XDR stands for Extended Detection and Response. It is an advanced version of endpoint detection and response (EDR) that pulls in other security tools and coordinates everything from the cloud.
While system coordination occurs on the cloud, detection and remediation actions need to be implemented by on-site modules. The extent to which research gets refined before it is sent to the cloud depends on the design decisions made by each vendor of XDR systems.
The interplay between detection speed and processing efficiency influences how much of an XDR is based onsite and how much is centralized in the cloud. Competing businesses need to offer attractive prices and centralized SaaS-based components bring costs down. However, a remote system that can be cut off from networks under attack is no use to anyone, no matter how cheap it is. So, XDRs are never entirely cloud-based.
Here is our list of the eight best XDR tools:
- Palo Alto Cortex XDR EDITOR’S CHOICE The definitive XDR system from the company that coined the phrase.
- CrowdStrike Falcon Combines onsite modules and SaaS systems in a unified security platform.
- LogRhythm XDR Stack A NextGen SIEM combined with UEBA and SOAR is a largely cloud-based system.
- Rapid7 Insight Platform A combination of on-site and cloud-based tools that compose an XDR.
- TrendMicro XDR A cloud-based SIEM that coordinates with on-site security services from that same vendor, including email security.
- Exabeam A SaaS SIEM system that interfaces to on-site agents.
- ImmuniWeb A cloud-based vulnerability management suite that blends together to form an XDR.
- Cynet 360 This platform uses AI routines and provides a high degree of threat resolution automation in its cloud-based services.
Elements of an XDR
An XDR is a platform – it is composed of a range of modules that work together. These are:
- Data collection which could be adapted from an EDR.
- Threat hunting which could be a SIEM, a vulnerability manager, or both.
- User and Entity Behavior Analytics (UEBA) to rule out false-positive reporting.
- Security Orchestration, Automation, and Response (SOAR) for threat mitigation.
Some providers offer these modules as individual products as well as bundled services
The best XDR platforms
The field of XDR is relatively new – the term was only coined in 2018. However, there are already some excellent XDR services available from leading security software providers.
All of these products are SaaS-based, which is one of the defining characteristics of an XDR system. You can read more about these tools in the following sections.
1. Palo Alto Cortex XDR
The term “XDR” was defined by Palo Alto Networks in 2018. As the inventor of the industry, Palo Alto can certainly be assumed to have got the right combination of tools to compose the definitive XDR service.
Each security software provider arrived at the XDR target from a different starting point. The Palo Alto journey to XDR started with evolved onsite security products, such as an EDR to replace endpoint antivirus and a Next-Generation Firewall to protect the network. Palo Alto also offers a virtual firewall – which is a SaaS service, based in the cloud, effectively creating a virtual network. This can protect your own cloud-based services, such as virtual servers provided by the likes of AWS or Azure.
Palo Alto Networks created its Cortex XDR to tie each of these services together into a coordinated cybersecurity service. This is the essence of XDR, a SaaS console that presents an overview of security elements and, behind the scenes, unites the information feed from each to provide a consolidated data lake for threat hunting.
The threat detection system that is the core service provided by Cortex uses UEBA and triage to cut through to pertinent data. As it operates on the servers, of the Palo Alto Networks servers, this system gets instant threat intelligence feeds and also benefits from the zero-day experiences of security processes operating for other Cortex customers.
Cortex speeds up threat mitigation through SOAR, lightening the code base on-site by interfacing to services that are already present on-site, such as Active Directory (AD) and the firewall.
The elements of the XDR platform, such as the next-generation firewall, can all be deployed independently, so getting the XDR plan is a matter of buying a service bundle.
EDITOR’S CHOICE
Palo Alto Cortex XDR is our top pick for an XDR solution because the XDR term was invented to describe it. This system has all of the indicators of a classic XDR. It is a SaaS coordinator of onsite protection measures and it uses already installed services to direct responses to attack. The cloud module pools attack experience from all customers and inject in threat intelligence developed at the same data center. UEBA and AI processes complete the combination of services that thread together into a coordinated defense platform.
2. CrowdStrike Falcon
CrowdStrike Falcon is a brand of cybersecurity tools. CrowdStrike has created a series of products within the Falcon product range that cover all aspects of system security. It markets these tools individually and in bundles.
The full complement of the Falcon range creates an XDR. CrowdStrike offers an EDR solution, which is installed on each endpoint, providing constant defense even when the device is offline. It provides a management console for its EDR system, which coordinates data collection and threat response. That central coordinator is cloud-based and that service, called Falcon Insight, is the core of a classic XDR.
The Falcon Insight system can be augmented by other modules to create a stronger XDR system. Those other services are Falcon X, which is a threat intelligence feed, Falcon Overwatch, which is a threat hunting service, and Falcon Discover, which is a vulnerability manager. Other add-ons are a firewall management system and USB device management.
CrowdStrike produces a next-generation antivirus system, called Falcon Prevent. This is installed on each endpoint. However, customers of Falcon Insight don’t need to buy this separately because it is bundled in with that coordinated service. In fact, Falcon Insight is really a coordinator that communicates with Falcon Prevent instances.
