Keeping a computer network up and running—especially in a Linux environment, takes some skills
A network or system administrator needs to have the right skills required to manage and maintain a network. One of such skills is an excellent hands-on knowledge of network troubleshooting. There are times when troubleshooting will account for more than seventy percent of a network administrator’s time. Fortunately, network troubleshooting tools can enable you to quickly resolve issues during those crisis times and keep your network operating as designed.
Here is our list of the best Linux network troubleshooting tools:
- ManageEngine OpManager A highly scalable Linux network monitoring tool. It can monitor Linux devices and traffic in your network for availability, health, and performance in real-time and generate network performance reports
- Ping A network troubleshooting tool used to test the reachability of a host on an Internet Protocol (IP) network.
- IP command tool Found in the net tools which are used for performing several network administration tasks.
- NSLookup A network administration command-line tool for querying the Domain Name System (DNS) to obtain the mapping between a domain name and IP address.
- Domain Information Groper (Dig) A network administration command-line tool for querying the DNS. Dig is useful for network troubleshooting and educational purposes.
- Ethtool A tool used for troubleshooting in a Linux network. It is primarily used to query and control Ethernet devices, including driver and hardware settings on Linux systems.
- PuTTY A free and open-source terminal emulator, serial console, and network file transfer application.
- Traceroute A tool in Linux that allows you to investigate the routes of network packets and identify the limiting factor in their journeys.
- Route The route command is used to view and make changes to the kernel routing table on Linux, BSD, and other Unix-like systems.
- NETCAT and NCAT A tool for reading from and writing to network connections using TCP or UDP. It is a feature-rich network troubleshooting and investigation tool.
A good understanding of those troubleshooting tools serves as an advantage. In addition, Linux supports lots of useful command-line tools that can help you narrow down to the root cause of a network issue. This article will explore the ten best Linux network troubleshooting tools to help you when things don’t seem to work.
The Best Linux Network Troubleshooting Tools
1. ManageEngine OpManager
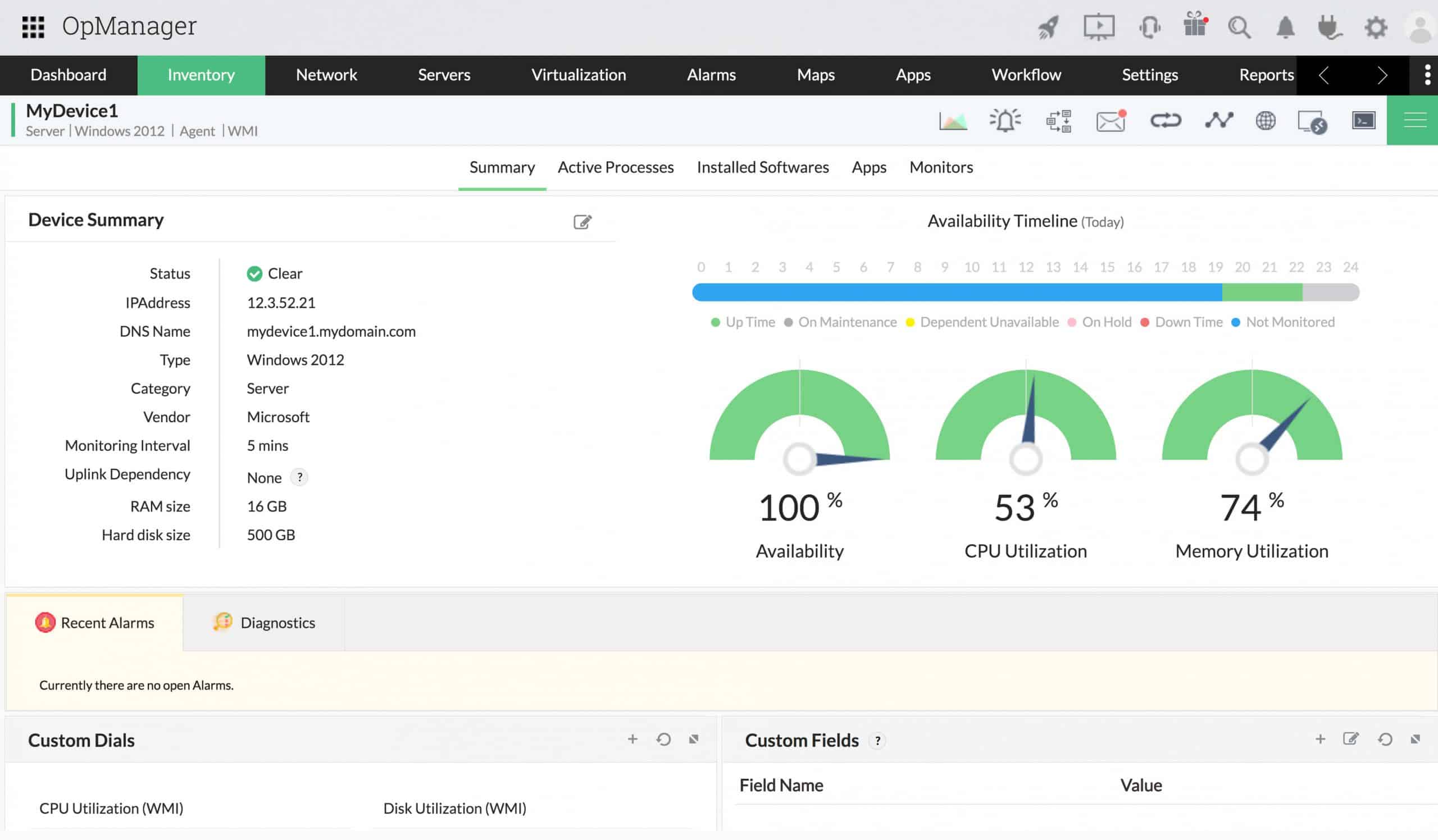
