Overview of Datadog Cloud SIEM
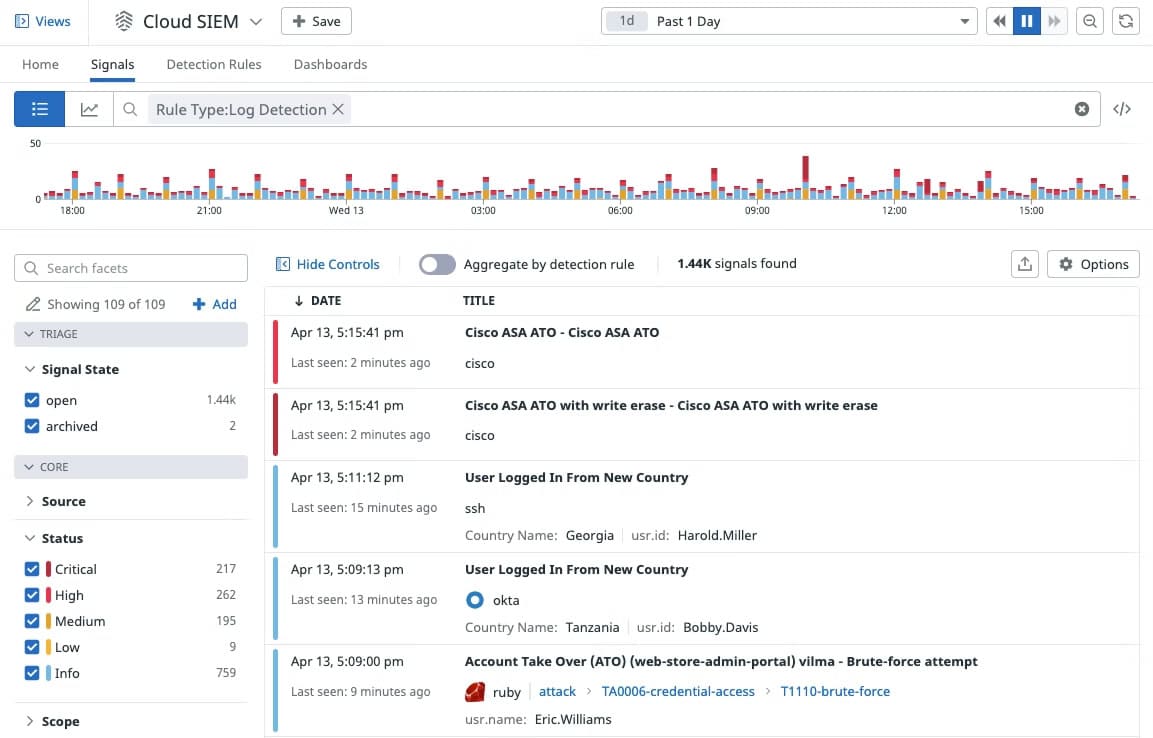
Datadog entered the SIEM application market with the launch of Datadog Cloud SIEM in 2020. Datadog Cloud SIEM (Security Information and Event Management) is a SaaS-based solution that provides end-to-end security coverage of dynamic, distributed systems. It is part of the Datadog Cloud Security Platform and is designed to provide a single centralized platform for the collection, monitoring, and management of security-related events and log data from across the enterprise. This enables security teams to identify and respond to suspicious behavior patterns more effectively than possible by looking at data from individual systems.
With Datadog Cloud SIEM, you can analyze operational and security logs in real-time regardless of their volume. Developers, security, and operations teams can leverage detailed observability data to accelerate security investigations in a single, unified platform.
Key features and capabilities include:
- Observability and security See all of your security data in one place, and correlate them with runtime events, application and service logs, and more. Development, security, and operations teams can access the same observability data and drive security investigations in a single, unified platform.
