Unrestricted USB ports are a massive security risk for any environment. Whether you’re trying to prevent infection or data theft, reliably locking down USB access without preventing legitimate work can seem impossible.
We tested and reviewed seven of the best USB lockdown software tools to help sysadmin balance security and productivity in their environment. Let’s get started.
Here’s an overview of our top choices for the best USB lockdown software tools:
- ManageEngine Device Control Plus Offers comprehensive USB lockdown with scalable device control features
- Endpoint Protector by CoSoSys Robust enterprise device control solution
- USB Lock RP Uses lightweight agents and supports legacy environments
- DriveLock Offers device control through a sleek minimalist design with end-user training
- GFI Endpoint Security Provides device control as a part of the GFI Unlimited Suite
- DeviceLock Offers device control and DLP that can identify advanced data theft by reading text from images
- Safetica Uses behavioral analysis to identify insider threats while pushing out device control policies
How does USB lockdown software work?
USB lockdown software (also known as device control) stops unauthorized or unknown devices from interacting with endpoints that contain sensitive data. This approach uses endpoint security agents to monitor the environment, enforce policies, and record what data has been moved, if any.
This management allows the sysadmin to scale their device policies and protect endpoints from insider threats, data theft, and BadUSB. In addition, USB lockdown software often does more than just restrict access to USB ports, which is good news for administrators.
Robust device control solutions will offer USB lockdown software as an option and provide sysadmin with more granular control. Device whitelisting, transfer limits, one-time passwords, and encryption are just a few of the features offered by enterprise device control.
Organizations can leverage this technology to protect themselves from accidental or malicious data loss and build data protection workflows that adhere to specific security standards such as PCI DSS, FISA, or HIPAA.
What is Device Control?
Device Control is the act of controlling what kind of hardware is allowed to interact with your managed endpoints. Device Control encompasses all devices, including USB ports. Many platforms offer USB lockdown as a part of their device control solution so that you may hear the two terms used interchangeably. However, if you’re looking for a specific feature such as timed delay USB access, it’s important to specifically ask the vendor if their device control solution supports it.
What should I look for in USB lockdown software?
Control Features
USB lockdown software should have plenty of options for administrators to restrict access rather than a single on or off switch. In reality, people need to get work done. A USB lockdown software that denies staff access to their work materials won’t last long. Having granular control in place allows administrators to implement layers of security that reduce risk while allowing staff to remain productive.
Options for mandatory encryption, time restrictions, and configurable policies are essential for a successful device control policy. Start with your goal in mind and identify the features you’ll need to carry out that goal. For instance, mandatory encryption can help staff move data protected by compliance regulations, while time restrictions can prevent after-hours data theft and restrict BYOD environments.
Lastly, identify tools that have configurable levels of permissions or groups. For instance, a USB lockdown software that continuously prevents the CEO from accessing files would be frustrating. Instead, by integrating with systems such as Active Directory, sysadmins can use their existing permission architecture to build a solid but flexible USB lockdown policy that suits their needs.
Visibility
Device Control software should give administrators an overview of their protected devices and log what data has been moved and by whom. When the data transfer is authorized, keeping track of who accessed it and where it can be vital to investigate a data theft incident or fraud. Ensure your solution can log these actions in case an investigation requires this information.
Visibility also helps sysadmin understand their environment and how protected each endpoint is. For example, many USB lockdown software tools have centralized consoles that overview compliant machines, whitelisted devices, and possible issues. This visibility helps organizations scale their device control efforts by assigning NOC teams to handle problems or input this data into a SIEM for the historical record.
Integration
While most USB lockdown software works as a standalone solution, having the option to share insights between platforms is essential for long-term success. For instance, having a device control platform with a robust API library allows an organization to scale alerts to a ticket system down the road. Integrations also help keep team members in the loop. For example, a flexible integration may allow instances of confirmed data theft to notify NOC teams and a manager via text immediately.
These same integrations can sometimes also support automated scripting. If the device control platform doesn’t support automated response, often, an integration can enable automatic actions such as locking a user account or quarantining a machine from the network.
The best USB Lockdown software
With these critical features covered, let’s examine some of the best USB lockdown software tools on the market today.