ManageEngine OpManager is a highly scalable Linux network monitoring tool. It can monitor Linux devices and traffic in your network for availability, health, and performance in real-time and generate network performance reports. These reports can be used to make a better purchase or upgrade decisions. In addition, with over 2,000 metrics for monitoring network device performance, OpManager can be used to monitor and identify faults in real-time, so performance issues can be fixed before they impact end-users.
OpManager can provide alerts on the performance degradation of devices in a Linux network. In addition, it categorizes the alerts into Attention, Trouble, Critical, and Service Down. This helps to streamline and prioritize response efforts. Some of the key features and capabilities include:
- Real-time Linux network performance monitoring
- Physical and virtual Linux server monitoring
- Network Performance Reporting
- Customizable dashboards
- Email and SMS alerting
OpManager has many built-in Linux network troubleshooting tools such as Ping, Traceroute, CLI, SNMP, MAC Address Resolver, DNS Resolver, DHCP Scope Monitor, and Port Scanner. The software comes in different editions, which are tailored to suit your network and server monitoring requirements, as shown in Table 1.0 below:
| Features | Free | Standard | Professional | Enterprise | MSP |
|---|---|---|---|---|---|
| Targeted at | Small network | Small to medium networks | Mid to Large networks | Geographically distributed networks | MSPs managing multiple clients |
| Monitor up to | 3 devices | 1000 devices | 1000 devices | 10,000 devices | 10,000+ devices |
| Starting price | Free | $245 | $345 | $11,545 | Contact vendor |
Table 1.0 | Comparison of the different editions of OpManager
OpManager license options depend on the number of devices to be monitored. The license is inclusive of all the interfaces, nodes, or sensors in the device. A device can have any number of interfaces, elements, or sensors. You can download the free version for evaluation or check out the 30-day fully-functional trial to confirm its capabilities and make sure it’s the right fit for your organization before purchase.
2. PING
Ping is a network troubleshooting tool used to test the reachability of a host on an Internet Protocol (IP) network. The ping command is one of the most used tools for troubleshooting, testing, and diagnosing network connectivity issues in Windows and Linux environments. With this tool, you can test if a server is up and running. Ping works by sending one or more ICMP (Internet Control Message Protocol) Echo Request packets to a specified destination IP on the network and waits for a reply. When the destination receives the packets, it responds with an ICMP echo reply. This helps to determine whether a remote host is reachable or not. It can also determine whether there is a packet loss by examining the round-trip delay in communicating with the destination.