Features of the CrowdStrike Insight service include UEBA for detection triage and SOAR for threat response. It is included in the Falcon Enterprise, Falcon Premium, and Falcon Complete bundles. Falcon Complete is actually a custom-built package. CrowdStrike also offers a managed cybersecurity service.
CrowdStrike offers customers a 15-day free trial, although this actually gets you Falcon Prevent, not the fully-coordinated Falcon Insight service.
3. LogRhythm XDR Stack
LogRhythm evolved its XDR from a SaaS SIEM system. So, this combination of on-site and cloud-based modules is much more cloud-based than other XDR platforms. Almost all processing occurs on the LogRhythm servers. This is a very efficient solution. However, it does introduce a heavy dependency on a constantly active internet connection in order to maintain protection.
In the LogRhythm XDR Stack, on-site agents collect system log messages and upload them to the LogRhythm servers over a secure connection. This on-site function is performed by two elements, UserXDR, which is resident on each endpoint, and NetworkXDR, which gathers network statistics.
In the cloud, AnalytiX consolidates all incoming data and files them in a common format. DetectX is a threat detection system that constantly scans through incoming log messages looking for identifiers that indicate an intrusion. This is the core of the XDR stack, and it is the search engine of a SIEM.
While looking for suspicious behavior, DetectX employs machine-learning UEBA to work out a baseline of regular activity on the site. As it is based on the LogRhythm server, its detection algorithms get updated instantly whenever the LogRhythm analytical system detects a new attack vector in its work for other clients. So, the threat intelligence feed that should be expected in an XDR is sourced from shared experience.
The final element of the XDR Stack is RespondX. As its name suggests, this is the threat response service of LogRhythm. RespondX deploys SOAR to manipulate existing services on the client’s system in order to shut down threats.
LogRhythm offers three deployment options for its XDR Stack: IaaS (Infrastructure as a Service) on the cloud, on-premises software for Windows Server, or as a network appliance.
4. Rapid7 Insight Platform
Rapid7 has assembled an XDR platform called Insight. This is a collection of security products, mostly based in the cloud, that coordinate to provide a full XDR.
The main component of the Insight system is called InsightIDR. This is a SIEM system that performs most of its tasks on the cloud and offers a browser-based console to customers. This tool is not all cloud-based, however, because it includes onsite agents that gather data and upload them to the Rapid7 server over an encrypted connection. InsightIDR uses UEBA for activity baselining that reduces false-positive reporting.
The InsightIDR service implements threat detection by searching through unified log records for “chains of attack.” This is the threat intelligence base of the InsightIDR system, which is termed Attack Behavior Analytics (ABA). This service identifies the typical behavior of active hacker groups and can spot the opening attacks of each. This enables the system to jump ahead of the attackers and shut down the avenues that they typically use to get into a system and wreak havoc.
IDR stands for Incident Detection and Response. As that term explains, InsightIDR includes response mechanisms that are implemented through the onsite agent modules and also involve interfacing with other security products in a typical SOAR strategy. That SOAR system is called Insight Connect.
Other modules in the Insight Platform include InsightVM, which is a vulnerability manager that operates through both cloud and on-site components. Cloud services are protected by the DivvyCloud service. Rapid7 offers an Insight module specifically for DevOps environments concerned with Web applications. This is called Insight AppSec.
5. TrendMicro XDR
TrendMicro implements its XDR solution by coordinating its onsite security products through a cloud-based SIEM system. Those onsite tools include endpoint protection, network security, server protection, and email security products. There is also a cloud security system that can feed into the TrendMicro XDR service.
The various security products that are busy protecting specific aspects of IT infrastructure gather log messages and also generate their own monitoring notes. These get sent to the TrendMicro server for consolidations. That unified pool of live event records is then searched through by a threat detection module, which is essentially a SIEM system. Any worrying events generate system alerts and instructions to the relevant onsite module for deeper vigilance.
Confirmation of malicious activity triggers automated response actions that are performed directly by the onsite tools or relayed through them to system utilities. This is the classic SOAR strategy.
TrendMicro offers XDR in two formats. The first of these is called Vision One, which is a coordinating SaaS layer offered to customers of TrendMicro onsite security packages. The other option is called Managed XDR, which is a fully managed, outsourced SOC service.
6. Exabeam
Exabeam is a cloud-based SIEM that expands out into a security operations suite to form an XDR. The majority of the Exabeam system is based in the cloud with onsite elements deployed as relays. The device agents upload log messages and receive mitigation instructions.
Step one in this SaaS SIEM service is the creation of an Exabeam Data Lake. This is a consolidated poll of records that gets constantly added as new uploads arrive from device agents. These records are made available in the web-based console for viewing and sorting by the user but their main purpose is to provide a data mine for the threat detection service in the Exabeam XDR.
Exabeam Advanced Analytics operates as a UEBA service and establishes a pattern of normal behavior on a client-by-client basis. This reduces false-positive reporting and gives the threat hunter a baseline to compare activity records against.
