The US National Institute of Standards and Technology (NIST) Cybersecurity Framework provides a policy framework of computer security guidance for how organizations can assess and improve their ability to prevent, detect, and respond to cyber-attacks. The framework provides a high-level categorization of cybersecurity outcomes and a methodology to evaluate and manage those outcomes
Overview of the Framework
The NIST Cybersecurity Framework (CSF) is a risk-based approach designed for businesses to assess and manage cybersecurity risk. Although the framework is published by the United States Department of Commerce agency, the common taxonomy of standards, guidelines, and practices that it provides is not country-specific; this explains why it is used by many governments, businesses, and organizations worldwide.
The Framework does not replace an organization’s risk management or cybersecurity program; rather, it complements the existing program and provides value by acting as a high-level security and risk management and assessment tool. Organizations can leverage the Framework to identify opportunities to strengthen and communicate their cybersecurity risk management while aligning with industry practices.
It is designed for businesses, government agencies, and not-for-profit organizations regardless of their focus or size. An organization typically starts by using the framework to develop a “Current Profile,” which describes its cybersecurity activities and its outcomes. It can then create a “Target Profile” or adopt a baseline profile tailored to its industry sector (e.g., energy or telecoms industry) or type of organization. It can then define steps to enable its transition from its current profile to its target profile.
The NIST CSF consists of three main components:
- The Framework Core This contains various activities, outcomes, and references about aspects and approaches to cybersecurity.
- The Framework Implementation Tiers These are used by an organization to clarify for itself and its partners how it views cybersecurity risk and the degree of sophistication of its management approach.
- The Framework Profile This is a list of outcomes that an organization has chosen from the categories and subcategories based on its needs and risk assessments.
The Framework Core
The Framework Core presents industry standards, guidelines, and practices that allow for communication of cybersecurity activities and desired outcomes across the organization from the executive level to the implementation/operations level.
The core materials are organized into five “Functions,” subdivided into “Categories” such as Asset Management, Identity Management and Access Control, and Detection Processes. For each category, the framework defines several “Subcategories” of cybersecurity outcomes and security controls such as External Information Systems are Catalogued, Data-at-rest is Protected, and Notifications from Detection Systems are Investigated. For each subcategory, the framework also provides “Informative Resources” referencing specific sections of various other information security standards (such as ISO 27001, COBIT, ANSI/ISA-62443, etc.) and practices that illustrate a method to achieve the outcomes associated with each Subcategory. The five functions of the Framework Core include: Identify, Protect, Detect, Respond, and Recover.
