Overview of Datadog Cloud SIEM
Datadog entered the SIEM application market with the launch of Datadog Cloud SIEM in 2020. Datadog Cloud SIEM (Security Information and Event Management) is a SaaS-based solution that provides end-to-end security coverage of dynamic, distributed systems. It is part of the Datadog Cloud Security Platform and is designed to provide a single centralized platform for the collection, monitoring, and management of security-related events and log data from across the enterprise. This enables security teams to identify and respond to suspicious behavior patterns more effectively than would be possible by looking at data from individual systems.
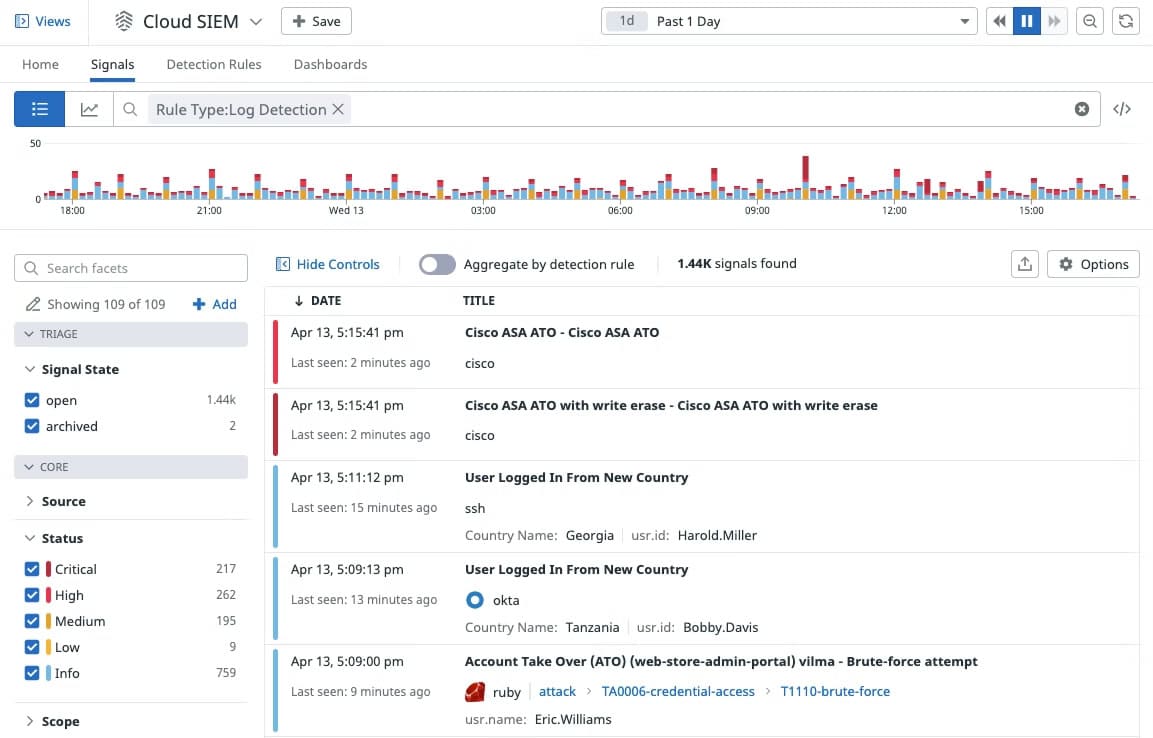
With Datadog Cloud SIEM, you can analyze operational and security logs in real-time, regardless of their volume. Developers, security, and operations teams can leverage detailed observability data to accelerate security investigations in a single, unified platform.
Key features and capabilities include :
- Observability and security See all of your security data in one place, and correlate them with runtime events, application and service logs, and more. Development, security, and operations teams can access the same observability data and drive security investigations in a single, unified platform.
- Out-of-the-box dashboards The Security Overview dashboard allows you to have a high-level view of your security posture. The IP Investigation and User Investigation dashboards enable users to correlate specific IP addresses and users with security signals, events, and logs, so they can quickly hone in on malicious activity patterns.
- Out-of-the-box threat detection rules Datadog Cloud SIEM comes equipped with out-of-the-box threat detection rules that don’t require a query language for widespread attacker techniques and misconfigurations that are mapped to the MITRE ATT&CK framework.