Incident response can be varied according to the preferences of the user. The XDR platform includes the Exabeam Incident Responder. this is where the user decides on the level of threat mitigation automation. The response is dictated by “playbooks.” These are workflows that get triggered by a specific type of threat. That response could just be a notification – which is the default. Otherwise, the user can set up an automated response to shut down detected threats.
An optional extra for the Exabeam XDR system is an archiving to store log files. The Exabeam XDR SaaS is available on a free trial.
7. ImmuniWeb
ImmuniWeb offers penetration testing and a vulnerability scanner. These are offered as a platform that can be combined with a SIEM to create an XDR. The SIEM isn’t included, however, so you will need to source that elsewhere on advice from the ImmuniWeb team.
The difference between penetration testing and vulnerability scanning is that penetration testing is a manual process and vulnerability scanning is automated. So, the ImmuniWeb services that you would subscribe to for your self-assembled XDR would be its Discovery and Continuous systems.
ImmuniWeb Discovery is an external scan that searches through Dark Web sites for any indications that your site has been compromised. This could be because user account details are up for sale or hackers specifically mention your services or URLs when advertising attack tools.
ImmuniWeb regularly sweeps hacker sites for information on attack strategies and feeds that knowledge into its Continuous service. This is a vulnerability scanner that looks through a client’s system from an external viewpoint, testing its protection against any newly-discovered attack vector.
The ImmuniWeb service is entirely cloud-based and is offered in three editions: Corporate Pro, Corporate, and Express Pro. These are all subscription services with a monthly charge rate.
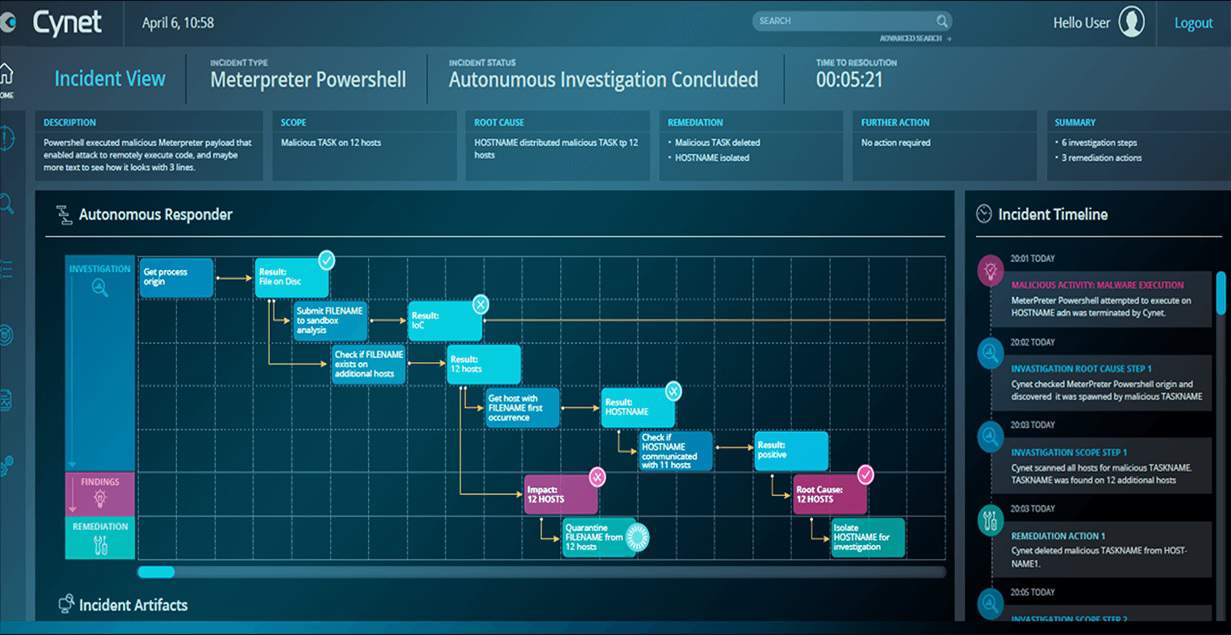
8. Cynet 360
Cynet calls its XDR system an Autonomous Breach Protection platform. It links together next-generation antivirus, EDR, UEBA, network traffic analysis, and deception intelligence in a classic on-site/cloud combination that typifies an XDR.
The data collection element in this SaaS service is called Sensor Fusion. These are log message collectors and network monitoring sensors that generate their own activity records. These are uploaded to the Cynet 360 service, which performs a SIEM search for threats.
The Deception module of Cynet 360 is very good – it is a unique service created by this business. The Deception strategy is to work as a honeypot. It creates fake, weakly-protected user accounts that attract hackers. It also diverts malicious activities with fake data files and deceptively easy-to-change (but fake) device settings.
Cynet 360 uses AI-based UEBA to zoom in on intruder activity and leave genuine users alone. The service includes an armory of scripts and strategies that automate threat response. This mitigation service also interfaces with other system services in a SOAR defense strategy. Cynet offers a 14-day free trial of its Cynet 360 XDR.
L’article 8 Best XDR Tools and Software est apparu en premier sur Comparitech.



0 Commentaires