The critical facility that enables data loss prevention systems to block data theft is device control
“Device” is one of those words that can have multiple meanings in IT. For example, endpoints are often referred to as devices, and peripherals to endpoints are also called devices. However, in the world of data loss prevention, “device” refers to the peripherals.
Here is our list of the four best device control software:
- ManageEngine DataSecurity Plus This package provides a complete data loss prevention service in three interdependent modules. Control or block data transfers and protect files from tampering with this on-premises software for Windows Server.
- Endpoint Protector This package combines threat detection and data loss prevention and includes eDiscovery and access rights auditing as well as device controls. Deploy in the cloud or as a virtual appliance.
- Digital Guardian DLP This cloud platform includes monitors endpoints and networks to control data movements, and it is also able to enroll cloud services into its protection system. In addition, it contains peripheral devices, including USB ports, emails, printers, faxes, and file transfer utilities to manage authorized data movements. Agents are available for Windows, macOS, and Linux.
- Teramind DLP This cloud package offers threat detection and employee performance tracking as well as data loss prevention. In addition, the system includes controls over data exfiltration points through its endpoint agents.
You can read more about each of these options in the following sections.
Device control doesn’t just involve blocking all data movements onto those peripherals or disabling the interfaces – although those are two strategies that you could take. Instead, sophisticated device control lets some people move certain data types onto peripheral devices—the rules over who can move which data can be a complicated matrix of user groups and classes.
The foundations of device control
Device control doesn’t operate in isolation. That matrix of who can move what data has to be set up. Systems that include device control software also include automated methods to help build up that rule base, known as “security policies.”
A business can operate just one security policy. However, that is rare. So instead, the device control rule base is made up of a list of security policies.
To define a security policy, you need a user group from the access rights management system operating on the protected system and a list of data types.
The purpose of device control
Data loss prevention systems and their device control mechanisms are needed to prevent data theft. All of the data you hold on your system is necessary – otherwise, it would be deleted. Not only is that helpful information, but it has value. Although it might just be working data for your business that enables the enterprise to make money through its products, that data itself can earn money by itself for other people.
Many data thieves already have a high-paying buyer in mind – your company. News of the loss of data can severely damage the reputation of a business and lose sales and contracts. Paying thieves to keep quiet about the disclosure is often the cheapest way to deal with a data loss event.
If your business stores information on private individuals, called personally identifiable information (PII), it must comply with data privacy standards. Failure to protect PII can lead to fines, and it also exposes the business to litigation from those individuals to whom the stolen data relates.
Businesses that hold PII have to ensure that their suppliers that might need to process or store their PII are compliant with the relevant standard. Thus, if a data theft occurs and knowledge of that slip becomes public, your business would lose all of its contracts with companies following data privacy standards.
There are industry-wide standards in force in the USA and elsewhere that your company might need to follow. Examples of these are the Payment Card Industry Data Security Standard (PCI DSS) for the credit card payment processors and the Health Insurance Portability and Accountability Act (HIPAA), which pertains to the healthcare sector.
There are also location-specific standards. Examples of these are the EU’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). In these cases, there are also rules to follow over the location where data is stored and the location where those accessing the information are situated.
Creating security policies
The security policies that dictate how device controls should behave require a list of data instances that are deemed to be sensitive and a clean set of access permissions. Therefore, it is necessary to use an eDiscovery service to discover all data locations and then sort out which instances are sensitive, need to be protected, and do not need to be included in the program.
Implementing device controls over data also requires a more acceptable grade of access rights. Existing user groups in your access rights management system need to be split out so that users can be given access to just a specific type of sensitive data and possibly also just in one particular location. This access rights organizing task requires an auditing function.
Implementing device controls
The main focus of device controls is those peripherals that connect directly to the computer via a port. These days, USB connectors tend to dominate, and so USB devices are particularly of interest. Naturally, this category of devices includes memory sticks. In addition, however, some consumer products have a memory card and can connect via a USB port, such as digital cameras.
Peripheral devices don’t always have to connect directly to the computer by a cable. It is also possible to network these devices so that they can be shared among several computers. Devices in this category include printers and fax machines.
