A business needs to ensure its data is secure to assure its clients that whatever information they hand over– will be safe from prying eyes regardless of the data types.
Now, these prying eyes could come from anywhere – even from within the network itself; this means there is always a need for some of the seven best cybersecurity risk management solutions we will see in this post.
But, before we do, here is a brief list of the best cybersecurity risk management solutions.
Here is our list of the seven best cybersecurity risk management tools:
- SolarWinds Cybersecurity Risk Management and Assessment Tool FREE TRIAL A feature-filled risk management solution made by one of the leading players in the industry; this solution analyzes and audits access issues across files, folders, and servers to simplify administrators’ jobs. Start a 30-day free trial.
- ZenGRC A cloud-based and on-premise governance, risk, and compliance (GRC) management tool for auditing, managing, and monitoring business infrastructures; it is a solution that is simple to integrate.
- Resolver Risk Management Software A tool for risk management, security, compliance, incident management, and more; it shows all current risks in a single platform and provides data-driven recommendations to resolve them.
- SAI Global’s Digital Manager 360 A highly scalable cloud-based platform that offers flexible, scalable, and configurable modules for risk management and compliance audit across entire enterprise networks.
- LogicManager IT risk management software This tool makes sure organizations’ IT systems and data are secure, accurate, and in compliance with industry standards; it identifies gaps and generates heat maps to visualize any current risks.
- CURA Enterprise Risk Management A cloud-based suite of tools for cybersecurity risk management that is efficient in monitoring risk of loss caused by human error and external events; it has real-time, insightful, and highly interactive dashboards and reports for a better understanding of risks.
- Pathlock A GRC tool that prevents unauthorized access of sensitive data and gives insight into risks that are all controlled from a central dashboard; this is an ideal choice for businesses looking for industry standards compliance.
What constitutes a cybersecurity risk?
The definition of cybersecurity risk is the probability of exposure or loss of sensitive data resulting from a cyber-attack or data breach. It is also defined as the potential loss or damage of the technical infrastructure, technical functionality, or even the reputation of a business due to loss or damage to mission-critical data.
Meanwhile, cybersecurity is the technology, processes, and methods used to protect a business’s intellectual property, customer data, and other confidential information from malicious users – who could be inside or outside the network.
What is a cybersecurity risk management tool?
A cybersecurity risk management solution is a tool used to help businesses determine the level of risk and threats posed against their IT assets and predict the potential outcome should these weak spots be exploited.
These cybersecurity risk management tools also assess, track, monitor, and audit the software and hardware assets’ security health by pinpointing risks posed to them.
The end game is to patch or remove the risks before they can be exploited by malicious users within and beyond the network’s boundaries – regardless of the architecture.
What makes for an excellent cybersecurity management solution?
Some features to look for in a cybersecurity management solution:
- Risk identification – the first and obvious feature is its capabilities to spot vulnerabilities as they arise.
- Vulnerability Assessment (VA) – it should assess the risks and rank them according to seriousness to help prioritize which ones need to be tackled immediately and which ones can be “tolerated” temporarily until all significant issues have been resolved.
- Breach and attack simulation (BAS) keeps up with the latest threats and runs simulated attacks to assess how well the cybersecurity defenses will hold up.
- Insightful dashboards, actionable reports – it needs to present all findings and updates on a dashboard that is informative and easy to understand while also generating regular reports to let stakeholders know about the current security status or use as proof of legal compliance or meeting industry standards.
- Multi-alert system – all concerned personnel should be alerted with multiple methods like email, text, and messages to applications like Slack.
- Scalability – the solution should grow along with the business’ IT landscape and accommodate all changes to its processes and the network’s architecture.
- Price – the solution’s price should have a positive ROI; better yet, it could be free and still perform better than the premium ones.
We have compiled the seven best cybersecurity risk management solutions based on these features and found them worthy of being on this list.
The Seven Best Cybersecurity Risk Management Solutions
Now, let’s have a detailed look at each of the seven best risk management tools.
