Phishing attacks use social engineering in emails and messages to persuade people to hand over information such as passwords or financial information, or to get them to perform certain tasks such as downloading malware or completing a wire transfer. Phishing schemes continue to become more sophisticated with targeted attacks (spear phishing) posing a threat to many businesses.
While spam filters catch many phishing emails, newer and more sophisticated ones get through. There is evidence that most people are aware of the existence of phishing attacks. Indeed, many companies provide training and simulations to teach employees how to spot malicious emails and messages.
That said, scammers still have success with this form of cyber attack and its use remains prevalent. Plus, cybercriminals are changing tactics to get around the anti-phishing measures in place.
Here’s a rundown of phishing statistics and facts for 2022:
1. Phishing attacks are still extremely common
According to APWG’s Phishing Activity Trends Report for Q4 2021 phishing attacks hit an all-time high in 2021. With more than 300,000 attacks recorded in December, these incidents have become more than three times as common as they were less than two years ago.
The 2021 report also highlights a growing trend for phishing attacks levied against cryptocurrency companies. These now account for 6.5 percent of all attacks. This illustrates how cybercriminal gangs are seeking to evolve their pursuits to victimize the most lucrative targets possible.
In addition, the number of brands being targeted in phishing attacks actually declined in December after months of growth. However, there were still over 500 atttacks, which shows how cybercriminals are extending the scope of their attempts to lure in victims.
2. Loaders are the most popular attack avenue
Cofense’s Q1 2022 Phishing Review found that loaders have leapfrogged information stealers and keyloggers to become the favored tools for phishing. According to the study, loaders account for well over half of all attacks on their own. Compare this with the beginning of 2019, when almost 74 percent of phishing attacks involved credential phishing (stealing usernames and passwords).
These attacks can be difficult to stop as the emails typically show no signs of being malicious. Many originate from hijacked business email accounts, a tactic known as business email compromise or BEC. Plus, attackers often go a step further and host fake login pages (phishing sites) on Microsoft Azure custom domains. For example, these could end in “windows.net,” making the site seem legitimate and the scam even more difficult to spot.
In Cofense’s Q3 2021 Phishing Review the company reported that “93% of modern breaches involve a phishing attack”. This reveals just how prevalent the problem of phishing with keyloggers and information stealers remains.
Unfortunately, Cofense is predicting more of the same next year, with new subscription-based malware downloaders expected to join the phishing threat landscape.
3. Spear phishing emails are the most popular targeted attack vector
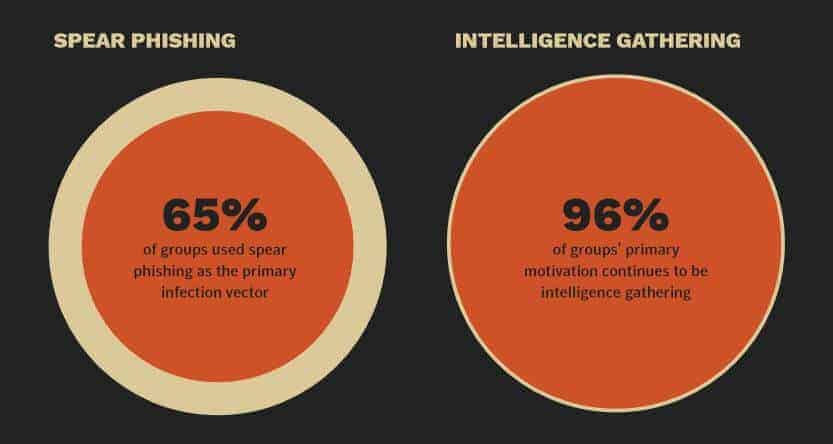
Symanetc’s Internet Security Threat Report 2019 shows spear-phishing emails are used by almost two-thirds (65 percent) of all known groups carrying out targeted cyber attacks. The report also tells us that 96 percent of targeted attacks are carried out for the purpose of intelligence gathering.
In its 2020 Threat Landscape Trends paper, Symatec reported an enormous spike in COVID-related emails being used to lure in victims. This shows how spear-phishing evolves over time and may use new topics to target consumers.
The same report reveals that business email compromise scams targeted around 31,000 organizations in Q1 of 2020 alone.
4. Human intelligence is the best defense against phishing attacks
In its 2019 report, Cofense reiterates the importance of awareness training in thwarting phishing attempts. It cites an example in which a phishing attack on a major healthcare company was stopped within just 19 minutes. Users reported receiving suspicious emails and the security operations center was able to take swift action.
