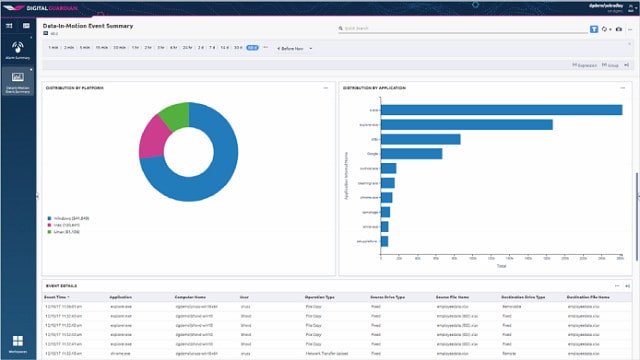
3. Digital Guardian DLP
Digital Guardian DLP runs from a cloud platform through on-device agents. It can monitor activities on any device anywhere, unify multi-site and home-based devices into one monitoring service, and include cloud resources. In addition, each device agent operates independently, ensuring continuity of protection if the endpoint gets disconnected from the network.
The service is controlled from the cloud server, and all actions are performed on endpoints. Administration tasks, such as creating security policies, are performed through the system dashboard, which is accessed through any standard Web browser. In addition, the device agents upload activity reports for endpoints and networks, and these get processed into threat detection and activity reports on the server.
The server will reorganize your access rights management system and kick off a system scan run by the device agents. That sweep discovers all sensitive data locations and categorizes personally identifiable information (PII) and intellectual property. These data locations are then subjected to access monitoring.
Pros:
- Offers threat detection as well as data protection
- Can unify the security monitoring of data on any device anywhere
- Applies security policies through an improved access rights management structure
Cons:
- The prices are only revealed during negotiations
This service combines threat detection with data loss prevention. The device agents run on Windows, macOS, and Linux. They control USB ports, printers, emails, and file transfer systems. You check out Digital Guardian DLP with a demo account.
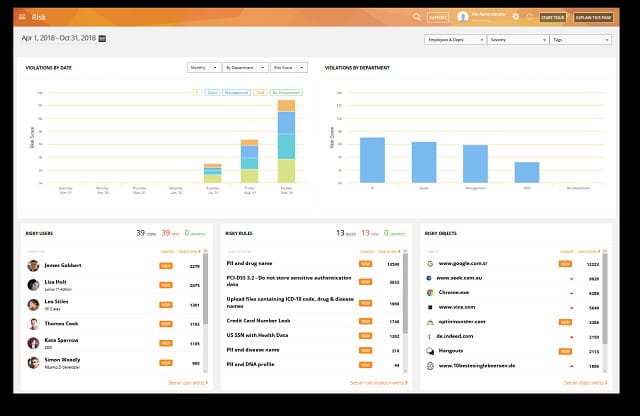
4. Teramind DLP
Teramind DLP is a SaaS platform with onsite modules for monitoring and remediation. This system is offered in versions for the health care industry and the financial sector and a general DLP service. In addition, it provides security policy templates for GDPR, HIPAA, ISO 27001, and PCI DSS.
The endpoint agents scan devices for data locations and then categorize all data instances to focus on sensitive data. Those data instances of interest then get graded further into bands of severity. This discovery service is continuous. The data discoverer will search through files, databases, and cloud storage, and it can find data in pictures and images of documents through the use of OCR.
Teramind DLP performs a risk assessment and an analysis of data access events to help you fine-tune your security policies. The system is able to identify anomalous behavior that could indicate insider threats, account takeover, or intrusion.
Pros:
- Implements threat detection and data loss prevention
- Assess the system to reduce risk
- Preset controls for specific data privacy standards
Cons:
- It can be a little over-automated.
Teramind DLP is available for a 14-day free trial.
L’article McAfee DLP Review & Alternatives est apparu en premier sur Comparitech.


0 Commentaires