Data protection software covers a wide range of services. Within this category, you will find data management systems, sensitive data protection tools, data loss prevention services, vulnerability scanners, and threat detection. The ideal data protection package will include all or most of these elements.
Here is our list of the six best data protection software packages:
- N-able Backup EDITOR’S CHOICE A data security system that prepares for unexpected data loss by managing backups of all data to provided cloud storage space. This is a cloud-based service.
- ManageEngine DataSecurity Plus A bundle of services that categorizes data by sensitivity, identifies vulnerabilities and protects files from tampering. Available for Windows Server.
- FireEye Helix A cloud-based threat management system that includes log file monitoring and protection.
- Acronis Cyber Protect A package that includes backups, vulnerability scanning, and data loss prevention. Runs as a virtual appliance.
- Files.com A secure file transfer and storage system that supports the implementation of a centralized data control strategy.
- Azure Information Protection This service from the well-known cloud platform tracks your sensitive data no matter where it is – it doesn’t have to be on an Azure server.
You can read more about each of these options in the following sections.
The information that your company needs as source material falls into several categories. You have reference data, transactional data, and research data. The transactions and research that your company performs are based on reference data. Within the reference data category, you have information about your customers, suppliers, employees, and associates.
The information you hold on associated companies needs to be protected because it is probably covered by some contractual obligation. For example, a supplier may have given you a tailored price list, which they wouldn’t want their competitors or other customers to know about. Similarly, your sales team has probably stored the special deals that it has agreed to win the business of a new customer and they wouldn’t want their existing clients to know about that. Other important internal business data that needs to be protected are the salaries paid to employees and intellectual property.
The reference data in your system that pertains to individuals is covered by legislation and you could face fines if that information gets disclosed. Those individuals whose information is leaked also have the right to sue your company. Laws also govern how you use that data, which is called Personally Identifiable Information (PII), and even where you store it.
Data protection priorities
When conducting data protection, you need to consider three areas of concern:
- Data loss
- Data disclosure
- Data misuse
Ensuring that you put in place software to prevent these three types of events will give you a data protection strategy.
Data loss
Within the IT industry “data loss” usually means data theft. In this guide, we use the term to mean accidental or environmental events that cause data to be no longer accessible. So, a server being ruined by a burst pipe or an IT technician accidentally wiping a disk would be two examples of this. In other words, the data is lost and cannot be recovered.
It should be assumed that the only reason you hold each piece of information is that your business needs it to operate. Imagine if all of your system’s customer accounts suddenly got wiped or if you lost all of the work in progress that your company’s consultants and engineers have stored while working on client accounts.
The consequences of the actual unrecoverable loss of data would be catastrophic. While the loss of all data of a particular type would be disastrous, so would even the loss of part of the data. This type of data protection forms part of company continuity procedures and relies on backup and recovery systems.
Data disclosure
Data disclosure refers to non-authorized access to data. This might be through theft or through sharing. In the case of data sharing by authorized users, this could be accidental or intentional. Intentional data disclosure could be driven by resentment against the company, as a power play by rival employees, or as a whistleblowing act.
Protecting data from disclosure is carried out through data loss prevention systems and threat detection.
Data misuse
Data misuse is usually intentional. For example, a company might use contact information for clients of one division to launch a promotion campaign for the launch of a new division. Data is held for a purpose and must not be spread around to benefit unrelated activities. Holding incorrect data is classified as data misuse because it incorrectly labels a customer. These types of events can be prevented through data governance and data protection compliance packages.
As incorrect information is classified as misuse, unauthorized alteration to records is another form of misuse that needs to be guarded against. Changes that render stored information incorrect can be performed accidentally or intentionally by employees, by company management to cover up a misdemeanor or improve a financial or by an intruder to cover up activity or to slur a rival. This type of data misuse can be guarded against by file integrity monitoring (FIM) systems.
The best data protection software
When looking for the best data protection software, we are aiming for packages that can cover as many of the damaging events that can impact data integrity. Data protection standards, such as PCI DSS and HIPAA understand that some data disclosure events are unavoidable. However, in these cases, the standards expect that companies should spot the data disclosure, loss, or damage with speed and notify all of those affected by the event as quickly as possible. The data attacks should also be reported to the relevant authorities as quickly as possible, while remediation attempts to recover data or prevent a similar attack from happening are also expected.
What should you look for in a data protection system?