Ping is part of the iputils (or iputils-ping) package, pre-installed on nearly all Linux distributions. Most Linux users are familiar with the tool and know how to use it in its basic form. However, there are many additional ping options and variations. The syntax for the ping command is as follows: ping [option] [hostname] or [IP address]
To better illustrate how the ping command works, let’s ping google.com. The output is as shown on the screenshot below:
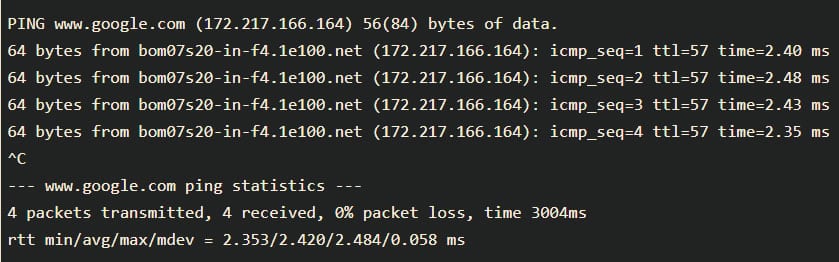
The ping command resolves the Google domain name into an IP address and starts sending ICMP packages to the destination IP. If the destination IP is reachable, it will respond, and the ping command prints a line that includes the following fields:
- The number of data bytes. This translates into 64 ICMP data bytes – 64 bytes.
- The IP address of the destination – from bom07s20-in-f4.1e100.net (172.217.166.164).
- The ICMP sequence number for each packet. icmp_seq=1.
- The Time to Live: This refers to the amount of time or “hops” that a packet is set to exist inside a network before being discarded by a router. – ttl=57.
- The ping time, measured in milliseconds, is the round trip time for the packet to reach the host and the response to return to the sender. – time=2.40 ms, etc.
3. IP Command
The IP command tool in Linux is present in the net tools, which are used for performing several network administration tasks. For example, with the IP command, you can adjust how a Linux computer handles IP addresses, network interfaces controllers (NICs), and routing rules.
The tool is similar to the ifconfig command, but it is much more powerful and has more functions and facilities. Older Linux distributions used the now deprecated ifconfig command, which operates similarly. However, ifconfig has a limited range of capabilities compared to the IP command.
The syntax for the IP command is as follows: [OPTION] OBJECT {COMMAND | help}
Objects subcommands that you will use most often include:
- Link (l) – used to display and modify network interfaces.
- Address (addr/a) – used to display and modify protocol addresses (IPv4/IPv6).
- Route (r) – used to display and alter the routing table.
- Neigh (n) – used to display and manipulate neighbor objects (ARP table).
4. Name Server Lookup (NSLookup)
NSLookup is a network administration command-line tool for querying the Domain Name System (DNS) to obtain the mapping between a domain name and IP address. It’s convenient when troubleshooting DNS issues on a Linux system.
NSLookup queries the specified Linux DNS server and retrieves the requested records associated with the domain name you provided. Other DNS records that can be obtained include:
- A: the IPv4 address of the domain.
- AAAA: the IPv6 address of the domain.
- CNAME: the canonical name (CNAME) allows one domain name to map onto another. This enables multiple websites to point to a single IP or web server.
- MX: the server that handles email for the domain.
- NS: one or more authoritative name server records for the domain.
- TXT: a type of DNS record that contains text information for sources outside of your domain. This information is used for email spam prevention and domain ownership verification, among others.
Thenslookup tool comes bundled inside the bind-utils package in older Linux systems, while newer Linux systems ship the nslookup tool by default. The nslookup tool can operate in interactive or non-interactive mode. When used interactively, the user issues parameter configurations or requests when presented with the nslookup prompt (>). When no arguments are given, then the command queries the default server. In non-interactive mode, i.e., when the first argument is a name or Internet address of the host being searched, parameters and the query are specified as command-line arguments in the program’s invocation. The non-interactive mode searches the information for a specified host using the default name server.
5. Domain Information Groper (Dig)
Dig is a network administration command-line tool for querying the DNS. Dig is useful for network troubleshooting and educational purposes. With dig, you can query DNS servers for information regarding various DNS records, including host addresses, mail exchanges, name servers, and related information. It was intended to be a tool for diagnosing DNS issues. However, you can use it to poke around and learn more about DNS, which is one of the central systems that keep the internet routing traffic.
Newer Linux systems ship dig utilities by default, but most older ones come bundled inside the bind-utils package. Thus, dig is usually installed by default on most Linux distributions, and you can access it from the command line with no additional installation. To confirm if dig is installed on your Linux system, run the # dig -v.
If the command returns anything other than dig’s version information, you may need to install dnsutils. For example, to install dnsutils on a Linux server, run the following commands:
For Debian/Ubuntu distribution, use the command: sudo apt-get install dnsutils
For RedHat/CentOS distribution, use the command: dnf install bind-utils
Once you’ve installed dnsutils, run the # dig -v command again to verify dig’s installation.