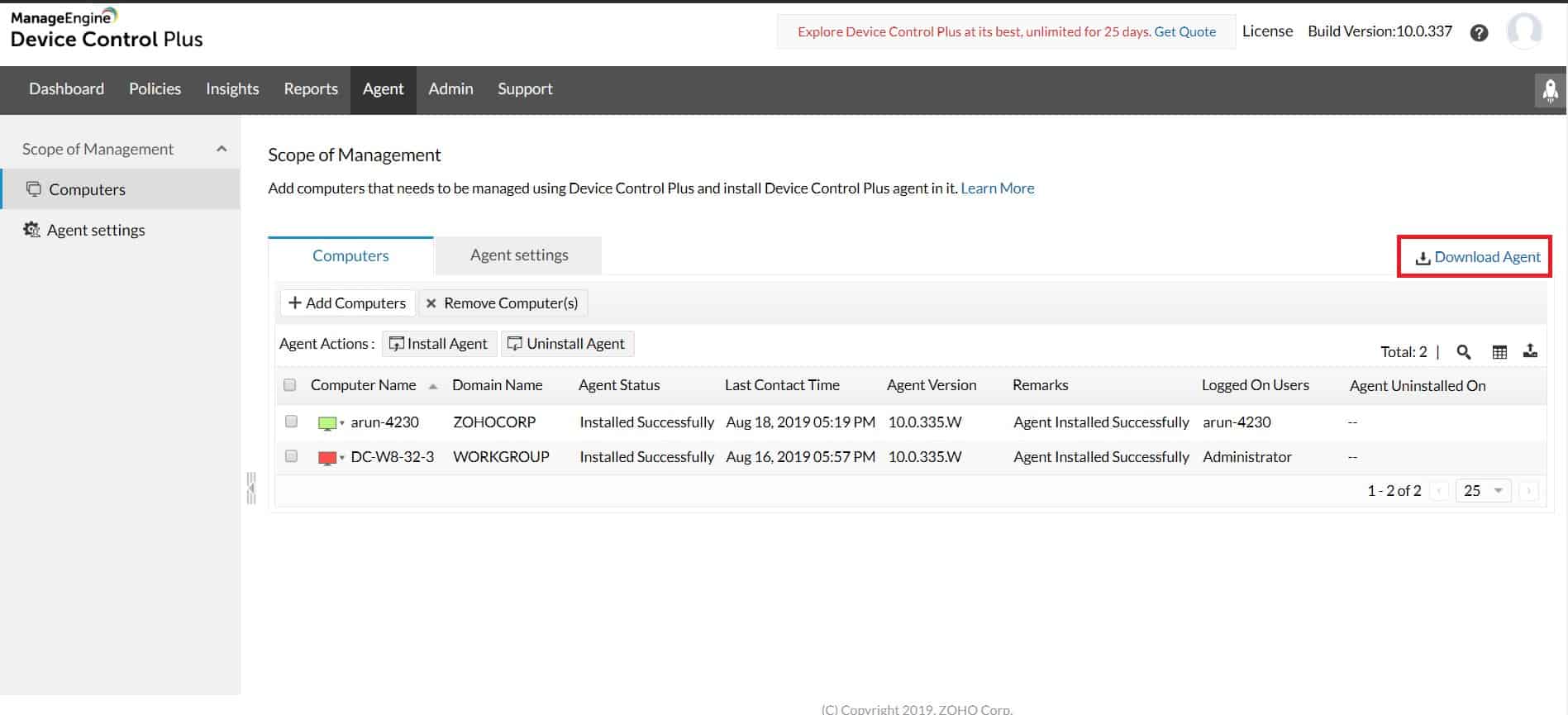
1. ManageEngine Device Control Plus
ManageEngine Device Control Plus is designed for enterprise control and supports both BYOD and company asset management. The platform offers administrators numerous options for device control while uniquely offering several features out of the box that makes onboarding quick and painless.
The platform goes beyond simple USB lockdown software by providing Data Loss Prevention (DLP) features to stop data leakage and detect the early signs of insider attacks. Sysadmins can create zones to set up read-only access, identify devices with overarching privileges, and automatically push out policies to new devices.