Typically, device controls extend to complete control of all data exfiltration channels. So, these tools also scan email attachments and chat apps. In addition, they will also constantly monitor network traffic for file transfer protocols, such as FTP and the secure versions, SFTP and FTPS. Unfortunately, secure transfer protocols protect the contents of the transfers with encryption, so the actual data payload of this traffic cannot be read. However, data loss protection systems can control access to the interfaces that launch these transfer systems.
The Best Device Control Software
It is rare to install a standalone device control tool because the groundwork that enables these systems to function is also required. Packages that include device control and all research functions that build up security policies are called data loss prevention systems.
What should you look for in device control software?
We reviewed the market for data loss prevention systems and analyzed tools based on the following criteria:
- A function that will scan all data exfiltration channels
- A supporting system of continuous sensitive data discovery and classification
- An auditor that reorganizes access rights management structures
- A library of pre-set controls for specific data privacy standards compliance
- Endpoint agents for all the major operating systems
- A no-cost assessment opportunity through a free trial or a demo system
- Value for money that provides a fully functional device control system as part of a data loss prevention package
We have created a list of suitable protection systems for sensitive data with these selection criteria in mind.
1. ManageEngine DataSecurity Plus
ManageEngine DataSecurity Plus includes three modules: File Server Auditing, Data Risk Assessment, and Data Leak Prevention. The File Server Auditing system provides file integrity monitoring, and the Data, Risk Assessment unit creates security policies by auditing access rights and discovering and classifying sensitive data. Finally, the Data Leak Prevention service is where device control is implemented.
The device controls in this package constantly monitor endpoints to detect any peripherals that get attached to them. This is mainly via USB ports. However, the system also scans network connections to other devices, such as printers and faxes. When any of these devices are detected, the controller monitors any data movements, following the security policies you set up. These policies can be preloaded from templates that satisfy specific data privacy standards.
Any endpoint with wireless capabilities can facilitate data transfer without needing the peripherals to be directly connected, so DataSecurity Plus also scans wireless systems, such as Bluetooth and WiFi, for data activity. CD and DVD drives are also monitored. The data controls extend beyond device activities to include the monitoring of email clients and chat apps. The service is also able to control data movements performed by file transfer utilities.
This system can enforce a complex web of data security policies that define which users can move or change which data. ManageEngine DataSecurity Plus runs on Windows Server, and you can get it on a 30-day free trial.