We reviewed the market for data protection software and analyzed the options based on the following criteria:
- An off-site system or virtual appliance that is systemically protected from events on the network
- A data persistence service that enables backups to be managed and changes to be rolled back
- A method to identify sensitive data and implement graded protection measures
- Integrated vulnerability and risk management
- Action logging for compliance auditing
- A demo or a free trial for a no-cost assessment
- Value for money offered by bundles that discount each function when compared to the cost of buying them individually
As well as following those guidelines, we looked for tools that would cover as many aspects of data protection as possible and specialized systems that are geared towards achieving excellence in specific aspects of data protection.
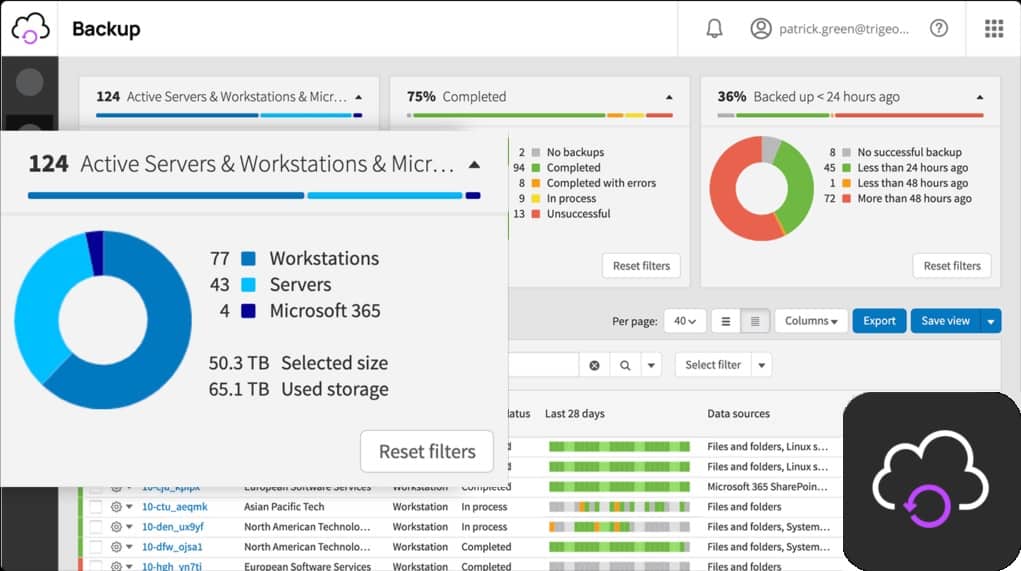
1. N-able Backup
N-able offers a range of services that support Managed Service Providers (MSPs). However, these tools can also be useful for in-house IT departments, especially those that manage multiple sites. The N-able Backup system is based in the cloud, so it can automate the backup services of any site anywhere. Backups created by this system can be used for migration or replication as well as for restoring lost data to the same location.
Data needs to be uploaded to the N-able cloud servers for storage. However, this is not a security risk because transfers are protected with strong encryption. This involves the AES cipher with a 256-bit key, which is considered uncrackable. Data is compressed for transmission, which speeds up the storage process and also makes the restore phase quicker.
While on the N-able server, backups are also protected by 256-bit key AES encryption. N-able has data centers around the globe and will store your backups in a location closest to your site to make transfer paths shorter. Data held on the N-able servers is also mirrored on another server, so there is no risk that the backups that you save can be lost or damaged.
If your business is hit by environmental damage that renders your premises inoperable, N-able Backup enables you to get up and running as soon as you have started up the alternative site that your business continuity plan designated. The backup system can populate your new servers with your old data, meaning that the business can continue to run with minimum disruption.
The N-able Backup system can manage the contents of virtual servers as well as physical servers. Servers can be backed up down to the operating system – even including the OS. The service has special backup routines for Microsoft Exchange Server, Sharepoint, and MySQL. It is also possible to backup OneDrive with N-able Backup. Updates can be versioned, creating timed archives, any one of which can be used in full or partially to restore files. This is an important function to recover from unauthorized file tampering, which might not be discovered before many backup cycles have occurred.
N-able Backup can operate restore actions to bare metal servers, physical-to-virtual, or virtual-to-virtual. The N-able Backup system can be assessed on a 30-day free trial.
EDITOR’S CHOICE
N-able Backup is our top pick for data protection software because it includes all of the storage space you need to hold copies of your important data. The Backup system is automated and can cover data held on any site. The system creates efficiency by running constantly in the background, performing incremental backups and its off-site location means the processes of the Backup service won’t be impacted by any environmental damage or system hijacking that could be the cause of your data loss or tampering.
Get a 30-day free trial: n-able.com/products/backup/trial
Operating system: Cloud-based
2. ManageEngine DataSecurity Plus
ManageEngine DataSecurity Plus includes File Server Auditing, Data Leak Prevention, and Data Risk Assessment. The facilities in this bundle include sensitive data discovery, data classification, file integrity monitoring, and vulnerability scanning.
