Arachni is free to use. It is an automated security scanner for Web applications, and it can be used for penetration testing or development testing. This tool has been around for ten years. However, its development has been slow and is probably not your best bet if you look for a vulnerability management system for a business’s Web assets.
This review will find out more about Arachni, how to use it, and what alternatives are available.
The history of Arachni
The history of Arachni starts with Tasos Laskos. He studied an MSc in Cyber Security at the Royal Holloway College of the University of London and, as part of his thesis for that course, wrote Arachni. The system worked well, so Laskos decided to make his tool available to the broader community by placing the code on GitHub and making it an open-source project.
Over the years, Laskos has struggled to get Arachni noticed, and he set up Sarosys LLC to commercialize the product and help fund the project. As the sole developer for Arachni, Laskos found it difficult to devote enough time to its development. The last update of the system was released in 2017 with version 1.5.1.
In January 2020, Laskos announced on the Arachni website that Arachni is no longer maintained. It seemed that he had finally abandoned his project. In June 2021, he released a new announcement that he is now working on a replacement for Arachni.
Arachni deployment options
Although having read that Arachni has been abandoned, you might be tempted to hurry straight down to the Alternatives section, and it is worth a look.
Arachni has a command-line interface and also a Web GUI. The package is available for Linux (32-bit and 64-bit), macOS (64-bit), and Windows (64-bit). The Arachni Download page recommends the Linux and macOS versions over the Windows implementation.
The host needs at least 2 GB of available RAM and a spare 10 GB of disk space.
The download file for the system is an executable that will unzip the code and install it as a subdirectory of wherever you downloaded the package to. For example, if you downloaded it to the Downloads folder on Windows, the entire system will be set up beneath that directory. The code tree will be in the subdirectory arachni-1.5.1-0.5.12-windows-x86_64.
Using Arachni
The Arachni system is implemented as a series of batch files. Initializing a total scan of a Web asset launches all of the batch files in sequence, each executing a different test vector. This is a series of pen testing attempts covering a full range of exploits, including HTTP GET attacks, SQL injection, code injection, cross-site scripting, and so on. There are a total of 40 modules that provide a set of passive checks and active attempts. Each module will run through many permutations of possible inputs to test its particular topic of inquiry. All of this work can take a long time to run.
Running the system from the command line results in a text-based report displayed on the screen.
This report is also saved to an AFR file. This is a native binary format – AFR stands for Arachni Framework Report. The file can be converted into various formats, such as XML, plain text, and HTML.
The other method of access to the scanner is through its Web-based GUI. Unfortunately, this is not very well documented in the Wiki for the system, and I almost gave up. However, if you know how to launch it, your assessment of Arachni will improve exponentially.
To get the GUI running, you need to open a Command Prompt window, go to the home directory of Arachni on your computer, and enter bin\arachni_web. You will see a message telling you that the listener is running on localhost:<port> — you will see a number instead of <port>. Go to your browser and enter that address in the address bar (e.g., localhost:9292). This opens the Web interface. You need to log in, giving the username admin@admin.admin and password administrator.
This leads to the launch page for the scanner, which gives you a range of options. I left all of the defaults for a test and specified a Direct mode scan of the Arachni website at https://ift.tt/3um05lD.