1. SolarWinds Cybersecurity Risk Management and Assessment Tool (FREE TRIAL)
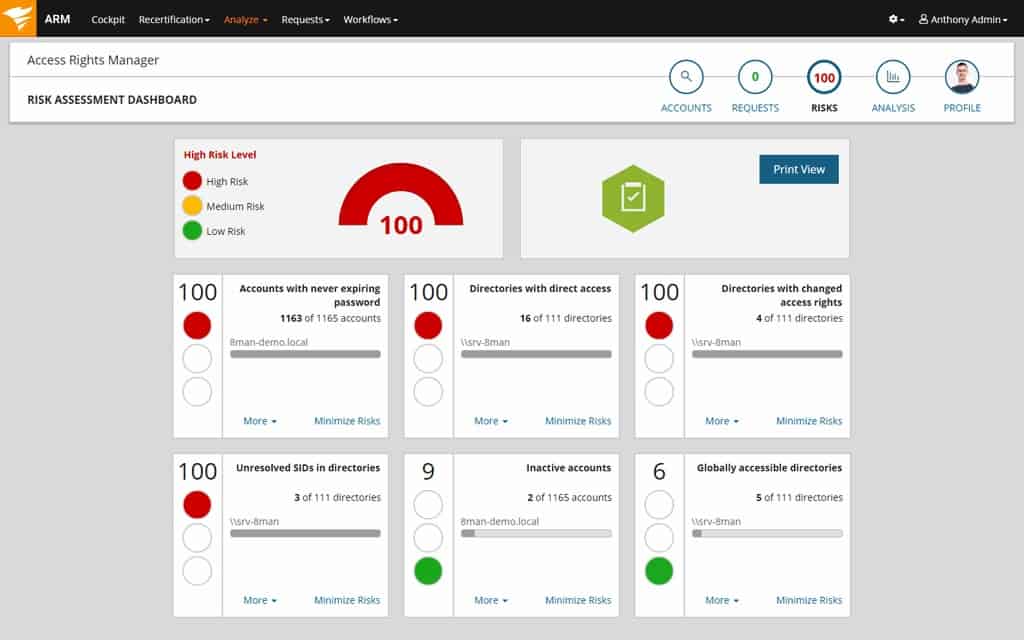
With SolarWinds Cybersecurity Risk Management and Assessment Tool, we have a tool made by one of the leading network and server management solutions makers out there. It analyzes and audits access across files, folders, and servers while proactively detecting data risks based on insecure account configurations and unauthorized accesses.
Here are some more of SolarWinds Cybersecurity Risk Management and Assessment Tool features:
- This is a simple cybersecurity risk management solution for enforcing security policies with automated secure account provisioning; simplifying cybersecurity risk management allows for easy scaling to meet any changes in security and compliance mandates.
- SolarWinds Access Rights Management (ARM) is an add-on feature that allows for the easy reviews of user provisioning and permissions across the domain; it helps address IT risk exposures by reversing access, implementing two-factor authentication, enabling secure rights delegation to prevent risk exploitations before they even occur.
- The tool tracks and monitors user access activity to help minimize the impact of insider threats and mitigates any issues quickly; it offers fast and accurate account provisioning and delegation of access rights management for easier collaboration.
- Administrators stay informed with the help of accurate, detailed, and on-demand reports that outline which users accessed what assets and when.
- ARM helps with compliance by centralizing audit trails across Active Directory, helps facilitate internal and external IT security audits, and supports incident responses.
- It also helps establish cybersecurity risk assessment baselines with detailed reports that can be used for GDPR, PCI DSS, HIPAA, or IT SOX compliance.
You could try SolarWinds Cybersecurity Risk Management and Assessment Tool on a 30-day free trial.