Transfer control can be established to identify suspicious file transfers by metrics like size, file type, and location. This helps prevent the theft of data and provides context into why that data was accessed in the first place. Rather than working backward to restrict access, ManageEngine Device Control Plus uses a Zero Trust approach that relies on a trusted device list to allow different access levels.
For situations where staff need special access, one-time access can temporarily be given to that user with privileges that revert after a certain amount of time. The platform also understands user behavior over time to create a baseline of everyday work. It uses this data to identify suspicious activity and highlight possible insider activity when anomalies arise. Threat activity can either launch automated scripts or send an alert notification via integration. This works well for both smaller teams and larger organizations that send alerts to a helpdesk queue.
Lastly, the platform has an intuitive dashboard that makes it easy to view the status of all managed endpoints and track critical alerts historically and in real-time. ManageEngine Device Control Plus offers a comprehensive approach to USB lockdown for both medium and enterprise-sized organizations.
You can test out ManageEngine Device Control Plus through a free 30-day trial.
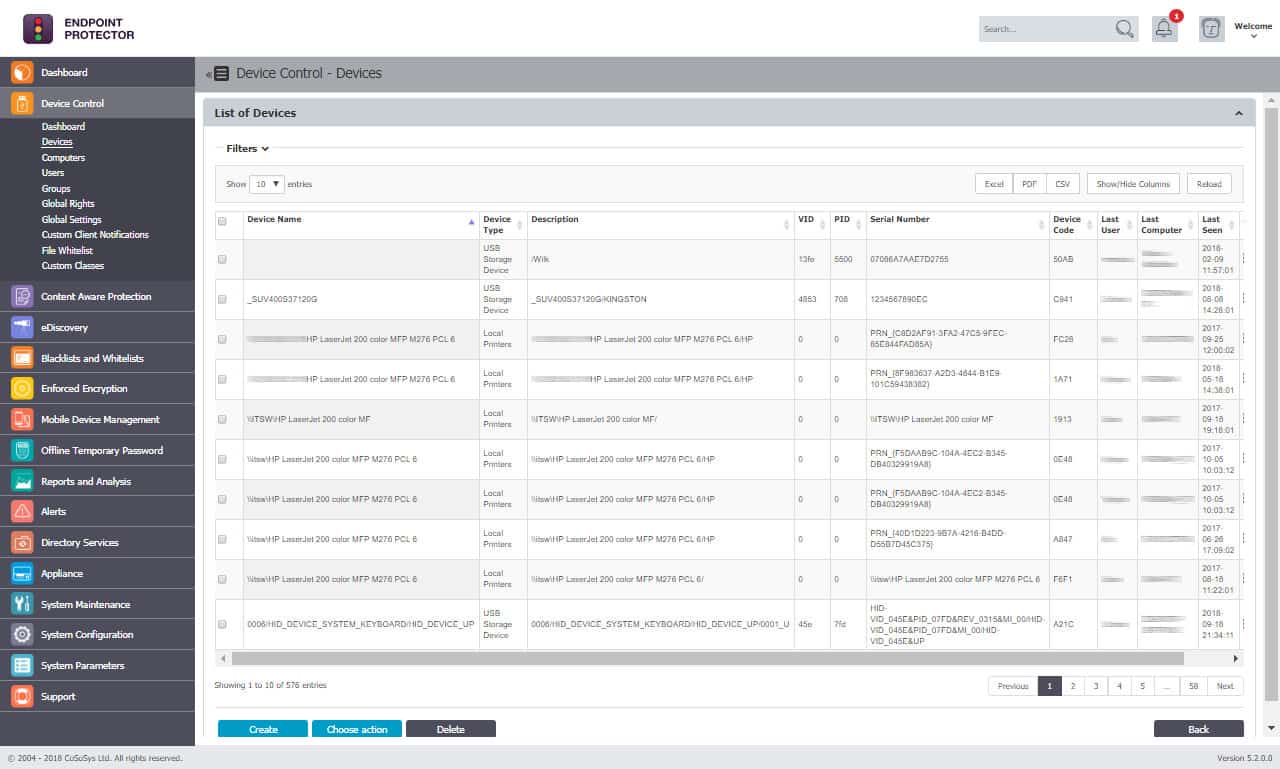
2. Endpoint Protector by CoSoSys
Endpoint Protector is an industry-leading DLP platform that provides cross-platform protection. The brand focuses heavily on controlling sensitive data transfer, storage, and recovery with detailed USB lockdown options.