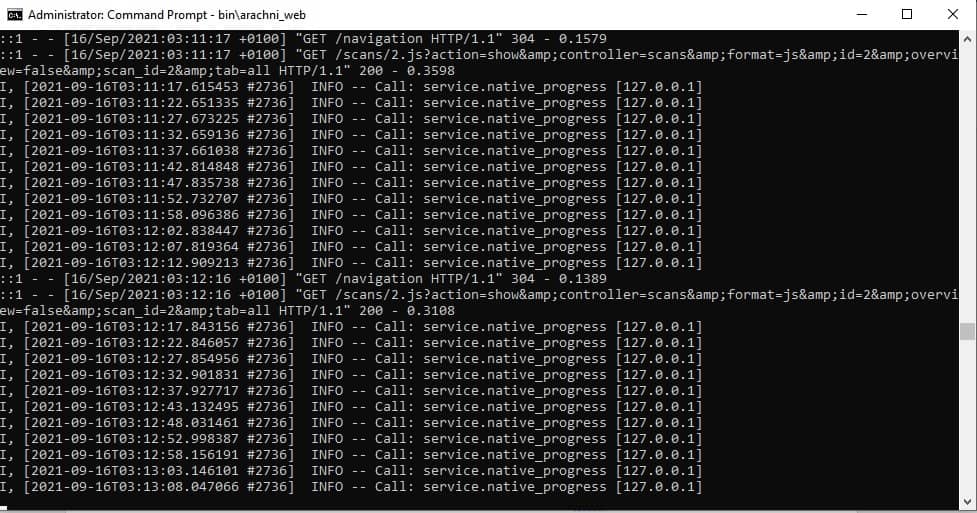
As the test run progresses, a stream of feedback messages will pass by in the Command Prompt window:
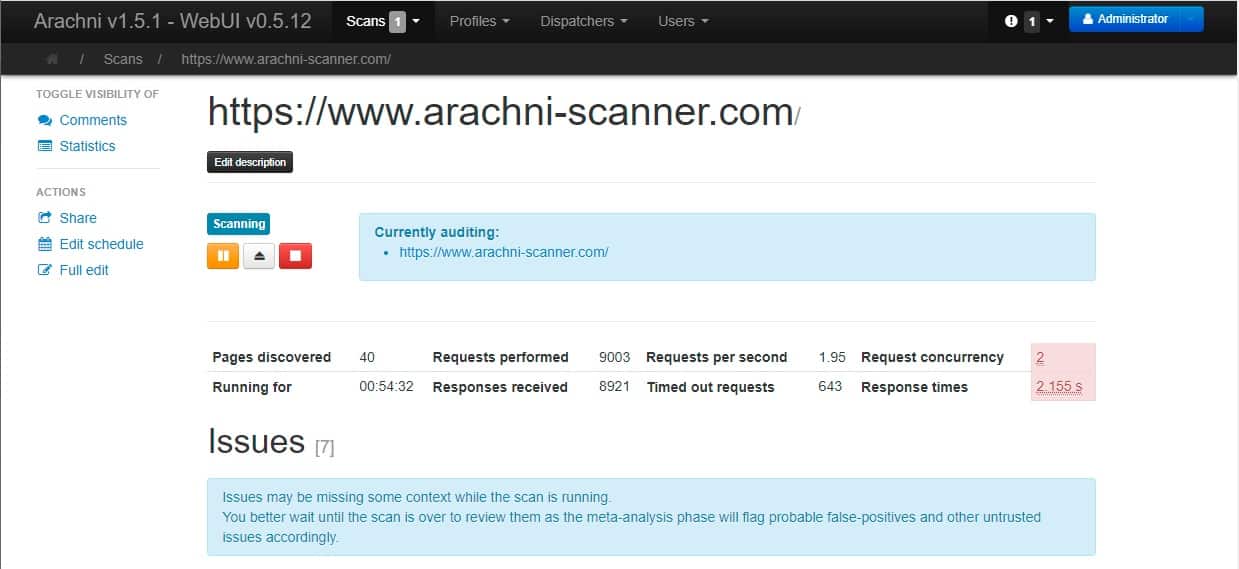
The Web interface gives a live progress report:
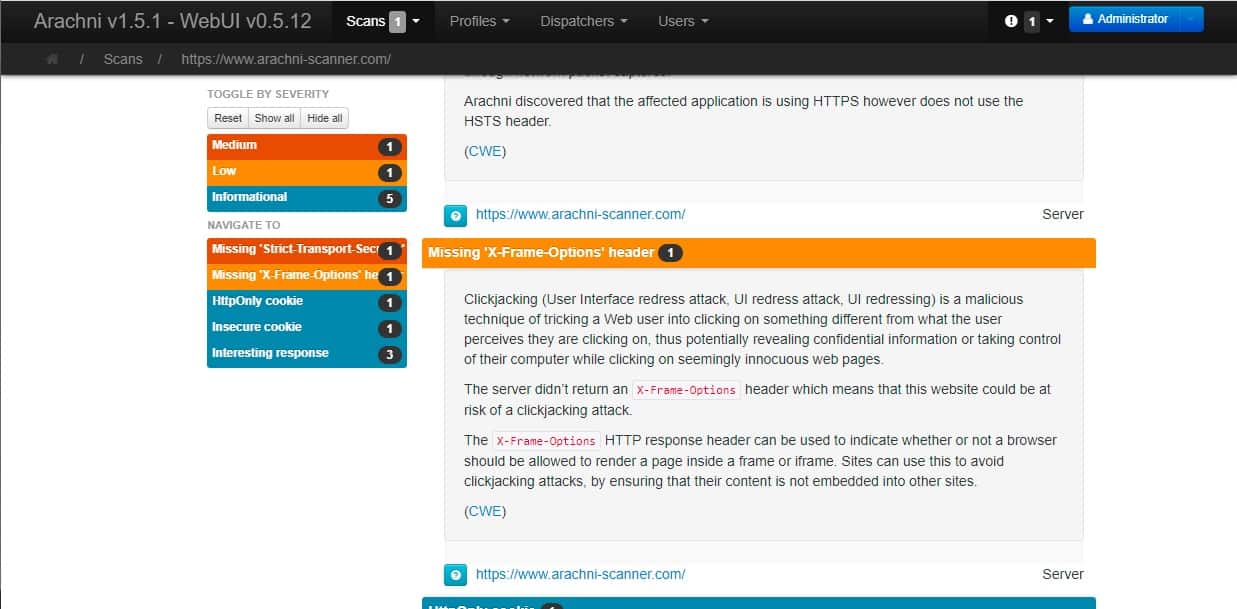
The lower part of the scan report shows the number of problems encountered by type. Clicking on a category gets an explanation of the kind.
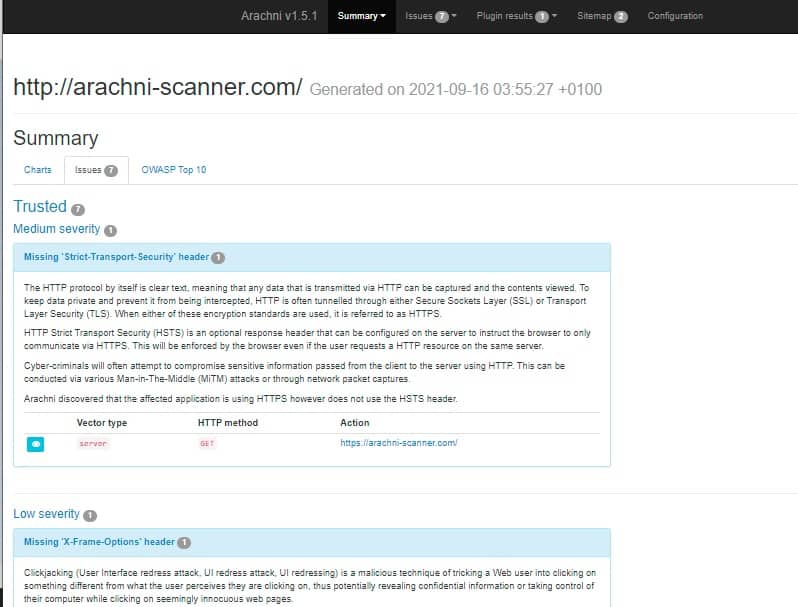
Although creating the scan results in the AFR format is an obscure choice, the utility arachni_reporter can convert that report into HTML format. The results are impressive. Here are the results produced by a scan of the arachni-scanner.com site.
The front tab of the report shows interactive charts based on the scanner’s findings.
An Issues tab shows each of the vulnerabilities that were identified.
Further details on each problem can be found by clicking on the line in the Issues report. The system also explains the error and a description of the exploit as given by OWASP.
Overall, the reporting system of Arachni is awe-inspiring.
Arachni strengths and weaknesses
Arachni is difficult to get to know because the Wiki guide is not very comprehensive. However, once you manage to stumble around the system and get to know its operating structure, you should find it an impressive service.
There are several good points and bad points to note about Arachni.
Pros:
- Progresses through all of the critical tests for the OWASP Top 10
- It has both a command-line interface and a browser-based GUI
- Offers a range of testing modes
- Impressive report output with insightful explanations
Cons:
- It hasn’t been updated since 2017
- No support
- The project has been abandoned
- It takes a long time to run
Arachni is a series of penetration testing exercises implemented as batch files and strung into a single chain that can be launched with one command. However, a vulnerability scanner is precisely that – an automated pen-testing session.