Pros:
- Discovery and classification for sensitive data
- Control of connected peripherals, wireless transfers, email, chat apps, file transfer utilities, networks printers and faxes, and removable storage.
- Preset security policies for standards compliance
Cons:
- No SaaS options
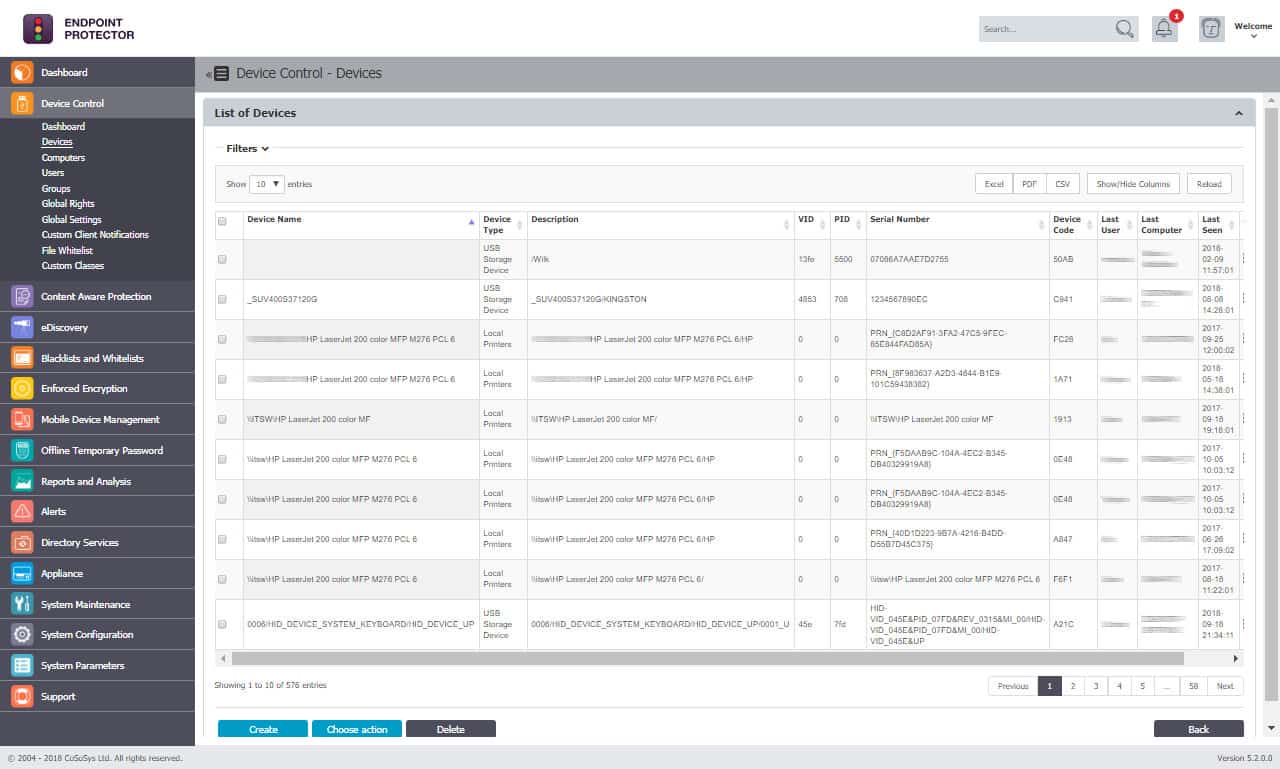
2. Endpoint Protector
Endpoint Protector combines threat detection with data loss prevention (DLP). The core of the DLP system is device control. The controls are implemented through the access rights manager operating on the protected system and an eDiscovery system.
The Endpoint Protector system is controlled from a central server and implemented through endpoint agents. These agents are available for Windows, macOS, and Linux. They can continue controls on peripherals and other data-related activity even when the endpoint is offline and uncontactable by the Endpoint Protector server.
The user accesses the dashboard for the DLP and sets up security policies, and it is possible to specify settings that implement specific data privacy standards by selecting a template. The server audits the on-site access rights manager and creates user groups that coordinate with the sensitive data categories that Endpoint Protector uses.
With these foundations in place, the Endpoint Protector server searches the network and discovers all endpoints. It then installs the agent programs and scans the devices for peripheral ports. If any devices are connected, they are logged. However, the agent will continue to watch and will spot new devices when they attach. The system will also monitor email and chat systems, file transfer utilities, and connections to printers and faxes.
The agents scan for data and identify those instances that are sensitive. These are then categorized for controls. With this task completed, data protection can begin. The data discovery cycle continues to operate, logging all new instances for protection.
Endpoint Protector is a good choice for a device control tool. It combines a local module for immediate controls, even offline, with a central coordinating server that spreads security policies across the enterprise. In addition, this system offers a range of deployment options from SaaS to cloud service and virtual appliance. Endpoint agents for Windows, macOS, and Linux cover all office systems.
Pros:
- Controls peripheral devices attached to endpoints plus networked printers and faxes
- Monitors data activities on email, chat apps, and file transfer utilities
- Includes a discovery and classification system for sensitive data
- Audits access rights permissions
- Offers templates for standards compliance security policies
Cons:
- It would be nice to have data throughput throttling
Endpoint Protector is available as a service on Azure, GCP, and AWS, and CoSoSys offer it as a SaaS platform from their servers. It is also possible to get the system as a software package for installation as a virtual appliance. Offered as a hosted SaaS platform and is also available as a service on AWS, GCP, and Azure. Alternatively, you can install the software package on-site over a VM. Finally, you can assess Endpoint Protector by accessing a demo.