5. Phishing attacks are getting more sophisticated
Cofense also sheds light on the types of attacks taking place. Because users trust links to things like OfficeMacro, cloud sites, and infected webpages.
In 2022, this trend continued with abuse of trusted platforms like SharePoint, Amazon AWS, Google, Adobe, DigitalOceanSpaces, Weebly, Backblaze B2, and WeTransfer all reportedly increasing.
Cofense also confirmed Symantec’s findings regarding attackers’ ability to quickly capitalize on current events. They corroborated that in 2020, there was an influx of COVID-19 related phishing, often claiming to provide financial assistance for impacted citizens.
6. Attackers are using tricks such as Zombie Phish and shortened URLs
A popular trick used by attackers is the Zombie Phish. As explained in the 2019 Cofense report, this involves attackers taking over an email account and responding to an old email conversation with a phishing link. The sender and subject is familiar to the recipient, helping to disguise the email as genuine.
Another strategy that’s being seen more in phishing emails is the use of shortened URLs provided by link shortening services such as Bitly. These links are rarely blocked by URL content filters as they don’t reveal the true destination of the link. Plus, users who are vigilant about suspect domain names might be less likely to identify a shortened link as malicious.
However, in its 2021 report, Cofense is quick to remind consumers that .com domains still account for 50 percent of credential phishing attacks. As a result, it remains critical to be highly vigilant when visiting Top Level Domains of this kind.
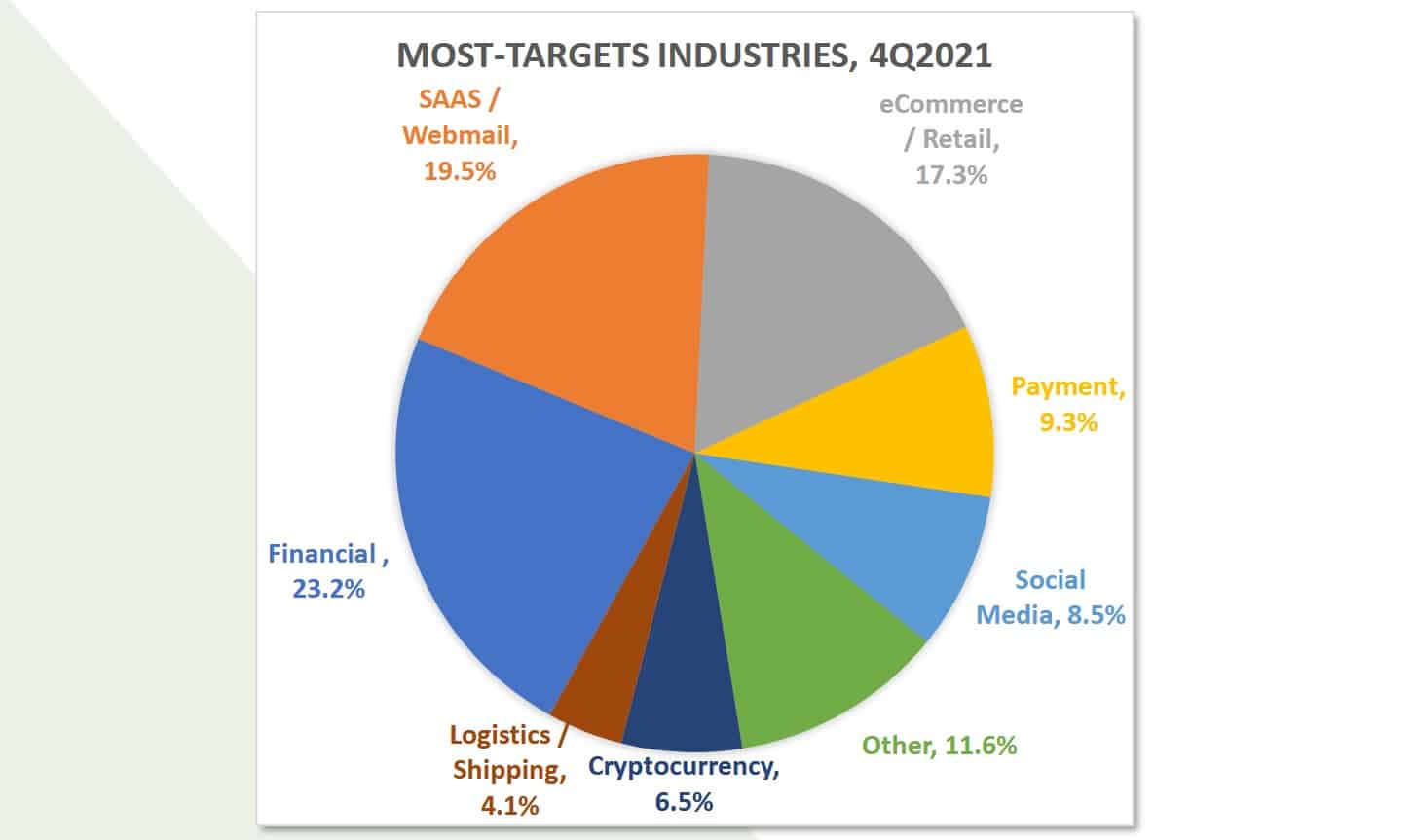
7. Financial services are the biggest targets
Although credential phishing is no longer the most popular tactic, it remains far more common than we’d like. The APWG report sheds some light on the types of credentials attackers are after.