This system was developed as a student project by one person and promised to be a commercially viable tool. The developer put in a lot of work on this package, and, unlike many enthusiast-created systems, it works and doesn’t have any bugs. Many heritage pen-testing tools and vulnerability scanning tools of a similar age to Arachni no longer work or have been made obsolete by advancements in technology. Arachni does not fit into that category – it still works, and its results are insightful.
It is a shame that Tasos Laskos didn’t manage to put together a team and a proper project framework to keep Arachni alive. Undoubtedly, given all of the work he has done in creating this excellent tool, he felt underappreciated and defeated by the tremendous effort it takes nowadays for a product to get noticed in the marketplace.
Here’s hoping that Laskos’s replacement for Arachni gets off the ground.
Alternatives to Arachni
Arachni is a fascinating tool and would be of particular interest to students of InfoSec and trainee pen testers. However, the project has been abandoned means that it can’t be considered a viable candidate for use in a commercial environment. So if you are looking for a tool to perform vulnerability scanning or production testing of Web applications under development, you need to keep searching.
What should you look for in an alternative to Arachni?
We reviewed the market for vulnerability managers and Web application testers like Arachni and assessed the options based on the following criteria:
- A self-installing package
- An easy-to-use system that offers a graphical interface
- A service that automatically scans for Web application exploits, particularly the OWASP Top 10
- A service that can be used by system administrators who are not specialists in cyber security
- A tool that can be applied to development testing as well as vulnerability scanning
- A free tool or a system that offers a free trial or demo for assessment
- A commercial-grade service that is fully supported and frequently updated to keep the tool relevant and value for money
With these selection criteria in mind, we have put together a list of some excellent application security testers and vulnerability scanners that match the functionality of Arachni while also providing professional support.
Here is our list of the five best alternatives to Arachni:
- Netsparker (ACCESS FREE DEMO) This service can operate as a vulnerability scanner and also as a development test environment. Options for this tool allow on-demand scanning, or you can set up a schedule. Netsparker specifically tests Web applications, and it can be set up to run continuously for Web application development teams. The service scans code as well as running interactive elements. The Netsparker strategy looks for logical errors that can expose data or give hackers entry points. This is a highly professional service that is supported around the clock. Netsparker is a SaaS platform, but it is also possible to get the package for installation on Windows and Windows Server. Access a demo system to assess Netsparker.
- Acunetix (ACCESS FREE DEMO) This is another service that can be used as a vulnerability manager or continuous testing in a development environment. Three editions tailor the deployment of this system. The tool offers Web applications scanning for more than 7.000 vulnerabilities, and there is also an option for network vulnerability scanning that has a list of 50,000 weaknesses to look for. Acunetix is available as a SaaS platform or for installation on Windows, macOS, or Linux. Whichever package you choose, the services of a 24-hour Help Desk are included in the price. Access a demo system to check out Acunetix.
- Detectify Deep Scan This is an automated testing system that was assembled by a team of ethical hackers. In many ways, this history reflects that of Arachni, which a white-hat hacker created in training. The Detectify team acquires a more incredible list of exploits than most scanners have by offering freelance researchers a commission if their exploit discoveries are added to the vulnerability database of this scanner. Detectify can be used for development testing or vulnerability scanning. In both cases, it looks at Web applications. Detectify is available for a two-week trial.
- Veracode Dynamic Analysis This is a dynamic application system testing (DAST) package that can be used in a CI/CD pipeline, offering continuous testing or acting as a vulnerability scanner for live systems. The basic scanning service is straightforward to use. The tool is hosted and provided as a SaaS platform, so you don’t have to install any software. You just enter the URL of a Web asset into the dashboard and start the scan. Tests can be expanded and customized through a built-in scripting language. Veracode Dynamic Analysis can be integrated with issues trackers and project management tools to automate resolution workflows. The service can be assessed by accessing its demo system.
- Syxsense Secure This system hardening bundle includes a vulnerability manager, endpoint detection and response service (EDR), a port scanner, a patch manager, and a configuration manager. The EDR installs on endpoints running Windows, macOS, and Linux. This tool also acts as an agent for the other systems in the package, which are all cloud residents. You access this service through its SaaS portal. The bundle also includes cloud storage space for patch installers and log files. Syxsense Secure is available for a 14-day free trial.
L’article Arachni Review & Alternatives est apparu en premier sur Comparitech.



0 Commentaires