Ethical hacking addresses the shortcomings of cybersecurity software. That is, the software is organized and can’t invent new methods to damage a system
On paper, the superior data processing abilities and execution speed that software has should defeat mere humans every time. However, hackers are clever and intelligent ingenuity is a crucial skill that software lacks. That’s why hackers often win against the automated defenses of computer systems.
Here is our list of the four best ethical hacking tools:
- Netsparker (ACCESS FREE DEMO) A continuous testing tool for development projects that can also be used as a vulnerability scanner for Web applications. Offered as a SaaS platform or for download onto Windows or Windows Server.
- Acunetix (ACCESS FREE DEMO) A vulnerability scanner for Web applications and networks searches for more than 7,000 external threats and scans from within a network for more than 50,000 vulnerabilities. Available as a SaaS platform or for installation on Windows, macOS, and Linux.
- Kali Linux This adaptation of the Debian Linux operating system has hundreds of hacking tools included with it. So if you want to perform ethical hacking and you don’t have Linux, get this distro.
- Havij An SQL injection and cross-site scripting service that also identifies databases and helps break into them. It runs on Windows.
You can read more about each of these options in the following sections.
The only way to ensure your system is protected against hacker attacks is to fight fire with fire. Ethical hackers are also called “white hat hackers.” They are hackers, but they have a different reason to break into your system. While hackers want to get in and steal money, ethical hackers want to get in to earn money. The only difference between the two types of hackers should be that the systems managers demand the white hat hacker attack.
An ethical hacker should be prepared to go to any lengths to break into a system. Therefore, in-house staff is not the best people to perform hacking attacks. Instead, you need outsiders who aren’t emotionally invested in the security of your system. However, if, out of curiosity, you want to test your system’s security yourself, you should pick up some of the ethical hacking tools that both hackers and white hat hackers use every day.
What are hacking tools?
Who makes hacking tools, and why aren’t they in prison? You would think that writing and distributing hacking tools should be some sort of crime, like aiding and abetting. However, many hacking tools are regular run-of-the-mill system testing tools. For example, for every system administrator and network manager user, Ping is a tool that hackers use. In addition, many of the command line information utilities you operate, such as ipconfig and arp, are hacker tools.
Information is power, and the first thing that a hacker needs is intel on your network – login credentials, in particular, would be helpful. Network discovery systems and port scanners are also very commonly used by hackers when they document a system on the search for a way in.
Another term for ethical hacking is penetration testing. An attack strategy can be planned to see how far into the tester system can get by acting like a hacker – how far they can penetrate defenses.
Hacking has been around for as long as computer systems, and so there are some ancient hacking tools out there that very old hackers use. These usually command-line utilities and use a Unix-like format with switches that feed in variables or activate options. A typical configuration for the launch of a hacker tool would be like arp -a.
Younger hackers have learned about those old tools, but they are more willing to adopt newer tools with GUI interfaces and interpret point-and-click instructions into operating system commands. So, there isn’t one single type of system that looks like a hacker tool.
The best ethical hacking tools
It is the job of an ethical hacker to act as a real-world hacker. Therefore, the best ethical hacking tools are those utilities that real-world hackers use.
What should you look for in an ethical hacking tool?
We reviewed the market for ethical hacking tools and analyzed the options based on the following criteria:
- A mix of command-line tools and utilities with a good GUI
- Systems that conduct research and offer support to attack strategies
- A service that can guide what system weaknesses provide the best opportunities
- A system that logs all actions for later analysis
- A mix of free and paid tools
- A chance to assess paid agencies without cost
- A fair price that gives value for money or a free tool
As well as following these selection criteria, we made sure to find tools for each operating system. We also included tools that can contribute to an attack campaign in part. The majority of the ethical hacking tools that we recommend you to try our bundled into Kali Linux.
The Four Best Ethical Hacking Tools
1. Netsparker (ACCESS FREE DEMO)
Netsparker is a vulnerability scanner for Web application exploits. Tests are launch through a browser with a crawler, and they can be run on-demand or set up for continuous testing. The scanner runs through the CVE list of known exploits, and it also applies heuristics to spot possible combinations of utilities that could be used to launch an attack.