There’s been a marked change lately. Attackers are now targeting financial services like banking platforms and crypto exchanges the most, with webmail and ecommerce falling to second and third place, respectively.
8. Smaller organizations see a higher rate of malicious emails
Symantec combines numbers for various types of email threats, including phishing, email malware, and spam, and reports that employees in smaller organizations are more likely to receive those types of threats. For example, for an organization with 1–250 employees, roughly one in 323 emails will be malicious. For an organization of 1001–1500 employees, the rate is far lower with one in 823 emails being malicious.
9. Malicious emails are most likely to hit mining companies
Symantec also breaks down malicious email rates by industry. Mining tops the list with one in 258 emails being malicious. This is closely followed by agriculture, forestry, and fishing (one in 302) and public administration (also one in 302). Manufacturing, wholesale trade, and construction follow as the next most heavily targeted industries.
10. Australian companies were most likely to fall victim
According to Proofpoint’s 2022 State of the Phish, 92 percent of Australian organizations suffered a successful attack last year, which is a 53 percent increase over last year. Meanwhile, less than 60 percent of Spanish organizations experienced phishing or ransomware campaigns.
11. Many data breaches stem from phishing attacks
Verizon’s 2020 Data Breach Investigation Report found that phishing is one of the top threat action varieties in data breaches, with 22 percent of data breaches involving phishing. In its 2021 report, the prevalence of social engineering attacks, including phishing, continued on an upward trend accounting for around 30% of attacks.
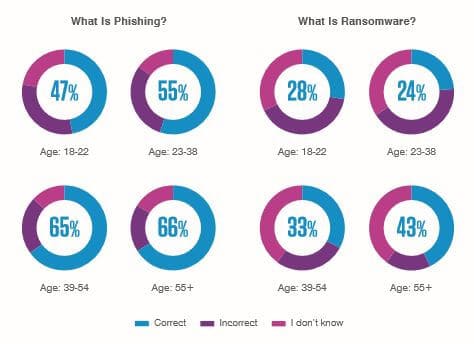
12. Knowledge of phishing terms varies among generations
Proofpoint provides interesting information about employee awareness of phishing terms. Out of four age groups, baby boomers (aged 55+) were most likely to recognize the terms “phishing” and “ransomware.”
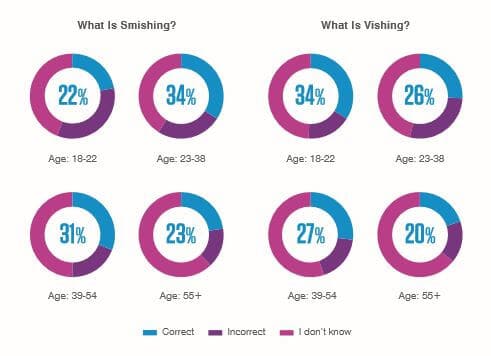
However, when it came to the terms “smishing” and “vishing,” the older generation was the least likely to know the definitions.
13. Sextortion is a common tactic in phishing campaigns
Cofense reveals that phishing schemes based on sextortion scams represent a growing issue. These emails are typically generic, but attackers prey on human emotion by using fear and panic to encourage victims to submit a ransom payment. Scammers usually request payment in bitcoin or another cryptocurrency to help avoid detection.
In the first six months of 2019, Cofense found more than seven million email addresses were impacted by sextortion. Cofense also found that $1.5 million had been sent as bitcoin payments to accounts (bitcoin wallets) known to be associated with sextortion schemes.
There were even reports at the end of 2019 of a sextortion botnet sending up to 30,000 emails an hour.