6. Ethtool
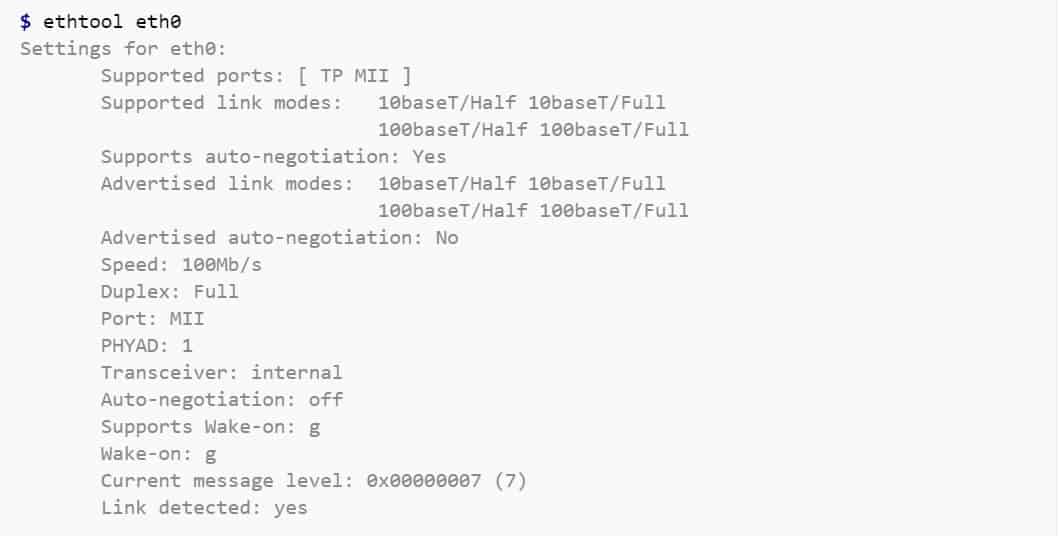
Ethtool is a tool used for troubleshooting in a Linux network. It is primarily used to query and control Ethernet devices, including driver and hardware settings on Linux systems. Ethtool can also be used to find important information about connected Ethernet devices on your Linux network. Other ways the tool can be used include:
- Control speed, duplex, auto-negotiation, and flow control for Ethernet devices
- Control checksum offload and other hardware offload features
- Control receive queue selection for multi-queue devices
- Control DMA ring sizes and interrupt moderation
- Identification and diagnosis of Ethernet devices
- Identification and diagnosis of Ethernet devices
- Extended Ethernet devices statistics
- Upgrade firmware in flash memory
Most Linux distributions provide a standard utility program called ethtool that can be used from a shell to control or gather information from NICs using the ethtool userspace API. The tool consists of the following key components:
- An API within the Linux kernel can send and receive parameters through their device driver software, through which NICs can send and receive parameters.
- A userspace API based on the Linux SIOCETHTOOL ioctl mechanism through which application programs can communicate with the kernel to send and receive NIC and NIC driver parameters.
Ethtool is installed by default in most Linux distributions. However, you can check whether ethtool is installed already with the following command: # sudo ethtool –version.
If you see an error, then ethtool may not be installed on your computer. However, you can install it via the official package repository of your favorite Linux distribution.
7. PuTTY
PuTTY is a free and open-source terminal emulator, serial console, and network file transfer application. It supports several network protocols, including SCP, SSH, Telnet, rlogin, and raw socket connection. PuTTY was originally written for Microsoft Windows, but it is now supported on Linux OS.
The Linux version of PuTTY is a graphical terminal program that supports the SSH, telnet, and rlogin protocols and connects to serial ports. It can also connect to raw sockets, typically for debugging purposes. Some Linux users may be wondering why anyone would use a separate SSH client on Linux when there’s already a pre-existing native Linux terminal? There are several reasons why you would want to use Putty on Linux:
- Familiarity: You have used Putty for so long on Windows that you are more comfortable with it.
- Convenience: You find it difficult to manually edit SSH config files to save the various SSH sessions, so you prefer Putty’s graphical way of storing SSH connections.
- Troubleshooting: You want to debug by connecting to raw sockets and serial ports.
Putty is not installed by default on most Linux distributions. Instead, you have to manually install it from the default official repositories or package manager in your Linux distributions. Since most people would prefer to use the pre-installed OpenSSH in a terminal window on Linux for basic SSH access, the primary use of Putty on Linux is primarily for debugging: connecting to serial ports and raw sockets.