It can be challenging to start over with a zero-trust policy for device control in large busy environments. Therefore, when taking a whitelist approach, it’s essential to have various options from which to build your trusted list.
Endpoint Protector identities this problem provides sysadmin with numerous ways to lock down, manage and monitor devices across the enterprise. For example, users can create rules and groups via LDAP based on vendor ID, product ID, serial number, and existing permission groups. In addition, the platform takes a unique approach to protect data through content-aware scanning and enforced encryption.
Content-aware protection helps the system understand context based on the action, user, and type of data accessed. This provides a strong starting point for administrators to build additional policies, helping save time during the onboarding process.
Automatic USB encryption ensures that data leaving your environment is encrypted, no matter which device it goes on. Enforced encryption helps keep companies compliant by providing data is encrypted both in transit and while at rest. From an end-user perspective, this procedure is password-based and only adds a single step to their workflow.
Endpoint Protector’s combination of device controls, DLP options, and encryption settings make it a valuable tool for any business looking to secure their data and prove compliance. You can test out Endpoint Protector by requesting a demo.
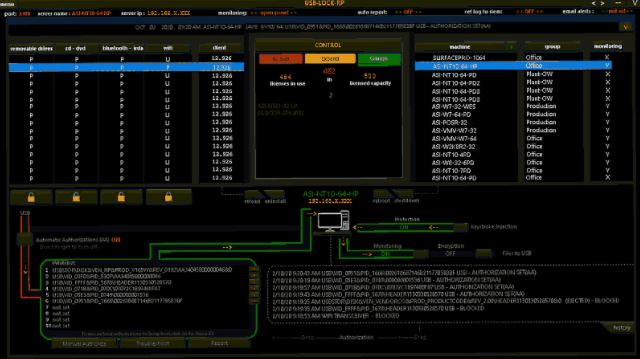
3. USB Lock RP
USB Lock RP is a device control platform with a focus on controlling and locking down USB ports. It provides centralized USB management through a sleek dark-mode dashboard and empowers administrators of any size network to manage their data more effectively.
The platform uses a lightweight agent to control endpoints and push out policy enforcement, making it highly scalable and viable for legacy devices with limited resources. The enforcement automatically detects hardware IDs to allow only specific USB devices without restricting other peripherals like speakers or printers.
Policy enforcement works on the system level to stop unauthorized devices from transmitting or receiving data, ideal for preventing data theft and infection. In addition, automatically blocking unknown devices creates a secure environment by default and helps reduce unnecessary scans of new hardware when plugged in.
The platform can scale to support up to 5000 devices and supports basic logging and data exports in CSV format. In addition, users can add blocking screens complete with their company logo, opening the possibility for MSPs to resell this product as a managed service.
USB Lock RP is a viable solution for both small and large networks alike. With its lightweight agent and support for legacy systems as old as Windows NT, this tool is both as flexible as it is powerful.