14. Popular apps continue to be used to distribute malware
The Q2 2021 McAfee Labs Threat Report found that use of Powershell and Microsoft Office as a malware-delivery method declined significantly following its huge growth in Q4 of 2020. Instead, attackers now rely on public facing apps to deliver their payloads for them. .
In its October 2021 report, McAfee Labs reports that of all the cloud threats it analyzes, spam showed the highest increase of reported incidents – up by 250% from Q1 to Q2 of 2021. The report also found that spear phishing remains the most prevalent technique used to establish initial access in compromised systems.
15. SEGs are far from free of phishing attacks
Many users wrongly believe that using a Secure Email Gateway (SEG) protects them from phishing attacks. Unfortunately, that’s far from the truth. 90 percent of the phishing attacks reported to Cofense are discovered in an environment that uses an SEG.
Cofense cites the main reason being that even the most progressive automated detection can’t keep up with advances in the sophistication of phishing techniques. SEG developers also need to balance protection and productivity. Plus, as with all systems, SEGs are prone to configuration errors.
In its 2022 report, Cofense reveals that .pdf or .html extensions are the most common filename extensions on attachments that reach users in SEG-protected environments. These account for around 35% and 30% of threats respectively.
16. Malicious attachments exploiting CVE-2017-11882 remain common
CVE-2017-11882 is a remote code execution vulnerability that exists in Microsoft Office software. This vulnerability was identified in 2017 and subsequent updates patch the flaw. Despite this, according to Cofense, around 12 percent of malicious attachments exploit this vulnerability.
Vulnerabilities like this remain a target for attackers as some companies are slow to update their software. However, as users catch up and patch the CVE-2017-11882 vulnerability, we will likely see associated attacks diminish.
17. Some phishing attack payloads are location-aware
If you think your location doesn’t matter when it comes to cyberattacks, you may be wrong. According to Cofense, the geolocation of a user (as per their IP address) often determines how a payload behaves once delivered. For example, the content could be benign in one country but malicious in another.
18. SSL is no longer an indicator of a safe site.
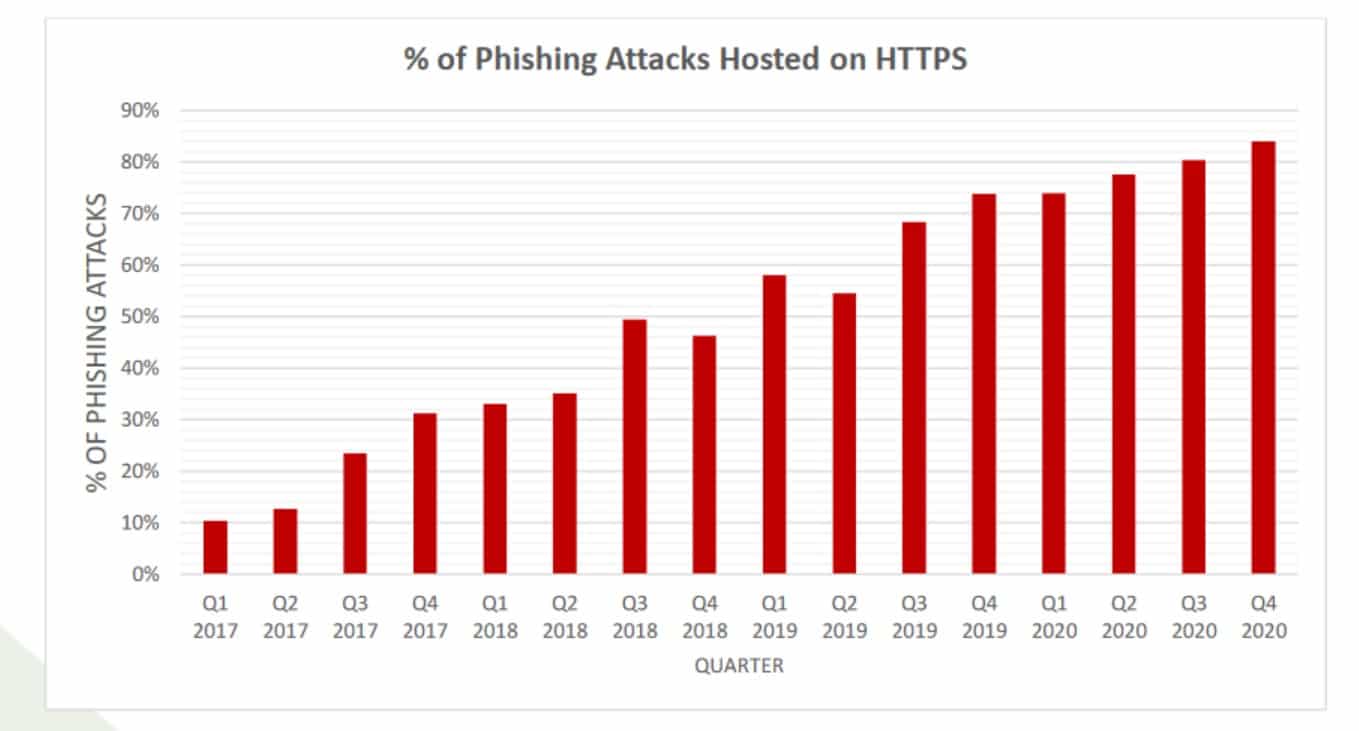
For many years, one of the primary tips for avoiding phishing sites has been to examine URLs carefully and avoid sites that don’t have an SSL certificate. “HTTPS” in the URL (versus “HTTP”) signifies that a site has an SSL certificate and is protected by the HTTPS encryption protocol.