2. ZenGRC
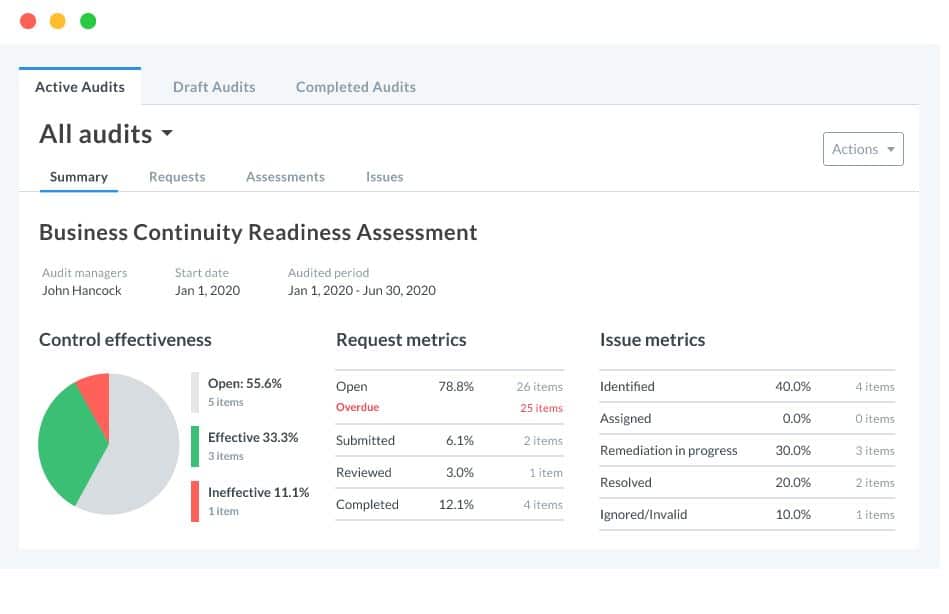
The Reciprocity ZenGRC solution allows security and compliance teams to perform audits and gather evidence using a single integrated tool that reveals information and reports on security risks in a business network.
This flexible solution – it comes in the cloud and on-premises versions –uses customizable control designs and tests to help protect businesses and meet the privacy expectations of their customers.
Some features of ZenGRC:
- ZenGRC is a governance, risk, and compliance (GRC) management platform; it is ideal for businesses of all sizes in any industry looking for help in internal auditing, compliance, and IT security.
- Thanks to automatic and innovative features, simpler and faster audit cycles allow for continuous monitoring with minimum manual intervention required.
- It can evaluate risks across connections, systems, business divisions, and controls using customizable risk calculations that offer multivariable scoring and ranking options based on control frameworks and risk assessment methods like the Secure Controls Framework (SCF), National Institute of Standards and Technology (NIST) standards, and Center for Internet Security Risk Assessment Method (CIS RAM) methods.
- This risk management system can integrate with existing security solutions to evolve current risk and compliance programs; it presents it all in optimized visualizations and in-depth reporting dashboards.
- ZenGRC shows where risk is changing in a network and simplifies audit and compliance management by providing complete overviews of the control environments; it offers easy access to information necessary for program evaluation and continual compliance monitoring to address critical issues at any time.
Book a ZenGRC demo for FREE.
3. Resolver Risk Management Software