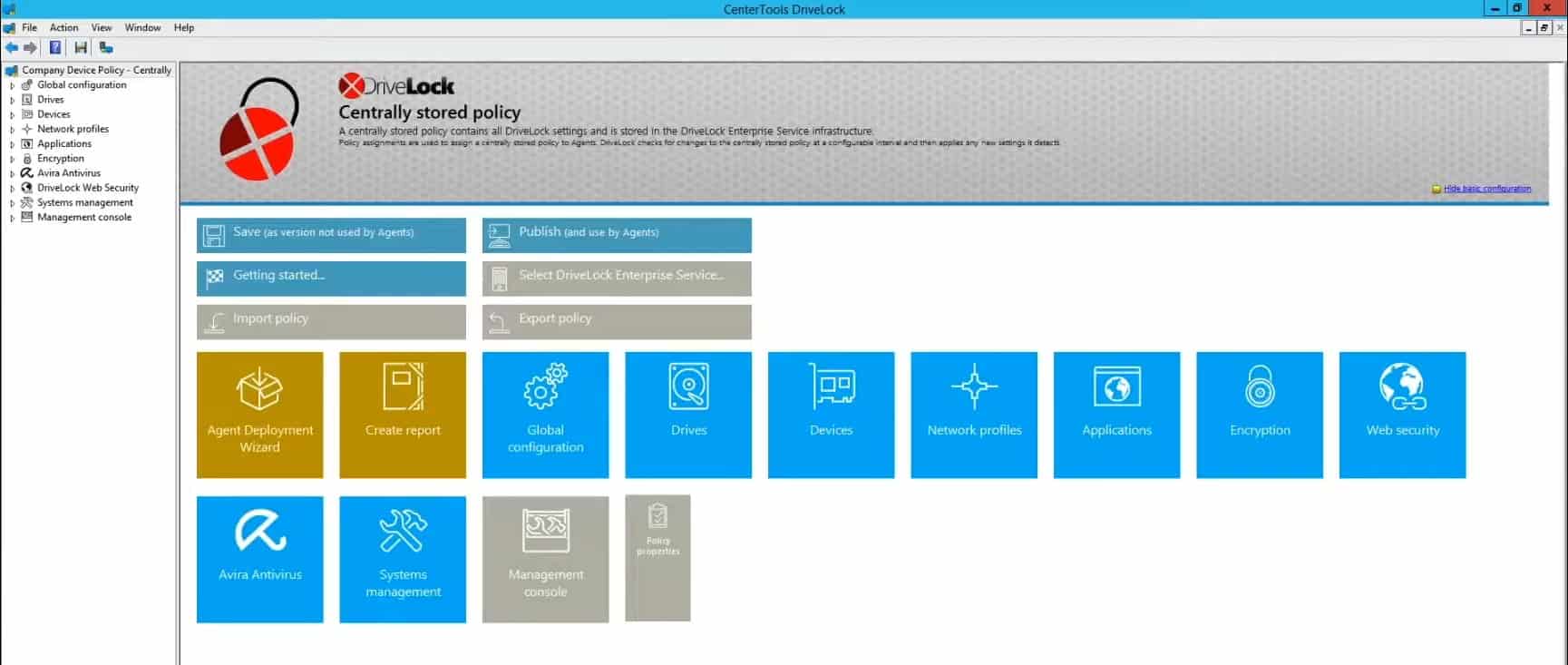
4. DriveLock
DriveLock provides cloud-based endpoint security that follows the Zero Trust model to secure endpoints and different data on the network. In addition, the platform offers numerous other features as separate services such as device encryption, app control, and vulnerability management.
DriveLock uses a minimalistic management console to help highlight critical information and key metrics to administrators on the front end. In addition, it leverages color well to help gather information about your environment and is fully customizable through a widget-based system.
The platform offers complete device control, including USB lockdown features to secure multiple types of environments. A part that made DriveLock stand out is its ability to train employees to handle data safely. This feature can identify when inappropriate access is attempted and rectify it through a short instructional lesson. This not only helps train staff to be more security conscious but also provides admins with a record of who attempted to access which files and how many times they tried.
Outside of USB lockdown options, DriveLock also supports controls for both internal devices and BYOD environments, allows users to create flexible policies without eliminating their current device policy. In addition, other forms of media removal such as CDs or DVD burners are also suppressed, a feature some other tools may lack.
You can test out DriveLock utterly free through a 30-day trial.