However, this is no longer a good tactic for recognizing dubious sites. As reported by APWG, a whopping 84 percent of phishing sites examined in Q4 of 2020 used SSL. This continues the long-running trend of increasing around 3% every quarter.
19. Gift cards are still a popular form of payment in BEC attacks
The APWG also provided insight into how attackers request payment. In BEC attacks, in particular, 68 percent of attackers requested they be paid in gift cards in Q4 2021. This is an increase of eight percent over the previous quarter. Other popular forms of payment are payroll diversion (21 percent) and wire transfer (nine percent). Interestingly, direct transfers are much less common now than last quarter when it accounted for 22 percent of all scams.
20. A custom phishing page costs $3–12
On the attacker side, phishing schemes are part of a large underground industry. Symantec shows us some facts and figures from the dark web, such as the going rate for a phishing webpage is $3–12.

21. 67% of phishing attempts have blank subject lines
According to a report from AtlasVPN, almost 70% of all phishing email attempts contain an empty subject line. Some of the most commonly used subject lines cybercriminals use are ‘Fax Delivery Report’ (9%), ‘Business Proposal Request’ (6%), ‘Request’ (4%), and ‘Meeting’ (4%).
22. Almost 900 fake Amazon sites were in use on Amazon prime Day 2022
AtlasVPN reported a surge in retail websites impersonating Amazon on one of the year’s busiest shopping days. In the 90 days up to July 12, 2022, 1,633 fake sites were detected, with 897 spoof Amazon sites active on Prime Day.
Phishing projections for 2022 and beyond
Based on phishing statistics from the past year, we can expect to see a couple of key trends as we move through 2022 and into 2023:
- Attacks will increase in sophistication. According to Kaspersky, we can expect to see other nations employ any trick they can to steal COVID-19 vaccine information. We can also expect educational establishments to be targeted more frequently, given that so many students are learning remotely.
- There will be more focus on targeted ransomware. Kaspersky predicts that cybercriminals will take a simpler approach, focusing on landing one big payment from major companies, rather than lots of small payments from random targets. It predicts that this will involve rapid diversification into hacking IoT devices like smart watches, cars, and TVs.
- An increase in TrickBot activity. Cofense predicts that 2022 will see new emerging delivery methods for TrickBot with companies likely to be increasingly targeted by campaigns using LNK and CHM downloaders.
- New commodity downloaders are expected. Citing high prices for the malware downloaders currently being sold to hackers; Cofense is predicting the emergence of a new malware downloader that will be much more affordable. This could have severe repercussions for the phishing landscape.
We can’t be certain what the future holds, but we can say with some confidence that phishing will remain a significant threat to both individuals and businesses in the immediate future.
FAQs about phishing
How can I tell if an email is fake?
There are some telltale signs that an email isn't legit. These include some of the following:
- The subject line is blank
- The sender's name doesn't match their email address.
- The email asks you for personally identifying information, such as a username and password.
- Poor spelling and grammar are used in the body text.
What should I do if I handed over my login details?
If the authenticity of an email has fooled you, you should change your account password immediately. If you've accidentally provided online banking details to an attacker, you should contact your bank asap to avoid money being stolen. For social media phishing, the attacker may have sent messages to your contacts, so it's worth letting them know your account has been hacked and to get in touch via another channel (phone, text, WhatsApp).
L’article Phishing statistics and facts for 2019–2022 est apparu en premier sur Comparitech.

0 Commentaires