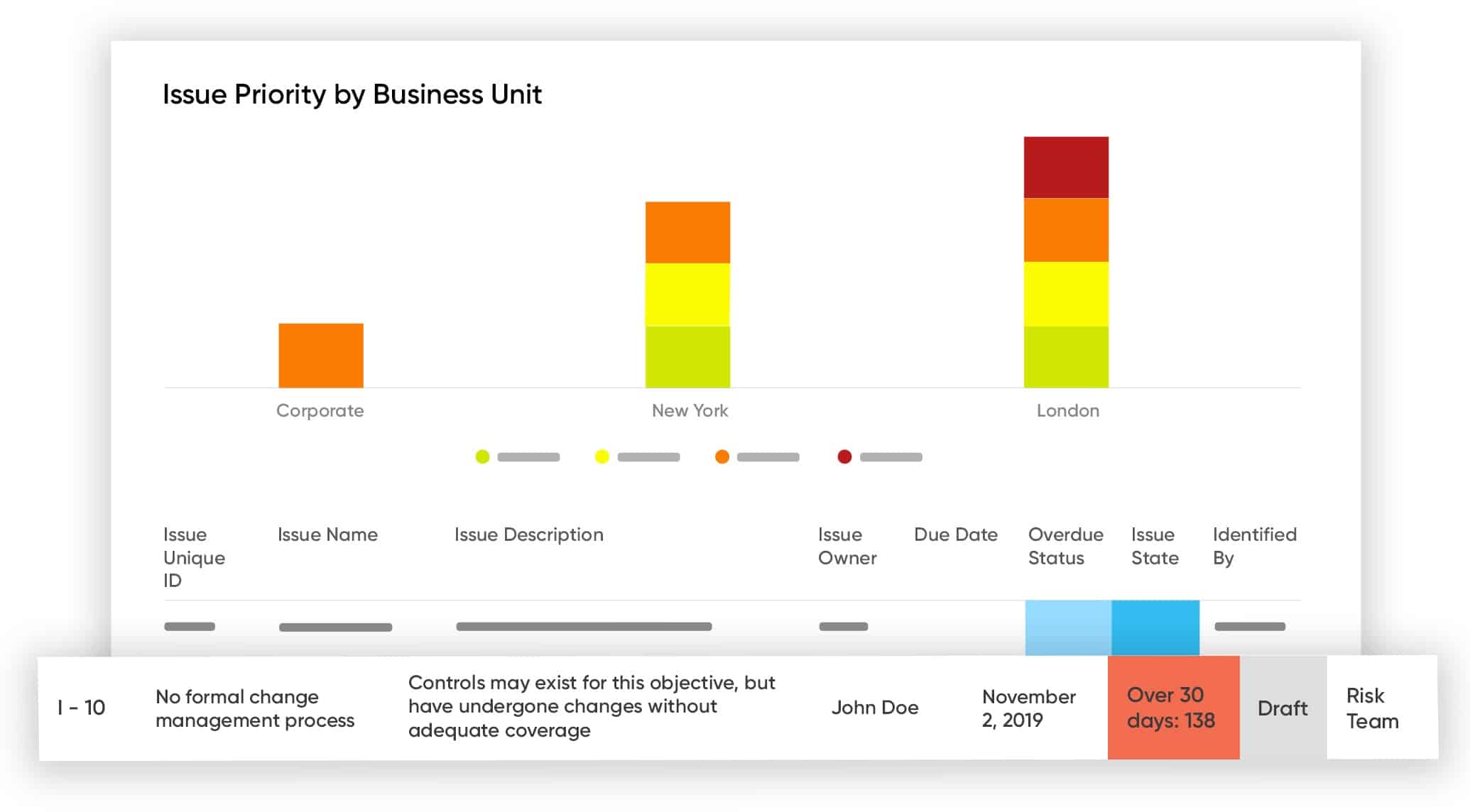
Resolver Risk Management Software offers a suite of tools that cover the risk management and security auditing needs of the entire stack of any network. It is a tool that has won numerous awards and remains an industry favorite. It can also help with other issues like compliance, incident management, and much more.
What makes Resolver stand out, though, is its ability to link risks with incidents – so that assessments of what could happen are related to what did happen.
Looking at some more features of the Resolver Risk Management Software:
- Resolver allows risk managers to view all existing threats from a single platform; this helps them provide data-backed recommendations that can positively impact the bottom line.
- They can also make informed decisions to focus the right resources on the risks that have the most significant impact on the business’ mission-critical processes; the tool’s easy-to-use interface allows companies to increase adoption across their network while also making it easy to work with the solution.
- Resolver allows for accurate and up-to-date insights into the full scope of covered digital assets thanks to its real-time reports that can be made accessible to stakeholders.
- They can quickly evaluate their risks using step-by-step guidance and documentation for controlling and mitigating threats while archiving the risk events on portals that concerned stakeholders can access to help with investigations.
- It is a highly configurable solution that requires no code and uses drag-and-drop configuration to create custom security frameworks to meet any network architecture or business process workflows; the workflow and orchestration engine allows for easy definition of scheduled persons, alerts, task management, and more.
Request a Resolver Risk Management Software demo for FREE.