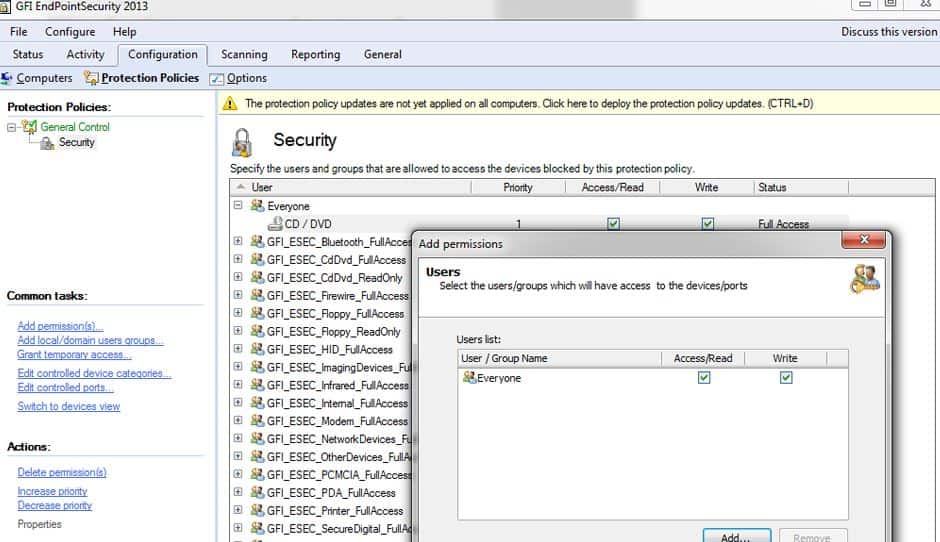
5. GFI Endpoint Security
GFI Endpoint Security provides device control and prevents data leakage through a series of features and policy controls across endpoints. The product starts through an awareness model, where it scans the networks and identifies vulnerable information in a breach. For example, files containing medical information, SSNs, etc. It then generates risk areas that help sysadmin determine where they need to create more stringent security controls to protect that data.
Agents can automatically be deployed when a new endpoint joins the network or domain, allowing users to keep a continuous inventory of their managed devices. Agents install quickly and automatically enforce the policies you set to lock down USB ports or restrict device access.
The platform offers centralized monitoring through a simple dashboard. The interface is pretty outdated compared to competing products but gets the job done in the end. GFI Endpoint Security provides detailed reporting and statistics about critical events and other activities useful for both casual documentation and compliance reporting.
GFI Endpoint Security is a part of the GFI Unlimited Suite which starts at $39.90 per unit for 10 to 49 endpoint agents.
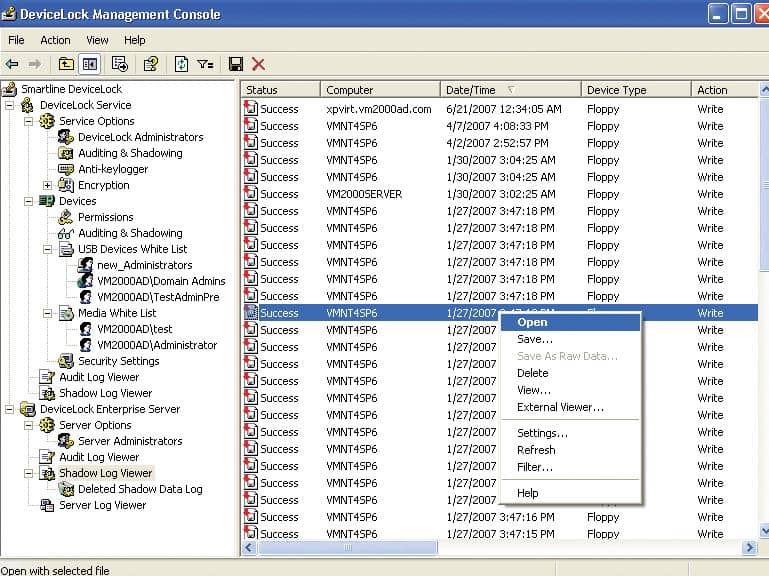
6. DeviceLock
DeviceLock DLP by Acronis offers data loss prevention, device control, and endpoint management. In addition, the platform minimizes insider threats by blocking unauthorized access to sensitive data automatically and logging any attempts to discover or access data out of scope for that user.
As a DLP solution, users have extended visibility into user behavior, devices, and the overall environment. This allows both administrators and the platform to identify patterns and trends that help reduce false positives and provide a more accurate device control solution.
DeviceLock works through a simple agent deployable and offers Active Directory integration and other centralized management console templates to set policies from. One hidden benefit to the platform’s increased visibility is having performance data collected for you. Performance reports allow you to see how well users are following data protection policies and viewing which features of the tool you use, helping you control your costs by eliminating features you don’t need.
DeviceLock offers several modular add-ons attractive to smaller budget-conscious organizations looking only to take advantage of a few features rather than pay for an enterprise solution. In addition to USB lockdown, DeviceLock also monitors and controls clipboards, identity image data, and extract text data from images to protect against data theft.