- Built-in vendor-backed security integrations Built-in security integrations with AWS CloudTrail, Okta, G Suite, and more enable users to ingest additional security data in minutes, which provides deeper context and helps accelerate investigations.
A free personalized demo and a free 14-day-trial with full access to all the features are available on request. After that, the software is generally sold through monthly subscription plans based on hosts, events, or logs.
Overview of Logpoint SIEM
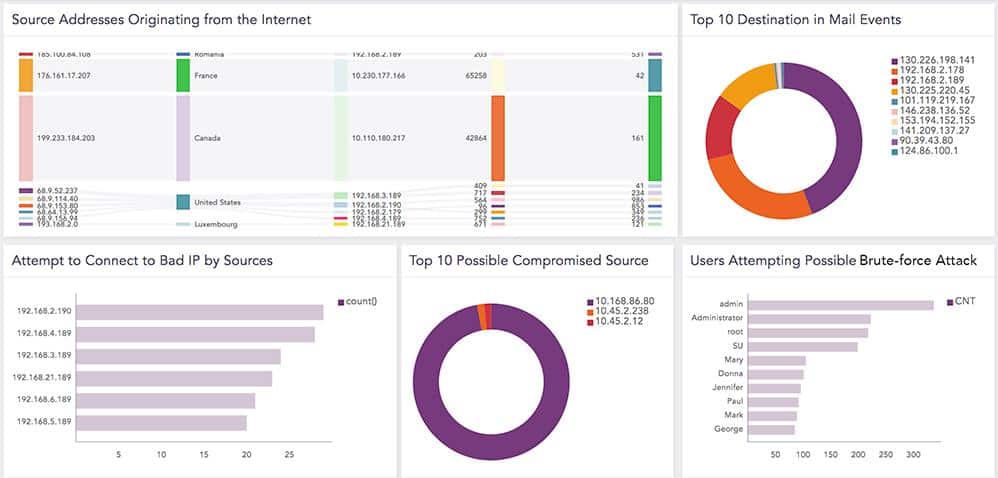
Logpoint is a Denmark-based cybersecurity solution provider that develops SIEM and other security products. Logpoint SIEM collects, stores, and analyzes log data from the entire IT infrastructure to detect suspicious activities and respond to threats. However, the modular design of the solution means that the SIEM tool is a bundle of security capabilities including automated compliance management, operational performance monitoring, and log management. Just as the name implies, Logpoint demonstrates expertise in log aggregation, management, and analysis.
Logpoint SIEM is available on-premises and as SaaS, in the cloud. The Logpoint converged SIEM is a unified platform that delivers SIEM+SOAR, UEBA, and BCAS capabilities as a service directly to enterprises and MSSPs—all from a single pane of glass. It is targeted at businesses of any size but it will be particularly appealing to large organizations. Logpoint system architecture is broken down into:
- Logpoint Collectors Collectors are responsible for the ingestion, normalization, and enrichment of log data from disparate log sources into the Logpoint platform.
- Logpoint Backend The Backend is the storage component of the Logpoint solution based on NoSQL that stores data in a flat file, enabling searches that take seconds.
- Logpoint Search head is the analytics component where customers develop the custom content that extracts value from that raw and normalized log data.
Logpoint cloud provides a single centralized platform to harness, monitor, and manage security-related data at cloud speed and scale from across the enterprise. Because Logpoint SIEM correlates data from a wide variety of event and contextual data sources, it can enable security teams to detect and respond to suspicious behavior patterns more effectively.
Key features and capabilities include:
- Improve threat detection and response Logpoint helps visualize real-time threat intelligence data and automatically puts it into context to enable swift response efforts.
- Improve the overall security posture Provides compliance for major regulatory domains such as PCI, SOX, HIPAA, GDPR, and others, making it effortless to present compliance evidence.
- Decrease time to detect and respond Logpoint helps security teams be more efficient by automating tasks and providing structured workflows.
- Streamline investigation, automated response Logpoint unified SIEM-SOAR solution empowers analysts with built-in detection, investigation, automation, orchestration & response playbooks to boost SOC productivity.
- Converged SIEM 75+ ready-to-use playbooks automate and accelerate the investigation and response processes.
- Discover suspicious behavior LogPoint UEBA capabilities enriches data with information about users and assets behavior, threats, and vulnerabilities, and detects security incidents that other solutions leave unnoticed.