4. SAI Global’s Digital Manager 360
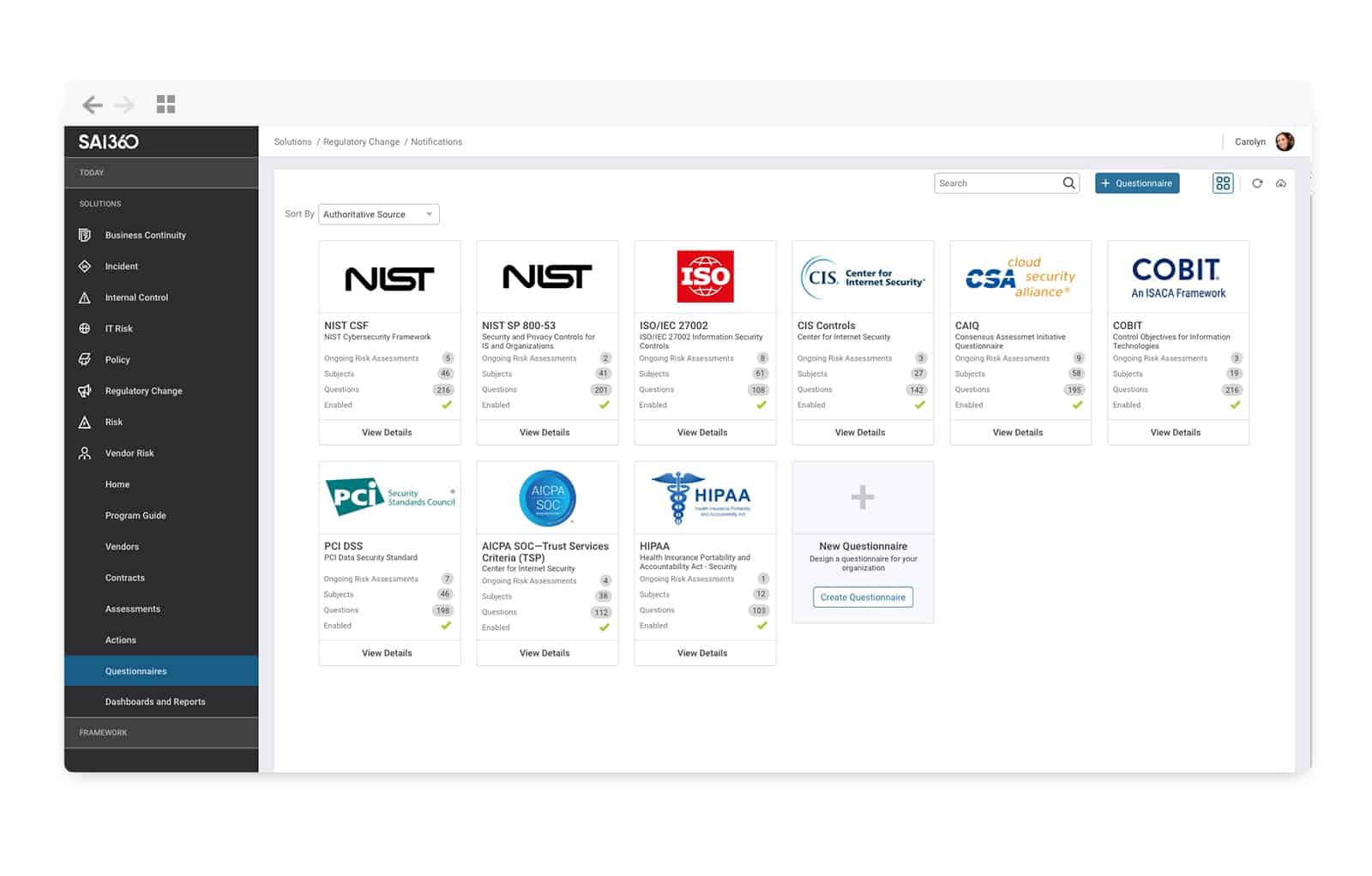
SAI Global’s Digital Manager 360 (acquired by Intertek) enables cybersecurity taskforces to manage digital risks and compliances across enterprises and extended networks. They can use the tool to assess and monitor adherence to security frameworks across the web and cross over into third-party relationships.
This GRC platform contains flexible, scalable, and configurable modules for a better insight into risk management. Some of the modules include IT Vendor Risk Management, Digital Enterprise Risk Management, Business Continuity Management, and Digital Incident Management – all of which can be used to cover every angle of a business’s IT assets and mission-critical processes.
More features from SAI Global’s Digital Manager 360:
- It provides a single, scalable cloud-based platform with proven capabilities to help reduce digital risks – straight out of the box – and the versatility of installing it on-premise.
- Minimal configuration is needed to gain complete visibility into IT risks and threats; it hits the ground running within minutes of deployment thanks to dozens of out-of-the-box integrations – which can be extended by configuring additional custom integrations.
- Businesses can cut IT security costs because it integrates well into any current IT GRC management lifecycles without costly configurations or third-party solutions; the platform improves consistency by automating tasks which helps in avoiding errors or security lapses.
- Digital Manager 360 provides a comprehensive library of over a thousand legal standard frameworks – with over 100,000 control sets – that help follow guidelines set out about industry standards and authorities.
- Administrators stay on top of issues thanks to a centralized view of risks that give insights into the whole stack of the IT infrastructure; they remain informed thanks to one-click reports and dashboards that authorized stakeholders, and decision-makers can also access.
Try Digital Manager 360 – request a demo for FREE.