- Out-of-the-box dashboards The Security Overview dashboard allows you to have a high-level view of your security posture. The IP Investigation and User Investigation dashboards enable users to correlate specific IP addresses and users with security signals, events, and logs, so they can quickly hone in on malicious activity patterns.
- Out-of-the-box threat detection rules Datadog Cloud SIEM comes equipped with out-of-the-box threat detection rules that don’t require a query language for widespread attacker techniques and misconfigurations that are mapped to the MITRE ATT&CK framework.
- Built-in vendor-backed security integrations Built-in security integrations with AWS CloudTrail, Okta, G Suite, and more enable users to ingest additional security data in minutes, which provides deeper context and helps accelerate investigations.
A free personalized demo and a free 14-day-trial with full access to all the features are available on request. After that, the software is generally sold through monthly subscription plans based on hosts, events, or logs.
Overview of QRadar SIEM
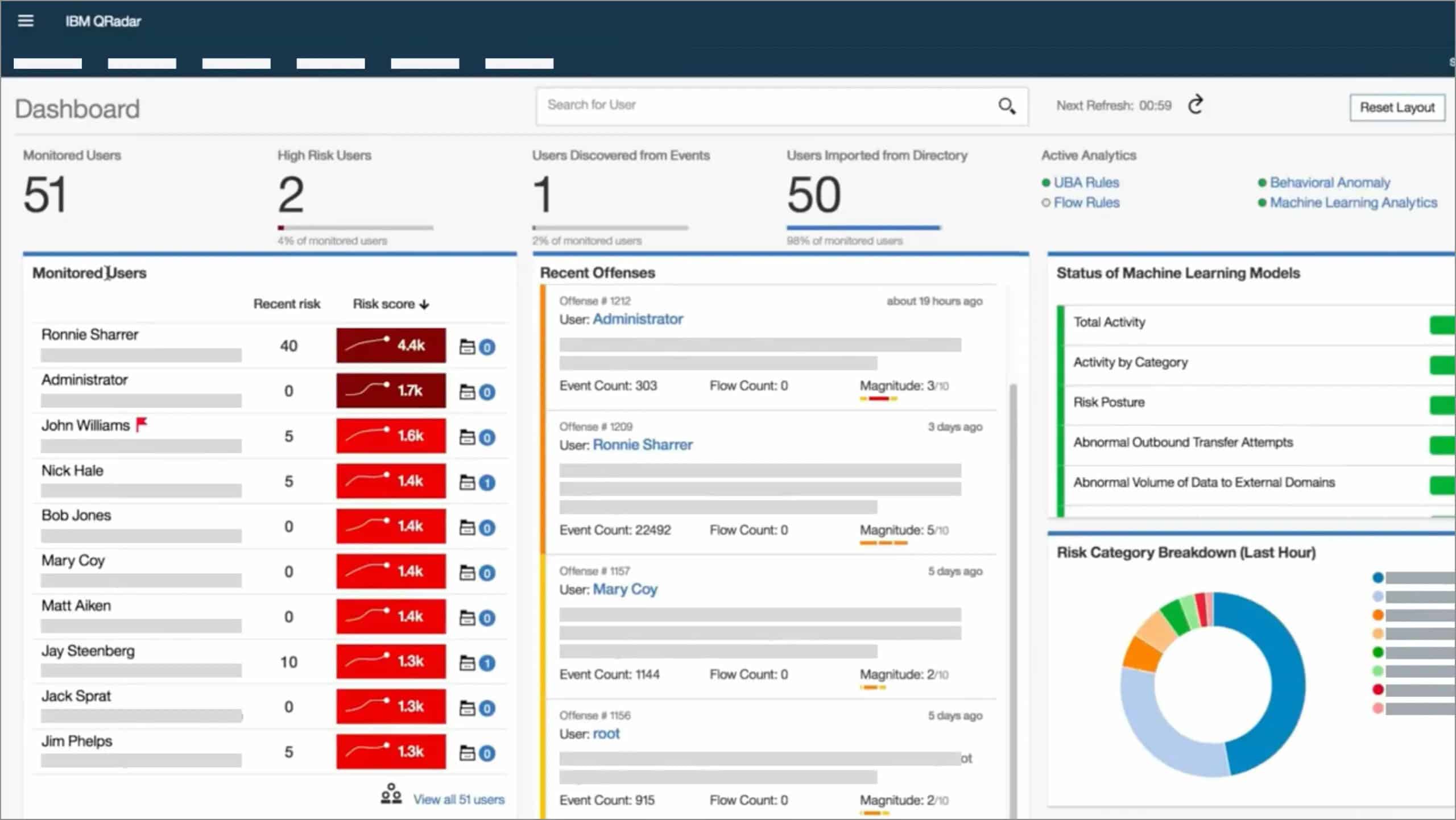
IBM Security QRadar SIEM is a mature market-leading SIEM solution that helps organizations defend against modern security threats. The solution applies automated, intelligent analytics to a vast amount of collected security data to provide security analysts with actionable insight into the most critical threats. QRadar SIEM provides security teams with centralized visibility into enterprise-wide security data and identifies suspicious behaviors based on correlation rules once a security threat is detected. This solution is the core module of the QRadar Security Intelligence Platform. The solution brings together log management, network analysis, user and entity behavior analytics (UEBA), threat intelligence, and AI-powered investigations into a single solution—integrated with IBM Security SOAR for incident response—all with comprehensive visibility across on-premises, cloud, and hybrid environments.
IBM Security QRadar has been named as a Leader in the 2021 Gartner Magic Quadrant for SIEM for the 12th consecutive year.
Key features and capabilities include:
- Intelligent insights across environments Provides visibility and applies context to on-prem and cloud-based resources.
- Built-in analytics Analyzes network, endpoint, asset, user, risk, and threat data to uncover known and unknown threats.