The service tracks down all of your data stores, whether they be on one of your sites or a cloud server. The tool will categorize data, identifying PII and other sensitive data that requires extra security and tracking. The system analyzes file permissions and access rights to devices and folders, identifying weaknesses and recommending changes.
Other services in the DataSecurity Plus package include File Integrity Monitoring (FIM). This is tamper protection that tracks changes to files, noting who made those changes and when. This service can be linked to a restore system to wipe out unauthorized changes. The service will raise an alert if a protected file is changed or deleted.
The DataSecurity Plus service monitors USB slots and blocks memory sticks from attaching. It is possible to log all file movements onto USB drives and selectively block some files from being copied. Similar controls are available for email attachments.
ManageEngine DataSecurity Plus is an on-premises package that installs on Windows Server. You can get it on a 30-day free trial for assessment.
3. FireEye Helix
FireEye Helix is a next-generation SIEM service that includes a threat intelligence feed. This service is a good choice to protect your entire IT system and all data from theft or other malicious activity. The service doesn’t just block intruders. It includes a system called User and Entity Behavior Analytics (UEBA) that can identify unusual activities performed by authorized accounts. This anomalous behavior may indicate a hijacked account or an insider threat. Account hijacking can be identified by illogical login activity, such as an account of a user being used in a different country. The system will track the activities of those suspicious accounts, particularly concerning data access.
You can set up your Helix system to perform by a specific data protection standard. The service operates with “playbooks” which are workflows that get triggered by a particular combination of events. It is also possible to create your playbooks. The service is hosted in the cloud and the dashboard is accessed through any standard Web browser. Those dashboard screens can also be customized.
Integrations in the Helix package will exchange data and interact with other applications if you activate them. This makes it easier for the security system to extract activity reports from other services and also implement remediation through coordinating with other systems.
Access a self-guided tour of the Helix platform to assess it for yourself.
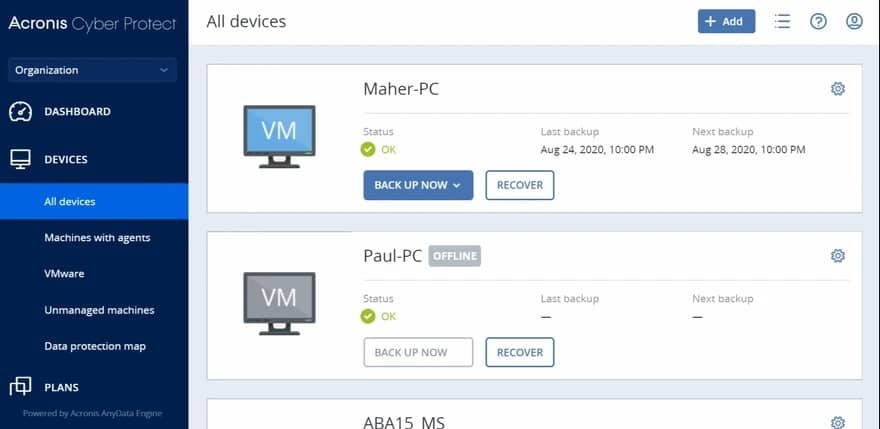
4. Acronis Cyber Protect
Acronis Cyber Protect is a bundle of security and data management services. It includes a backup system, a vulnerability scanner, and a threat-protection system.
The backup service can also be used to replicate servers, enabling you to set up new hardware quickly if your premises get destroyed. This can protect servers running Windows Server and Linux. The backup service will operate on virtualizations as well as physical systems.
Backups can be made to other devices on-premises or to cloud storage systems. Acronis offers a cloud storage facility but this is not included in the price of the Cyber Protect system and the two systems are not glued together, so the choice of platform is up to you.
The controller for the system is based in the cloud and one agent on your site will manage all of the system and data protection services on the Cyber Protect bundle. Acronis offers this system on a 30-day free trial.
5. Files.com
Files.com is a cloud service that operates as a secure file store and transfer manager. You can improve data protection by centralizing all file storage in one place on this cloud storage system. Uploads to the service are protected by encryption as files at rest on the server.
Files.com gives you several data management strategies. You can institute a working practice that requires all files to be created and saved on the cloud platform. This service integrates with Microsoft 365, so by removing endpoint software, you get better control over where files are saved. Each user gets an individual account, which enables all actions on files to be tracked. There is also an administrator account for each plan, which has several file tracking services built into it.
When all files are on the Files.com server, users can distribute or share files by sending out a link to the file on the server. Permissions can be restricted to read-only, controlling the number of copies that are issued for each file and tightening data protection.