The product is shipped in a virtual appliance, physical appliance, or as a piece of software or Cloud delivered Converged SIEM, allowing the organization complete flexibility in deployments. A free online demo is available on request.
Datadog Cloud SIEM vs. Logpoint SIEM: How They Compare
Deployment Model
Just as the name implies, Datadog Cloud SIEM is a cloud-based application for cloud-native environments; which means there are no on-premise system requirements and no installation hassles other than the usual sign-up process using an internet-connected device with a supported browser. However, you’ll be required to install local agents specific to the device or service you wish to monitor, for the most part. This deployment makes it ideal for organizations that don’t want to burden themselves with any resource-intensive on-premise SIEM solution
On the other hand, Logpoint SIEM offers both SaaS-based and self-hosted (on-premises) versions. The SaaS-based version just like Datadog needs no installation other than the usual sign-up process using an internet-connected device with a supported browser. However, to enable communication between your Cloud Connector appliances and the cloud service, you’ll be required to install the Logpoint Cloud Connector on your on-premise appliance. Logpoint SIEM’s self-hosted deployment model is ideal for organizations that want to have granular control, but it comes at a cost—you also have to manage it yourself.
Data Collection and Analytics
Datadog Cloud SIEM collects logs from many different sources into Datadog. All ingested logs are first parsed and normalized (reformatted) for consistency, easy correlation, and analysis. This helps to uncover malicious activities on the network, preventing bad actors from concealing their tracks. Once logs are collected, ingested, and processed, they are available in Log Explorer. Log Explorer is where you can search, enrich, and view alerts on your logs. This makes it easy to search and filter log data across your entire infrastructure for threat detection and investigation.
Similarly, Logpoint SIEM collectors are responsible for the ingestion, normalization, and enrichment of log data from disparate log sources into the Logpoint platform for your use cases. All logs are centralized into a single platform called the Logpoint Backend to streamline analysis, search, and investigations. Logpoint’s unique taxonomy harmonizes data from cloud applications, core infrastructure, security products, and proprietary applications, among other sources. By leveraging this taxonomy, analytics is consistent across all data sources and use cases. Logpoint provides a good-looking user interface where you can access a structured overview of critical events & security incidents in real-time.
Incident/Threat Detection and Mitigation
Datadog detects threats based on rules and creates a security signal. Datadog provides out-of-the-box rules for widespread attacker techniques, mapped to the MITRE ATT&CK framework. Detection rules take full advantage of Datadog’s “Logging without Limits”, which lets you customize what logs you want to index while still ingesting, processing, and archiving everything. Rules apply to the full stream of ingested, parsed, and enriched logs so that you can maximize detection coverage without any of the traditionally associated performance or cost concerns of indexing all of your log data.

On the other hand, the Logpoint converged cloud-based SIEM platform delivers AI-driven SIEM-SOAR-UEBA services directly to enterprises and MSSPs. SOAR (Security Orchestration Automation and Response) and UEBA (User Entity Behavior Analytics) capabilities enable organizations to collect data about security threats from multiple sources and respond to security events without human assistance. By automating routine actions. UEBA identifies suspicious patterns in user behavior.
Both SOAR and UEBA help security teams to become more efficient and frees up their time for more demanding tasks. The Logpoint business-critical application security (BCAS) capabilities also allows you to detect and respond to threats in your SAP environment. Detections are aligned with MITRE ATT&CK and shared openly for review and activation. This enables you to gain insight into the entities at the highest risk with threat intelligence and security analytics.
Notifications and Alerts
Datadog’s approach to alerts and notifications is based on machine learning (ML), which it calls Watchdog. Watchdog uses ML techniques to identify problems in your infrastructure, applications efficiency, and services, and flag anomalies. Alerts in Datadog are called Monitors. Users can receive alerts using PagerDuty, Slack, and email. These can be based on nearly any metric that Datadog can capture. As a result, every alert is specific, actionable, and contextual—even in large and temporary environments. This unique approach to alerts and notifications makes Datadog stand out and helps to minimize downtime and prevent alert fatigue.