Each scanning run can be customized to only focus on specific Web applications and also to only search for specific exploits. In addition, it is possible to set up parameters for the test in the settings screen of the tool, so you could work out, through trial and error, which values would trigger weakness and compromise the application.
Pros:
- A fast vulnerability scanner for Web applications
- The choice of on-demand and scheduled scans
- The ability to alter the parameters for a test
Cons:
- The system doesn’t offer internal network testing
Netsparker is available as a SaaS platform and also for installation on Windows and Windows Server. Assess the Netsparker service through its demo system.
2. Acunetix (ACCESS FREE DEMO)
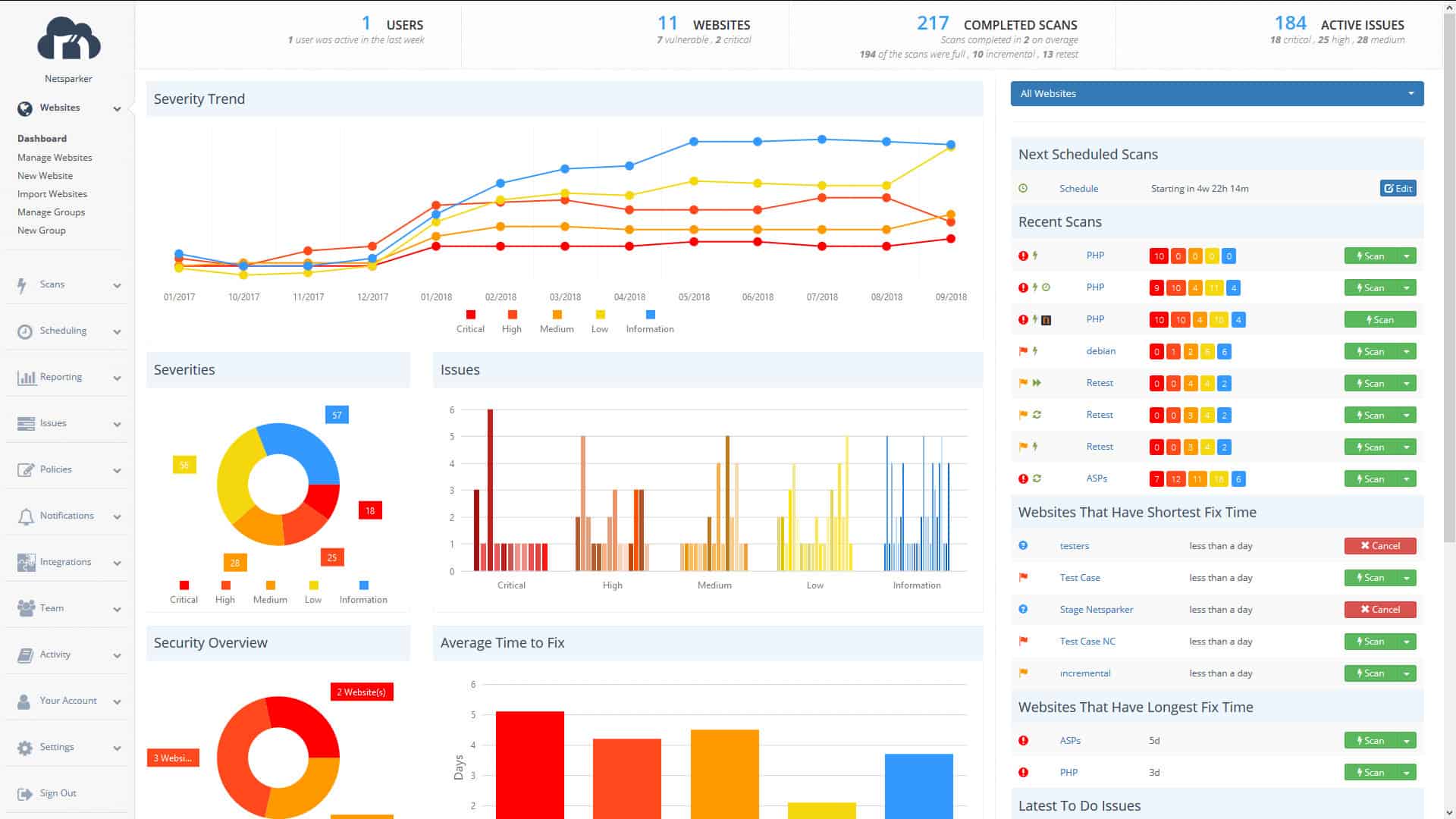
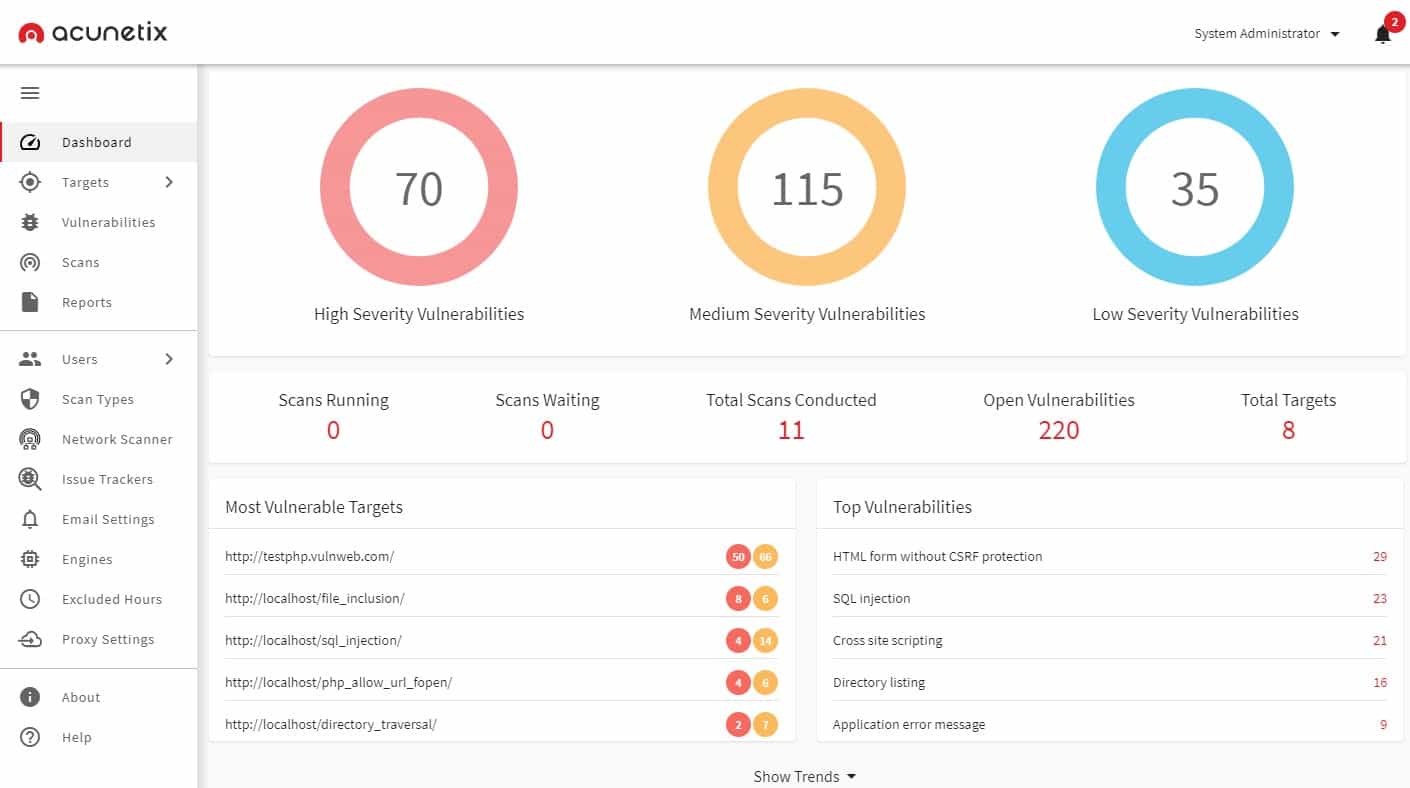
Acunetix is a vulnerability scanner that identifies threats to Web applications and networks in an ethical hacking research sweep. The system can scan a network from an external viewpoint and then perform an internal vulnerability sweep.