- Correlation of related activities Identifies and tracks associated activities throughout the kill chain.
- Parsing and normalization of logs Automatically makes sense of data from disparate sources.
- Threat intelligence Supports threat intelligence from IBM Security X-Force and STIX/TAXII.
- Out-of-the-box integration with multiple vendors Supports integration with over 450 solutions, including APIs and an SDK to speed data ingestion.
- Flexible deployment options QRadar SIEM is available for on-prem and cloud environments and can be delivered as hardware, software, or VM.
A free 30-day trial of the Community Edition is available on request. Community Edition is a fully-featured free version of QRadar that is low memory, low EPS, and includes a perpetual license. It is limited to 50 events per second and 5,000 network flows a minute.
Datadog Cloud SIEM vs QRadar SIEM: How They Compare
Deployment Model
Just as the name implies, Datadog Cloud SIEM is a cloud-based application for cloud-native environments; which means there are no on-premise system requirements and no installation hassles other than the usual sign-up process using an internet-connected device with a supported browser. However, you’ll be required to install local agents specific to the device or service you wish to monitor for the most part. This deployment makes it ideal for organizations that don’t want to burden themselves with any resource-intensive on-premise SIEM solution.
On the other hand, QRadar SIEM offers a flexible deployment model as stated below:
- SaaS-based service QRadar SIEM is available as a SaaS offering which comes with the advantage of the IBM team being on your side to run and care for the infrastructure. This is great for organizations that don’t want to burden themselves with the implementation of patches or updates
- Hardware and virtual appliance QRadar SIEM is available as both hardware and virtual appliances that can be deployed on-premises or on the cloud of your choice. This is great for organizations that desire to have precise control over their IT infrastructure.
- Managed service IBM Security X-Force provides offensive and defensive security services that are underpinned by threat research, intelligence, remediation, and managed services. This service takes the burden off organizations, so they can focus on the business.