5. LogicManager IT risk management software
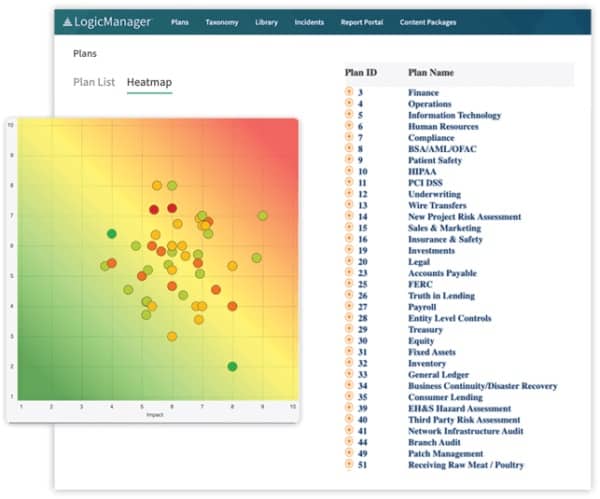
Equipped with LogicManager IT risk management software, administrators can ensure their organization’s IT systems and data are secure, accurate, and meet the industry’s ever-evolving privacy and security compliance requirements.
They can also house all their compliance information in one centralized repository, complete with ready-made libraries of risks, standards, and regulations.
Let’s have a look at some features of the LogicManager IT risk management software:
- This solution helps prioritize critical resources and identify gaps in IT asset protection with intuitive and objective risk assessments; it is easy to use, and master and the reporting options provide a lot of flexibility.
- LogicManager is versatile – it offers a wide variety of solutions with features for risk management, vendor management, cybersecurity management, financial compliance, and much more.
- One forte of this tool is its reporting capabilities – it offers highly configurable and engaging reports to be used by internal stakeholders and decision-makers that can also access interactive dashboards; these reports can also be used to prove compliance to regulators or presented to boards and senior management.
- Users can generate heat maps for in-depth insights into common risks, the effectiveness of the controls in place, and assign actions based on analysis; they can see protocols that are mapped across frameworks which, in turn, help identify risks that are specific to certain parts of the business with the help of intuitive reports.
- LogicManager helps oversee risk monitoring activities – it ensures correct and efficient control placement, testing, metrics collection, and incident handling using automated workflows.