It is available in three editions. The first of these is called Standard, and it only allows for the external scan of networks and Web applications. This provides on-demand vulnerability scanning. The middle edition, called Premium, is the one to go for if you need an ethical hacking tool. This scans for 7,000 external threats and also looks for 50,000 exploits from within the network.
This tool is also capable of providing continuous testing for applications under development. The highest plan, called the Enterprise Edition, is mainly a testing system for development projects, including the Web application vulnerability scanner.
Pros:
- Performs external and internal network vulnerability scans
- Scans for Web application vulnerabilities
- Offers both on-demand and continuous tests
Cons:
- Can’t launch attacks
Acunetix is available as a hosted Software-as-a-Service platform. It can also be installed on Windows, macOS, and Linux. Try Acunetix by accessing a demo system.
3. Kali Linux
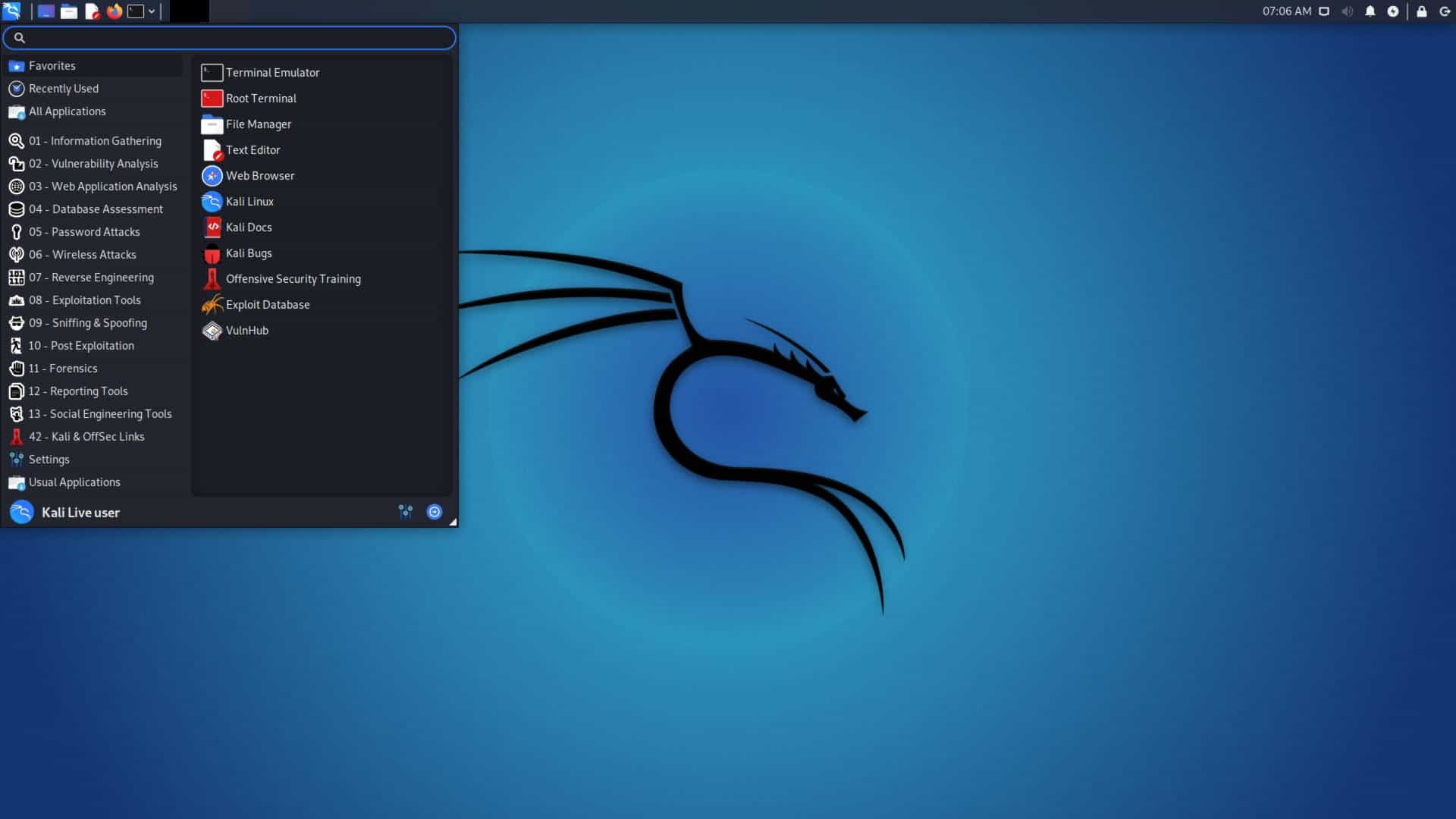
Kali Linux is an operating system with added features. It is a version of Debian Linux with hacking tools already built-in. This is the quickest way to acquire a complete hacking toolkit for testing your system’s security. This fantastic pack of ethical hacking tools is completely free to use. These are not demo versions or free trials. Every tool in the Kali Linux system is free forever – no tricks.