Data Collection and Analytics
Datadog Cloud SIEM collects logs from many different sources into Datadog. All ingested logs are first parsed and normalized (reformatted) for consistency, easy correlation, and analysis. This helps to uncover malicious activities on the network, preventing bad actors from concealing their tracks. Once logs are collected, ingested, and processed, they are available in Log Explorer. Log Explorer is where you can search, enrich, and view alerts on your logs. This makes it easy to search and filter log data across your entire infrastructure for threat detection and investigation.
The core functionality of QRadar SIEM is focused on the event and flow data collection. Event data represents events that occur at a point in time in the user’s environment such as user logins, email, VPN connections, firewall denies proxy connections and any other events that you might want to log in to your device logs. Flow data is network activity information or session information between two hosts on a network, which QRadar translates into flow records.
QRadar normalizes raw data into IP addresses, ports, byte and packet counts, and other information into flow records, which effectively represents a session between two hosts. Data that is collected and processed by QRadar is available to users for searches, analysis, reporting, and alerts or offense investigation to identify various security risks in your network. AI can be used to generate deeper insights during investigations, and quickly build custom applications to address security concerns.
Incident/Threat Detection and Mitigation
Datadog detects threats based on rules and creates a security signal. Datadog provides out-of-the-box rules for widespread attacker techniques, mapped to the MITRE ATT&CK framework. Detection rules take full advantage of Datadog’s “Logging without Limits”, which lets you customize what logs you want to index while still ingesting, processing, and archiving everything. Rules apply to the full stream of ingested, parsed, and enriched logs so that you can maximize detection coverage without any of the traditionally associated performance or cost concerns of indexing all of your log data.
QRadar contains a variety of anomaly detection capabilities to identify changes in behavior that could be indicators of an unknown threat. And the unique ability of QRadar to monitor and analyze Layer 7 application traffic enables it to more accurately identify incidents/threats that other solutions may miss. QRadar ships with numerous anomaly and behavioral detection rules as default settings, security teams can also create their own rules, tailor anomaly detection settings and download over pre-built 160 apps from the IBM Security App Exchange to augment their deployment.
Unlike Datadog, QRadar SIEM integrates with IBM security orchestration, automation, and response (SOAR) solutions for automated and accelerated incident response and remediation, user and entity behavior analytics (UEBA), network flow insights, and artificial intelligence (AI) to accelerate detection. With SOAR capabilities enabled, security teams can become more efficient, and free up time and resources for more demanding tasks. Similarly, UEBA allows security teams to gain greater visibility into insider threats, uncover anomalous behavior, easily identify risky users, and quickly generate actionable insights by applying machine learning and behavioral analytics to QRadar security data.
Notifications and Alerts
Datadog’s approach to alerts and notifications is based on machine learning (ML), which it calls Watchdog. Watchdog uses ML techniques to identify problems in your infrastructure, applications efficiency, and services, and flag anomalies. Alerts in Datadog are called Monitors. Users can receive alerts using Pagerduty, Slack, and email. These can be based on nearly any metric that Datadog can capture. As a result, every alert is specific, actionable, and contextual—even in large and temporary environments. This unique approach to alerts and notifications makes Datadog stand out and helps to minimize downtime and prevent alert fatigue.
QRadar system notifications are displayed on the QRadar dashboard or in the notification window when unexpected system behavior occurs. These generated notifications can be used to monitor the status and health of your system. As threats are discovered, the QRadar solution aggregates related security events into single, prioritized alerts known as “offenses.” Offenses are automatically prioritized based on both the severity of the threat and the criticality of the assets involved. Alerts and notifications can be sent via email (custom templates allowed), Twilio SMS service, and Telegram. Slack service, and more.
Compliance and Integration
Instead of generating the usual out-of-the-box reports that most network admins expect, Datadog’s approach to reporting aims to make metrics easily searchable, and it does excellently. Cloud SIEM is fully integrated with all of Datadog’s application and infrastructure monitoring products, which allows users to seamlessly pivot from a potential threat to associated monitoring data to quickly triage security alerts. Datadog’s 500+ integrations let you collect metrics, logs, and traces from your entire stack
as well as from your security tools, giving you end-to-end visibility into your environment. Datadog integration with Slack and PagerDuty allows you to automatically loop in relevant teams when a high-severity rule detects a threat. You can also export security signals to collaboration tools like JIRA or ServiceNow.