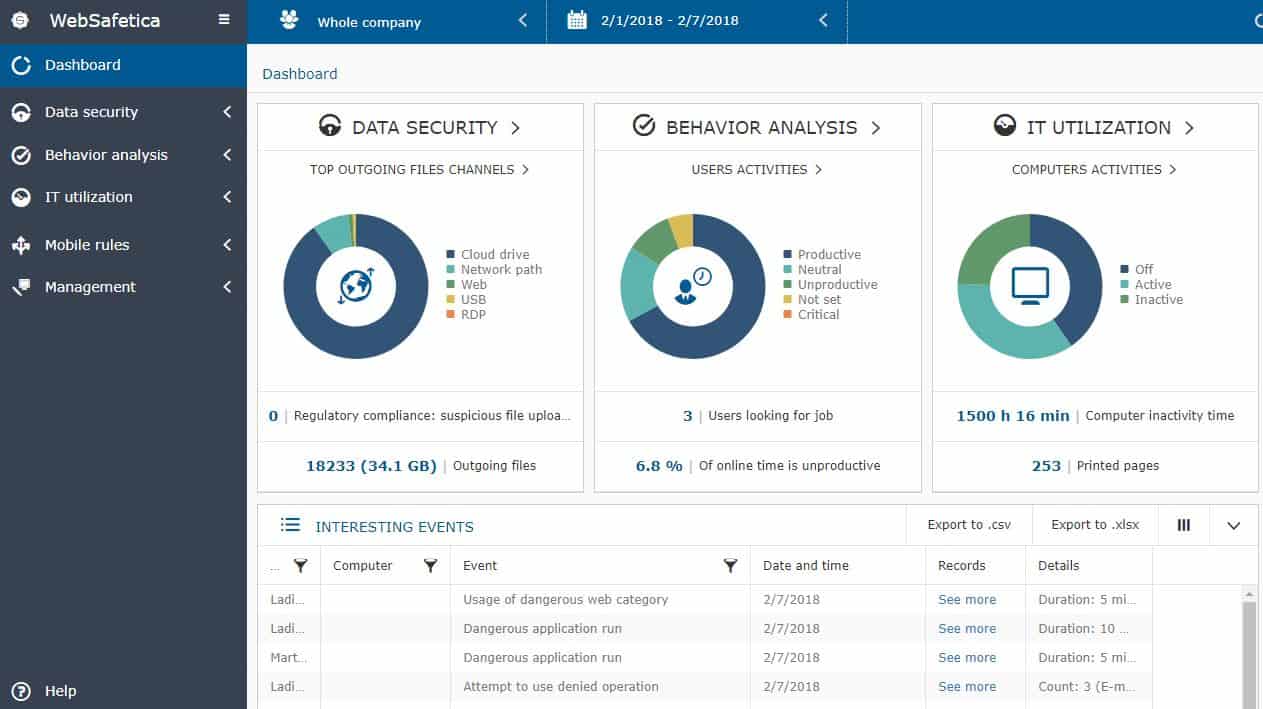
7. Safetica
Safetica focuses on protecting data by implementing DLP, insider threat detection, and regulatory controls for sysadmins. This combination helps keep businesses complaint while protecting them from accidental data loss through deletion and malicious insider data theft.
Administrators can create flows that not only restrict or lockdown USB ports but define how files can move. These rules provide granular control over how data moves, ensuring it can always go where it needs to, without being leaked elsewhere.
To detect insider threats, holistic behavioral analysis is used to automatically identity malicious behavior based on the baseline of everyday end-user actions. This, when paired with a Zero Trust policy, can see the emerging movement of a rogue employee and automatically restrict their access until a manual review has been completed.
The DLP section prevents data loss through a combination of incremental backups and customizable device control. First, onboarding starts by running an audit for sensitive data, where the system will attempt to highlight sensitive information. Second, users will set their policies based on these zones. Lastly, users create their automated reports and set up real-time alerts for any security threats that may emerge.
Safetica does not have a free trial, but you can test their platform through a free demo.
L’article 7 Best USB Lockdown Software Tools for 2022 est apparu en premier sur Comparitech.

0 Commentaires