There are around 300 tools included in Kali Linux, and you will probably never use most of them. This is not because they aren’t any good – every tool in the Kali package has been tested and recommended. However, there are many tools in each hacker tool category, so you will probably try out one tool, and then, if you like using it, you won’t bother with all of the tools in the package that perform the same task.
As you read through descriptions of each of the tools included with Kali Linux, you will already get an idea of which will probably work well for the penetration testing strategy you are creating. The great thing about deciding on ethical hacking tools in the Kali list is that you don’t have to download anything, and you can’t make a mistake when installing it – it is already there.
Kali Linux tools fall into the following categories:
- Information Gathering
- Vulnerability Analysis
- Exploitation Tools
- Wireless Attacks
- Forensics Tools
- Web Applications
- Stress Testing
- Sniffing & Spoofing
- Password Attacks
- Maintaining Access
- Hardware Hacking
- Reverse Engineering
- Reporting Tools
There are command-line tools and tools with a GUI interface in each category. None of the tools belong to Kali Linux – they are not exclusive. You can download each of the tools in Kali Linux individually for free. Many of the tools are available for other operating systems from their websites. All of them are guaranteed to run on other Linux distros; nearly all of them will run on Unix, most of them are available for macOS, and quite a lot of them are also available for Windows.
If you think that downloading and installing 300 tools is overhead because you really won’t use all of them, you will get just as much use out of previewing the tools you like and just download those onto your existing operating system.
The complete list of Kali Linux tools will help you in your selective research. You can also look at our Kali Linux Cheat Sheet, which has a download-and-keep PDF list of Kali tools embedded in it.
Some of the widely used ethical hacker tools included in Kali Linux are:
- Metasploit Framework This tool is very widely used by hackers. It works through a customized command line window and offers brute force credentials cracking and facilities for manual attacks. This system can be used to try to get into a network. It is available for Windows, macOS, and other Linux distros apart from Kali Linux.
- Armitage This is an excellent adapter for Metasploit Framework. It offers a front end for the command line Metasploit system and manages attack campaigns against one or several endpoints. If you want to get it outside of the Kali package, it is available for Windows, macOS, and other Linux distros.
- Burp Suite Community Edition This is an excellent tool for both intel and attacks. You gather information about a target in one tab of the interface and then copy it to another tab to run a raid. This system runs attacks on Web applications and can perform traffic interception if it is within the network. In addition, this system can perform a replay attack, flood a network, read packet contents, and perform brute force password cracking, among its attack strategies. Apart from Kali Linux, Burp Suite Community Edition can be hosted on other Linux distros plus Windows and macOS.
- John the Ripper This is a password cracker. The package includes brute force password guessing and decryption attempts. Create your password dictionary or import one from another tool. This is a command-line tool that will also run on other Linux distros and macOS.
- Hashcat A password cracker that specializes in decoding hashing algorithms. It is very successful in its efforts. This is a command-line utility that is also available for other Linux distros, Windows, and macOS.