- Its historical data helps with identifying trends, trail audits, and events management over selected periods.
Try Logicmanager IT risk management software – request a FREE demo.
6. CURA Enterprise Risk Management
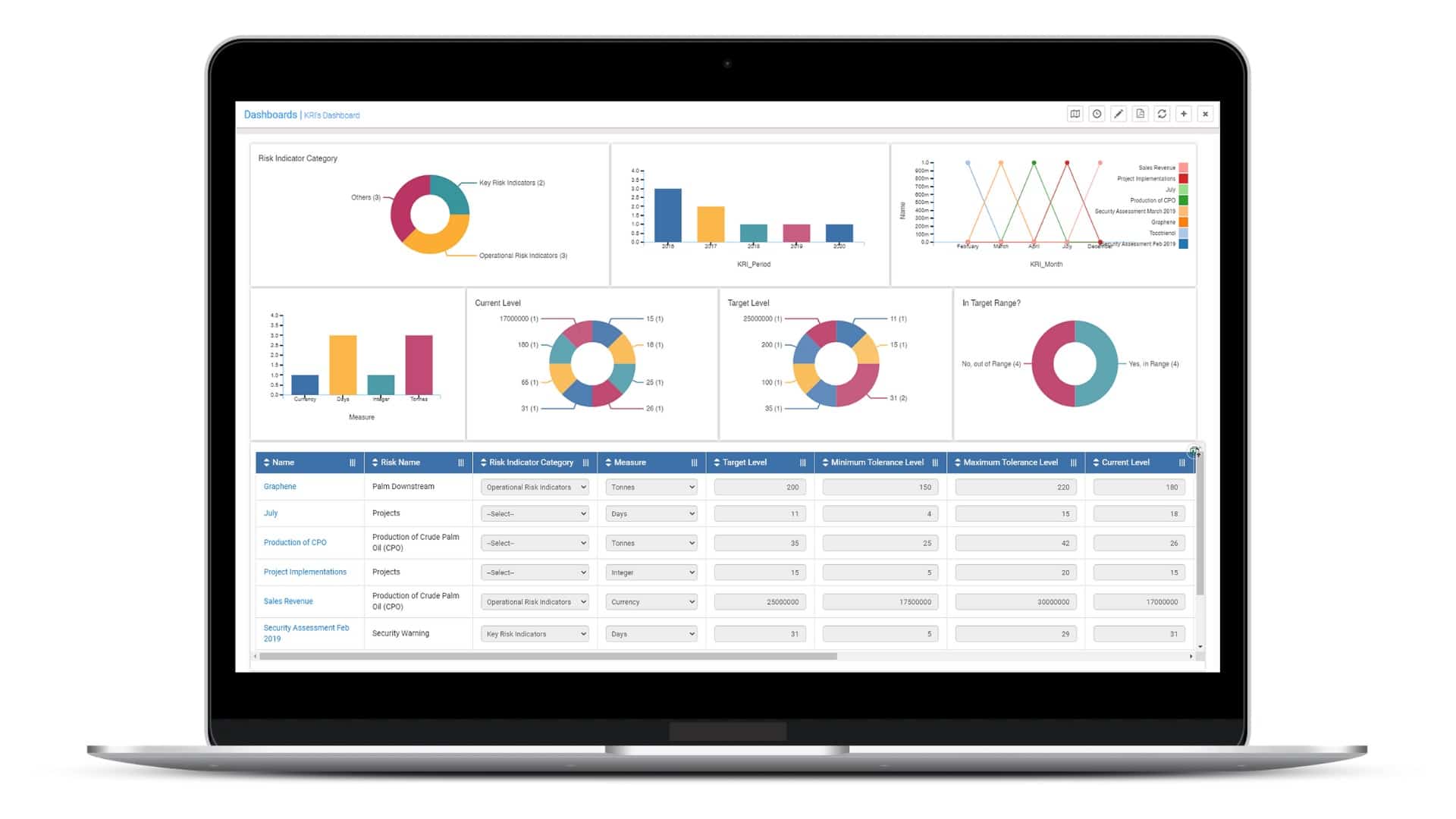
CURA Enterprise Risk Management is a web-based suite of tools for managing enterprise or project risks, incidents, business continuity, compliance, operational risks, and information security.
It enables businesses to effectively and efficiently manage their cybersecurity risks and prevent loss of data resulting from human error factors and other external events.
There are more features of the CURA Enterprise Risk Management, including:
- Visual and interactive dashboards, surveys, a self-assessment portal, notifications, workflow management, multiple-deployment capabilities, and custom configurations are some of the primary features of CURA.
- The platform allows for tracking of information via libraries, data parameters, and calculation metrics; it helps create automated, repeatable processes – that include risk assessment and analysis – and the implementation of risk controls.
- Meanwhile, its applications – built on a unified platform – can be integrated with third-party dashboards and reporting tools to create a GRC system across the full scope of the enterprise.
- It has solutions available as standalone applications or add-on modules to a more comprehensive implementation based on the CURA Enterprise GRC Platform.
- It offers real-time visibility through interactive dashboards and reports and alerts users and managers to tasks, actions, and escalations regarding risk resolutions and controls testing.
Request a CURA Enterprise Risk Management demo for FREE.