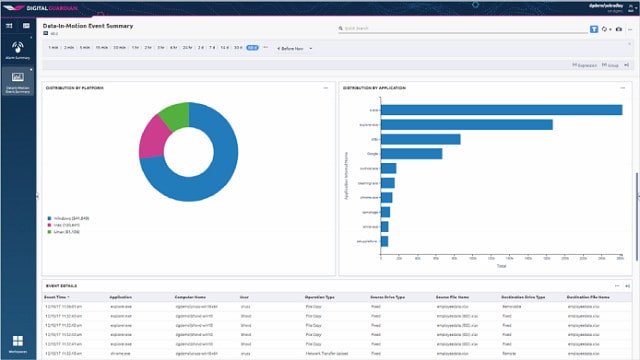
3. Digital Guardian DLP
Digital Guardian DLP is a cloud-based service that provides all of the elements of data loss prevention, including device control. As with the classic DLP strategy, rules are applied according to security policies formulated regarding access rights and sensitive data classification. In addition, the package performs both access rights auditing and continuous data discovery and classification service to support these requirements.
This service can unify the security monitoring of multiple sites and cloud resources. On-site devices are controlled by endpoint agents, which are available for Windows, macOS, and Linux. The Digital Guardian DLP system also implements network monitoring to catch unauthorized data transfers through email and file transfer services. This system aims to protect intellectual property as well as PII.
The service monitors USB ports, detecting whenever devices are connected. It will also scan connections to printers and faxes. Digital Guardian also includes a threat detection system that identifies insider threats and accounts takeover. You can assess the platform with a demo account.
Pros:
- Endpoint agents for Windows, Linux, and macOS
- Includes data discovery and classification plus access rights auditing
- Offers a library of security policy templates for data privacy standards compliance
Cons:
- The price is kept secret
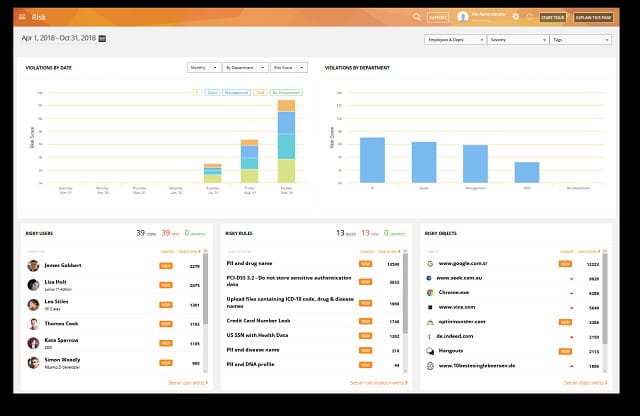
4. Teramind DLP
Teramind DLP offers three stages of protection. The data loss prevention system of Teramind is available in its highest plan. The lower plans are the Starter package, which provides user monitoring, and UAM, a user activity monitor looking for insider threats and account takeover. Each higher program includes the services of all lower editions, so you get user activity monitoring and user assessments in with the DLP plan.
The DLP system is suitable for businesses that comply with GDPR, HIPAA, ISO 27001, and PCI DSS. The service scans for instances of sensitive data and then categorizes them. This is the basis for the service’s security policies implemented through file integrity monitoring and device controls.
Teramind takes an inside-out approach to data controls because it tracks all users’ activities as its base process. It looks for abnormal behavior and applies those detection rules to the use of data in the system. In addition, the service includes a risk assessor and a data analysis service that helps you work out how you can better organize your security policies and data storage systems to improve efficiency while tightening security.
Teramind is a cloud service, and it also has an on-premises version. The SaaS package requires an endpoint agent to be installed on-site. These are available for Windows and macOS but not for Linux. However, the endpoint programs can run on VM. The on-premises version operates as a virtual appliance. You can assess the Teramind DLP system with a 14-day free trial.
Pros:
- A behavior-based data protection system
- Includes a sensitive data discovery and classification service
- Offers data privacy standards compliance
Cons:
- No software for Linux
L’article 4 Best Device Control Software and Tools est apparu en premier sur Comparitech.


0 Commentaires