- Aircrack-ng A command-line system that detects wireless networks and captures packets from them. This package can also be used to inject packets into a stream or re-broadcast traffic. In addition, it can send out a deauth command and perform a man-in-the-middle attack. Apart from Kali Linux, this utility is available for other Linux distros and Windows.
- Sqlmap This command-line utility specializes in identifying and breaking into databases. It can crack passwords, implement Web application SQL injection attacks and also steal or alter data. Read about this tool in greater detail in the Sqlmap Cheat Sheet. Sqlmap installs on Windows, macOS, and other Linux distros.
- Nmap is a network discovery tool. It is very widely used, but its main problem is that it is just a command-line tool. Zenmap, also included with Kali Linux, provides a graphical front end to the Nmap engine. Nmap is also a packet sniffer. You can install both utilities on other Linux distros, Unix, Windows, and macOS.
- Wireshark is a packet sniffer for LANs and wireless networks. The utility has a GUI interface, and there is a command-line version called TShark. You can feed packet capture files from Wireshark into other utilities for analysis. It runs on Windows, macOS, Unix, and other Linux distros.
The above list shows just a few of the best tools in the Kali Linux package. There are many other excellent free ethical hacking tools in the bundle.
Pros:
- A huge bundle of hacking tools
- A version of Debian Linux included
- Completely free to use
- Tools for system investigation and to launch attacks
- System documentation tools
Cons:
- You will be hosting the code for a lot of tools that you will never use
Kali Linux is a fine pick for an ethical hacking system because it includes around 300 tools known to be used by hackers. What’s more, this package of tools gives you an operating system, yet it is still free with all of those features. Kali Linux would be a good choice if you decided to set up a computer dedicated to ethical hacking activities because you can install Kali Linux on a bare-metal system.
Download Kali Linux for free: kali.org/get-kali/
Operating system: Bare metal
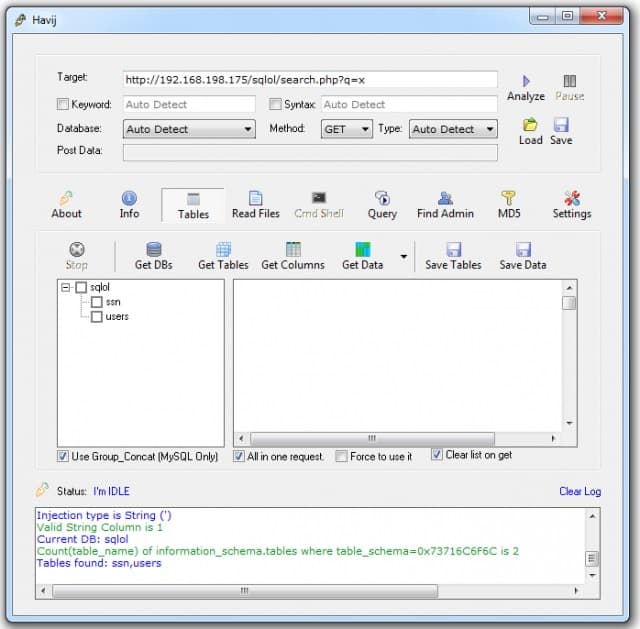
4. Havij
Havij offers SQL injection and database attacks in a very similar way to Sqlmap. Havij is older than Sqlmap, and it is available for Windows. A significant advantage that Havij has over Sqlmap is that it has a GUI interface. The screen for Havij has buttons on it that enable you to switch between available functions and attack strategies.
Havij first scans a website or API and probes it for a database behind the scenes. It can work out which type of DBMS runs the database and scan for possible user names. The package includes a credentials cracker. Once in, the tool can extract the database structure, offering a list of tables, which can be queried further to extract data.
Pros:
- An easy-to-use graphical interface
- The ability to scan websites and discover the supporting DBMS
- Facilities to break into databases and extract data
Cons:
- The code hasn’t been maintained for a long time
Havij is free to use.
L’article 4 Best Ethical Hacking Tools for 2021 est apparu en premier sur Comparitech.
0 Commentaires