The QRadar SIEM system includes a library of pre-written report formats. However, it is also possible for customers to write their report layouts within the system. QRadar SIEM provides hundreds of pre-built reports and rule templates that can help organizations more easily address industry compliance requirements. Default-setting compliance packages are available for organizations to meet compliance requirements for GDPR, the Federal Information Security Management Act (FISMA), Sarbanes-Oxley (SOX), HIPAA, ISO 27001, PCI DSS, and more.
The QRadar SIEM solution includes more than 450 pre-built Device Support Modules (DSMs), which provide default setting integrations with other security investments. Customers can simply point logs to QRadar, and the solution can automatically detect the log source type and apply the correct DSM to parse and normalize the log data. These packages are included free of charge with a QRadar license and are available in the IBM Security App Exchange.
Licensing and Price Plans
Datadog Cloud SIEM pricing model is per GB of analyzed logs, per month billed annually or on-demand. An analyzed log is a text-based record of activity generated by an operating system, an application, or other sources analyzed to detect potential security threats. Datadog charges for analyzed logs based on the total number of gigabytes ingested and analyzed by the Datadog Cloud SIEM service.
QRadar SIEM pricing is dependent on your needs, how you choose to deploy, and which licensing model best fits your needs. Pricing options include the Usage model based on Events per Second (EPS) determined by the number of log events ingested per second, and Flows per Minute (FPM) determined by the network communications per minute. Licensing with this metric is available for hardware appliances, virtual appliances, and SaaS model environments. Licenses are generally available as SaaS, software, or managed service. Subscription or perpetual licensing models are available for on-premise offering; while only a subscription model is available for SaaS deployment.
Choosing Between Datadog Cloud SIEM and QRadar SIEM
Although Datadog is a newcomer in the SIEM market, it has no doubt distinguished itself over the years in the observability space. It is therefore well positioned to meet the security needs of its existing customers and organizations that don’t have dedicated IT personnel to keep tabs on the infrastructure at a granular level. Datadog customers can leverage Datadog Cloud SIEM to aggregate and better analyze events inside their cloud-native applications without looking to third-party SIEM tools. This provides an advantage in terms of cost, implementation, and integration.
Datadog’s ability to support and integrate with more than 500 technologies makes it more versatile and adapted to many different functions, provides deeper context during investigations, and lets you cast a wider net to catch possible security issues. However, the lack of SOAR and UEBA capabilities makes it less effective in tackling modern security challenges.
QRadar SIEM is a mature and award-winning SIEM application managed by one of the foremost technology corporations in the world—IBM. QRadar’s flexible deployment option gives organizations the flexibility to choose the deployment model most suitable for them. QRadar’s ability to leverage IBM’s SOAR and UEBA capabilities puts it in the class of next-generation SIEMs which are better positioned to defend against modern security challenges. However, contrary to standard practice, this is a separate module on the QRadar Security Intelligence Platform. Customers that want to use these features will have to pay more, thereby increasing the total cost of ownership.
Deciding between Datadog and QRadar SIEM shouldn’t be about which is better, but about which best meets your business and security needs.
Key factors to consider include:
- Is the SIEM solution capable of meeting your organization’s security and compliance requirements?
- How much native support does the SIEM tool provide for relevant log sources?
- Does the SIEM solution possess the capabilities of next-generation SIEM functionalities such as SOAR and UEBA?
- What is the total cost of ownership, is vendor support available in your region, and to what extent?
L’article Datadog Cloud SIEM vs QRadar SIEM est apparu en premier sur Comparitech.

0 Commentaires