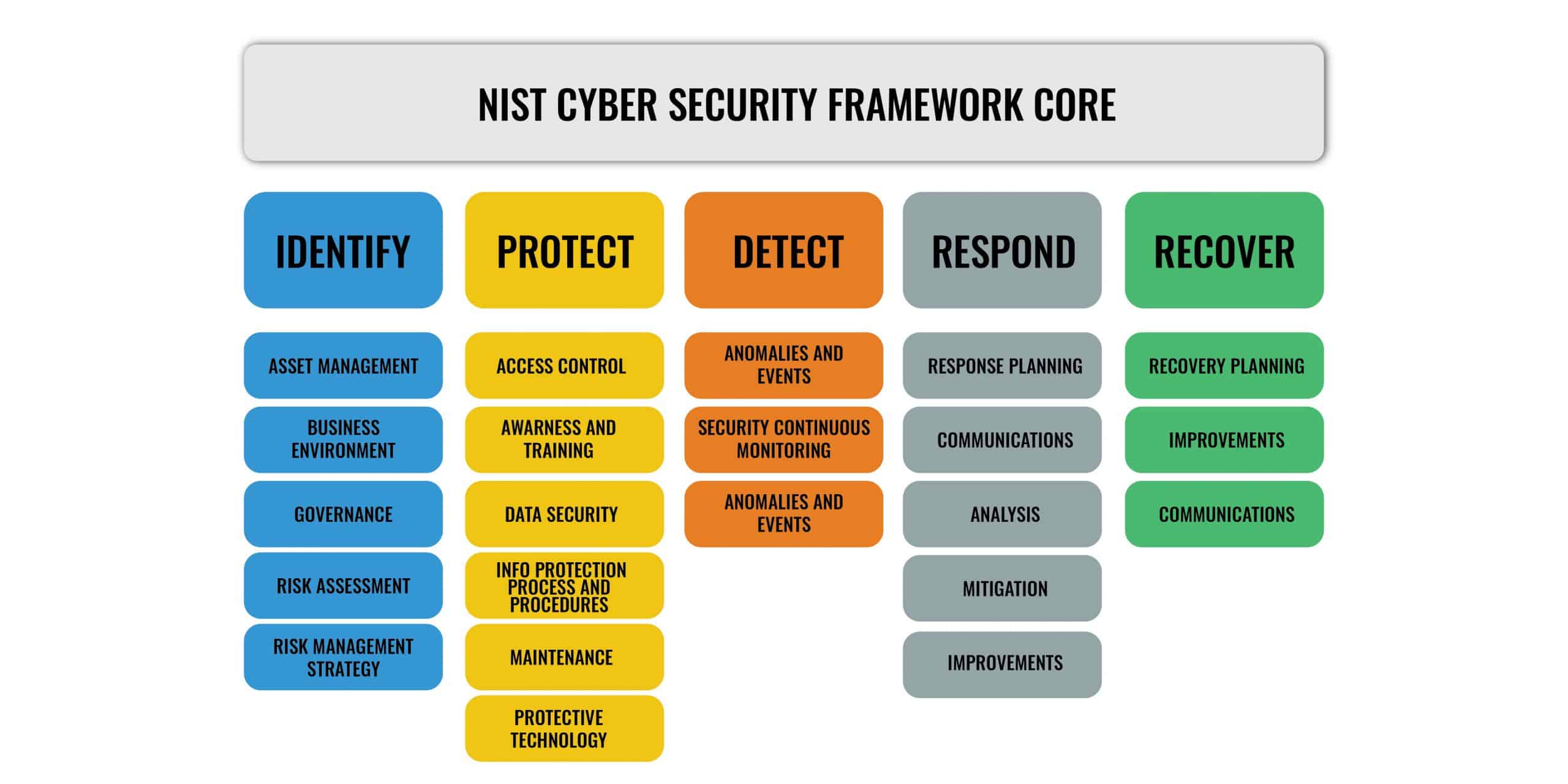
Identify: The activities in the Identify Function are fundamental to the effective use of the Framework.
For an organization to effectively focus and prioritize its efforts, consistent with its risk management strategy and business needs, a good understanding of the business context, the resources that support critical functions, and the related cybersecurity risks are essential.
The Identify Function helps to understand managing cybersecurity risk to systems, assets, data, capabilities, and people within the organization. Examples of outcome Categories within this Function include: Asset Management; Business Environment; Governance; Risk Assessment, and Risk Management Strategy. Key activities that take place in this group include:
- Identifying physical (personnel, facility, etc.) and digital assets (devices, systems, data, software, etc.) to establish the basis of an asset management program.
- Identifying the organization’s business environment, including its mission, objectives, stakeholders, activities, and role in the supply chain. This information is used to inform cybersecurity roles, responsibilities, and risk management decisions.
- Identifying established cybersecurity policies, procedures, and processes to monitor and manage the organization’s regulatory, legal, risk, environmental, and operational requirements. The understanding of those informs the management of cybersecurity risk.
- Identifying cyber risk and threats to organizational operations (including mission, functions, image, or reputation), asset vulnerabilities, threats to internal and external corporate resources, and response activities.
- Establishing a risk management strategy, including identifying constraints, risk tolerances, and assumptions. These are used to support operational risk decisions.
- Establishing supply chain risk management strategy, including the processes to identify, assess, and manage supply chain risks. These are used to support risk decisions associated with managing supply chain risk.
Protect: The activities in the Protect Function are fundamental to the development and implementation of appropriate safeguards to ensure the delivery of critical services.
It supports the ability to limit or contain the impact of a potential cybersecurity incident. Examples of outcome Categories within this Function include Identity Management and Access Control; Awareness and Training; Data Security; Information Protection Processes and Procedures; Maintenance, and Protective Technology. Key activities that take place in this group include:
- Implementing protections for identity management and access control within the organization to ensure that access to physical and digital assets is limited to authorized users, processes, or devices,
- Empowering staff through security awareness training to safely perform their duties and responsibilities, consistent with related cybersecurity policies and procedures.