8. Traceroute and Tracepath
Traceroute is a tool in Linux that allows you to investigate the routes of network packets and identify the limiting factor in their journeys. Traceroute is also helpful for mapping local networks and troubleshooting sluggish connections. Insight into the topology and connections of the local network is found when running the tool.
Traceroute works by sending packets of data to the target computer, server, or website and recording any intermediate steps through which the packets travel. The output of a traceroute command will be the IP addresses and domain names through which the packets pass. These entries also show how long it takes for the packets to reach each destination. The information obtained may explain why some websites may take longer to load than others, as the number of traffic hops can vary.
On Linux or Unix-like operating systems, traceroute sends, by default, a sequence of User Datagram Protocol (UDP) packets, with destination port numbers ranging from 33434 to 33534. The implementations of traceroute shipped with Linux include an option to use ICMP Echo Request packets (-I) or any arbitrary protocol (-P) such as UDP, TCP using TCP SYN packets, or ICMP.
Tracepath is another utility similar to traceroute on Linux, with the primary difference of not requiring superuser privileges. Traceroute and tracepath are available for installation from the default official repositories or package manager in most Linux distributions.

9. Route
The route command is used to view and make changes to the kernel routing table on Linux, BSD, and other Unix-like systems. It sets up static routes to specific hosts or networks through an interface after it has been configured. Route command in Linux is primarily used when you want to work with or update the IP/kernel routing table.
Many Linux distributions do not have route commands pre-installed. To install it on your favourite Linux distribution, use the following commands: On Debian/Ubuntu distribution use the command: # sudo apt-get install net-tools. On RedHat/CentOS distribution use the command: # sudo yum install net-tools. The syntax for the route command is as follows:
route [-nNvee] [-FC] [<AF>] List kernel routing tables
route [-v] [-FC] {add|del|flush} ... Modify routing table for AF.
route {-h|--help} [<AF>] Detailed usage syntax for specified AF.
route {-V|--version} Display version/author and exit.
When the add or delete options are used, route modifies the routing tables. Without these options, the route displays only the current contents of the routing tables.
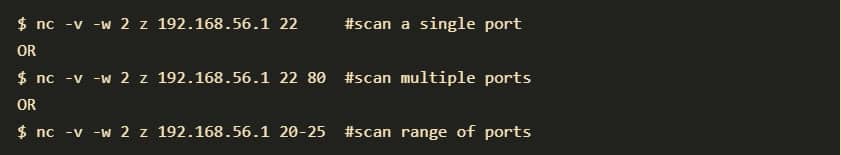
10. NETCAT and NCAT
Netcat is a tool for reading from and writing to network connections using TCP or UDP. It is a feature-rich network troubleshooting and investigation tool. Netcat can be used directly or indirectly as a backdoor tool into other networked systems, allowing you to remotely carry out port scanning, port listening, and file transfer. Other common uses include shell-script-based HTTP clients and servers, network daemon testing, and simple TCP proxies. Some of the key features and capabilities include:
- Outbound or inbound connections, TCP or UDP, to or from any ports
- Optional ability to let another program service establish connections
- Full DNS forward/reverse checking, with appropriate warnings
- Ability to use any locally configured network source address
- Can read command line arguments from standard input
- Built-in port-scanning capabilities, with randomization
- Slow-send mode, one line every N seconds
- Hex dump of transmitted and received data
- Built-in loose source-routing capability
- Ability to use any local source port
- Optional telnet-options responder
A modern reinvention of the Netcat tool is called Ncat. Ncat was developed for the Nmap Project; it combines the best capabilities of the various Netcat variants into a single, sophisticated tool. In addition, it includes several new features not available in the original Netcat tool, such as:
- Proxy connections via SOCKS4/SOCKS5 or HTTP proxies
- SSL connect/listen support and IP address/connection filtering
- Ability to “Chain” Ncat processes
- Connection brokering
- TCP/UDP redirection
Netcat can be installed on Debian/Ubuntu Linux distribution using the # sudo apt-get install netcat. Or on RedHat/CentOS distribution using the command: # yum install nc. On the other hand, Ncat comes with the standard Nmap download packages, which saves you the hassle of downloading it differently.
L’article 10 Best Linux Network Troubleshooting Tools for 2021 est apparu en premier sur Comparitech.

0 Commentaires