7. Pathlock
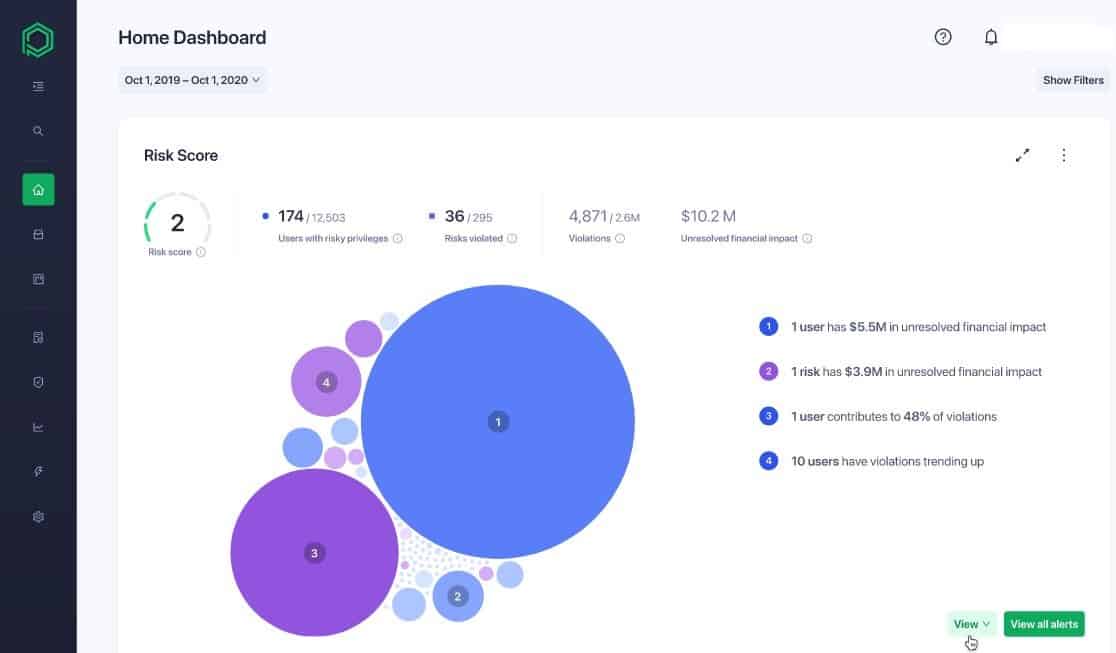
Pathlock is a governance, risk, and compliance tool for finance, IT, and other mission-critical business processes.
It also monitors user activity to spot out-of-policy transactional activity and prevent unauthorized access to sensitive data – with protection at the database or application level and the field level.
More Pathlock features:
- With Pathlock, administrators can see access violations and understand the business impact of their approval decisions; they can track breaches and incidents to ensure that corrective action is taken immediately.
- It demonstrates risk reduction over time using a central dashboard; it provides stakeholders with visibility into the actual bottom-line cost of risk and its impact on the business processes; and with this in mind, the tool also prioritizes compliance efforts based on the dollar-value effect of each risk.
- It is the tool to use when trying to achieve compliance to the likes of SOX, HIPAA, PCI, and GDPR – as it helps identify the relevant data that needs to be secured so administrators can put the proper measures in place to restrict access.
Request a Pathlock demo for FREE.
What steps are involved in cybersecurity risk management?
Ok; now that we have seen the solutions, let’s have a brief look at the five significant steps involved in cybersecurity risk management:
- Taking stock of valuable digital assets – this helps with defining the scope of the risk management campaign.
- Identifying risks, past and present – laying out any and everything that could happen to all aspects (storage, communication, sharing, connectivity, processing, etc.) of the assets from both within and beyond the network’s boundaries.
- Planning for an attack – testing attacks using known and unknown methods to see the impacts and worse-case scenarios; then creating controls for the prevention of each one of these attacks.
- Reviewing controls – time should be spent studying each management to gauge efficiency and accuracy before being accepted as a permanent solution.
- Creating cybersecurity awareness – this step stops the problems from occurring in the first place. A security-aware workforce addresses the cybersecurity risk issue at the root level by totally avoiding behaviors that create them, to begin with.
Advantages of risk management and implementing cybersecurity risk management tools
Maintaining an efficient security infrastructure creates the ability to respond quickly in the face of attacks. In addition, these tools help in quickly identifying threats, assessing how dangerous they are, and improving mitigation times and efforts. And finally, their capability to prioritize the risks by threat levels ensures resources are correctly allocated.
But, there’s more:
- Cost-saving – cybersecurity incidents costly affairs to clean up. Also, in case of successful attacks, the damage can linger, causing issues for a long time. In some cases, the businesses never recover from a data loss.
- More security health insight – security audits provide an opportunity to learn how well a business handles its security and find out where improvement can be made.
- Compliance – businesses can make sure they meet all compliance requirements and governmental standards. This increases trust with their clients and even gives them a competitive edge over similar enterprises.
- Benefits for employees – staff members will be more tech-savvy and especially cybersecurity aware and will help secure the business’ data. In addition, regular cybersecurity awareness workshops and IT training should be part of a business
A business gains by choosing to deploy one of the seven best cybersecurity risk management solutions we have just seen. And to be honest, there is no downside to these tools. What do you think? Let us know; leave us a comment below.
L’article 7 Best Cybersecurity Risk Management Tools est apparu en premier sur Comparitech.

0 Commentaires