Alerts in Logpoint are warnings generated to notify users when any significant events occur. They fire incidents that enable you to execute appropriate actions. Any valid search query can trigger an alert to generate incidents. You can create an alert rule and select the medium to notify you of the incident. If you create an alert rule to detect system crashes, an alert is fired whenever the search results match the alerting criteria. Logpoint then creates the corresponding incident based on the alert rule. Logpoint gives you the flexibility to design an alert mechanism based on your requirements. Logpoint can notify users via email, SSH, SNMP, HTTP, or Syslog. Logpoint lets you find events such as a system crash, power down, cables unplugged, high disk usage, high CPU usage, and forensics by creating incidents for each of them.
Reporting and Integration
Instead of generating the usual out-of-the-box reports that most network admins expect, Datadog’s approach to reporting aims to make metrics easily searchable, and it does excellently. Cloud SIEM is fully integrated with all of Datadog’s application and infrastructure monitoring products, which allows users to seamlessly pivot from a potential threat to associated monitoring data to quickly triage security alerts. Datadog’s 500+ integrations let you collect metrics, logs, and traces from your entire stack as well as from your security tools, giving you end-to-end visibility into your environment. Datadog integration with Slack and PagerDuty allows you to automatically loop in relevant teams when a high-severity rule detects a threat. You can also export security signals to collaboration tools like JIRA or ServiceNow.
Logpoint SIEM reports are used in different segments of a business to analyze, gain insights, and make decisions. Whether your data is in a single cloud, across multiple clouds, or on-premises, Logpoint gives you the flexibility to use a variety of in-built reporting templates that enable you to meet compliance requirements for PCI, SOX, ISO2700X, HIPAA, and more. These reporting templates can be modified to suit reporting needs. New reports can also be created from scratch using the intuitive Report Wizard.
Logpoint out-of-the-box and custom integrations allow you to have a SIEM solution that matches your organization’s needs. It comes loaded with support for several cloud sources such as Salesforce, Office365, Azure, and Amazon Web Services (AWS). It also supports integration with 400+ log sources. This allows you to seamlessly acquire data from your on-premise and cloud infrastructure, applications, and services into your SIEM platform.
Licensing and Price Plans
Datadog Cloud SIEM pricing model is per GB of analyzed logs, per month billed annually or on-demand. An analyzed log is a text-based record of activity generated by an operating system, an application, or other sources analyzed to detect potential security threats. Datadog charges for analyzed logs based on the total number of gigabytes ingested and analyzed by the Datadog Cloud SIEM service.
Unlike Datadog, the Logpoint licensing model is based on the number of log sources consumed, not the data volume or events per second. Whether you are using Logpoint Converged SIEM Cloud or deploying on-premise, the core pricing model remains the same irrespective of the data volume or use case. This allows you to design and deploy a multi-server environment, irrespective of the size of the archive, amount of log data, or several users—without affecting the cost. Simply deploy what you need and adapt as your vision evolves.
Choosing Between Datadog Cloud SIEM and Logpoint SIEM
Datadog and Logpoint no doubt have distinguished themselves over the years in the observability, logging, and security space. Deciding between the duo shouldn’t be about which is better, but about which best meets your business needs.
You need to consider a variety of factors such as:
- Is the SIEM solution capable of meeting your organization’s security and compliance requirements?
- How much native support does the SIEM tool provide for relevant log sources?
- Does the SIEM solution possess the capabilities of next-generation SIEM functionalities such as SOAR and UEBA?
- What is the total cost of ownership, is vendor support available in your region, and to what extent?
Datadog’s ability to support and integrate with more than 500 technologies makes it more versatile and adapted to many different functions, provides deeper context during investigations, and lets you cast a wider net to catch possible security issues. However, the lack of SOAR and UEBA capabilities makes it less effective in tackling modern security challenges. Nonetheless, Datadog Cloud SIEM is an excellent tool for existing Datadog customers and organizations that don’t have dedicated IT personnel to keep tabs on the infrastructure at a granular level.
Logpoint converged SIEM cloud platform or self-hosted deployment option gives organizations the flexibility to choose the deployment model most suitable for them. The self-hosted option is ideal for organizations that want to be in complete control, but it will require an investment in skilled human resources to manage it. Logpoint SOAR and UEBA combined capabilities put it in a better position to collect data from multiple log sources, identify hidden threats, and provide automated responses without human intervention. This creates a more effective defense against modern security challenges.
L’article Datadog Cloud SIEM vs LogPoint SIEM est apparu en premier sur Comparitech.

0 Commentaires