You can assess Files.com on a 7-day free trial.
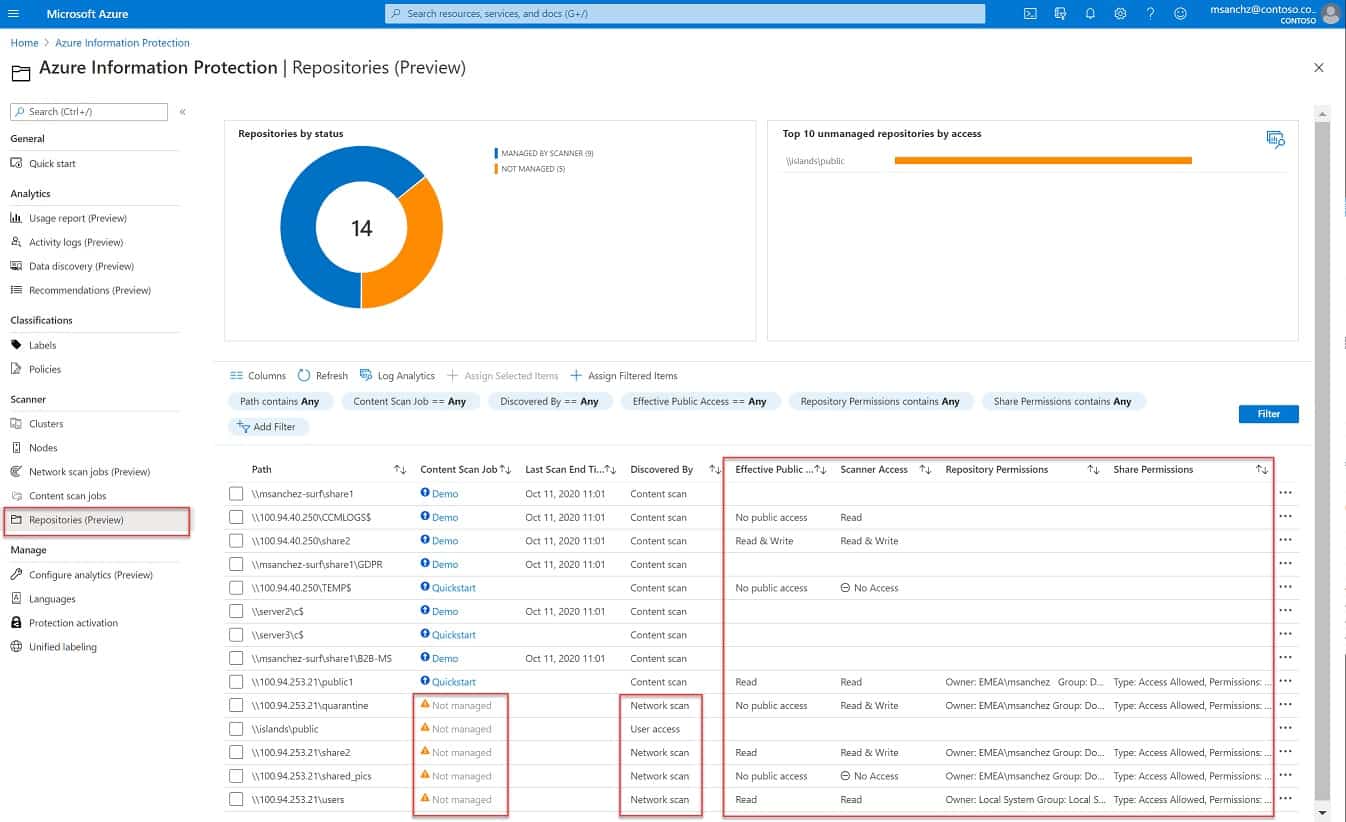
6. Azure Information Protection
Azure Information Protection will search all of your data stores and categorize files by sensitivity. This action can be applied to any site and also to cloud servers. The cloud data management capabilities are not restricted to Azure accounts – the data can be located on any cloud platform.
The monitoring service operates continuously, catching new files as they get saved and including them in the grading and control service. The classification of data as sensitive relies on the settings you put into the system. This enables the service to tailor its protection services according to data standards, such as GDPR, PCI DSS, or HIPAA.
It is possible to block sensitive files from being copied or transferred. You can also prevent their contents from being printed and those files can also be prevented from attaching to emails.
The Azure Information Protection service includes an encryption service to protect files on your server and in transit. You can link the Azure Information Protect service to your Active Directory implementation for access rights management.
L’article 6 Best Data Protection Software est apparu en premier sur Comparitech.



0 Commentaires