- Establishing data security protection consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information
- Implementing security policies, processes, and procedures to maintain and manage the protection of information systems and assets
- Managing technology to ensure the security and resilience of systems, consistent with organizational policies, procedures, and agreements
Detect: The Detect Function defines, develops, and implements the appropriate activities to identify cybersecurity incidents promptly.
Examples of outcome Categories within this Function include Anomalies and Events; Security Continuous Monitoring, and Detection Processes. Key actions that take place in this group include:
- Monitoring your network for unauthorized users or connections and implementing detection mechanisms to ensure timely awareness of malicious activities.
- Investigating any unusual activities on your network and ensuring abnormal activity is detected promptly and the potential impact of events is understood.
- Implement continuous monitoring capabilities to monitor IT assets, identify cybersecurity events, and verify the effectiveness of protective measures.
Respond: The Respond Function supports the ability to contain the impact of a potential cybersecurity incident by enabling the development and implementation of appropriate activities to take action regarding a detected security incident.
Examples of outcome Categories within this Function include Response Planning; Communications; Analysis; Mitigation, and Improvements. Key activities that take place in this group include:
- Ensuring response processes and procedures are maintained and executed to ensure timely response to detected cybersecurity events.
- Notifying customers, employees, and other key stakeholders whose data may be at risk during and after a cybersecurity incident
- Carrying out mitigation activities to prevent the expansion of an event and its effect and resolve the incident.
- Updating your cybersecurity policy and plan with lessons learned from current and previous detection/response activities and implementing those improvements
Recover: The Recover Function supports timely recovery to normal operations that were affected due to a cybersecurity incident. It also supports the development and implementation of appropriate activities to maintain plans for resilience.
Examples of outcome Categories within this Function include Recovery Planning; Improvements, and Communications. Key actions that take place in this group include:
- Ensure that recovery processes and procedures are maintained and executed and ensure timely restoration of systems or assets affected by cybersecurity incidents.
- Implementing improvements by incorporating lessons learned into future activities and reviews of existing strategies.
- Coordinating internal and external communications to keep employees, customers, and other stakeholders informed of your response and recovery activities.
Framework Implementation Tiers
The Framework Tiers are a scaled ranking system (tier 1-4) that describes an increasing degree of rigor and sophistication in cybersecurity risk management practices. Higher tiers represent a higher degree of complexity and maturity in the management of cybersecurity risks and responses. This helps determine the extent to which cybersecurity risk management is informed by business needs and is integrated into an organization’s overall risk management practices. It provides context for stakeholders around the degree to which an organization’s cybersecurity program exhibits the characteristics of the NIST CSF.
NIST makes it clear that the Implementation Tiers are not designed to be a maturity model. Instead, they are intended to act as a benchmark to take stock of current cybersecurity risk management practices and help organizations develop plans to improve their cybersecurity posture. There are four Implementation Tiers altogether. Each of the tiers is broken down into three main components: Risk Management Processes, Risk Management Program, and External Participation. NIST outlines the Tiers as shown in the table below:
| Tier | Name | Description |
|---|---|---|
| 1 | Partial | No cybersecurity coordination. Cybersecurity practices are adequate for the risks experienced. |
| 2 | Risk-Informed | Informal sharing and coordination. The organization is aware of some risks and is planning how to respond to them. |
| 3 | Repeatable | Regular formalized coordination. The organization has clearly defined and regularly repeatable cybersecurity processes. |
| 4 | Adaptive | Active risk management and information sharing. The organization is proactively instigating cybersecurity measures. |
Table 1.0 NIST CSF Implementation Tiers
| Tier Name | Risk Management Process | Integrated Risk Management Program | External Participation |
|---|---|---|---|
| Partial | Risk management practices not formalized. Reactive.approach | Limited cyber risk awareness and irregular risk management | No external collaboration |
| Risk-Informed | Approved practices, but not widely used as policy | More risk awareness and internal sharing, but no established organization-wide approach to managing risk | Collaborates, but no formalized information sharing |
| Repeatable | Approved as policy and updated regularly | Risk-informed policies, processes, and procedures are defined, implemented as intended, and reviewed | Collaborate, and receive information regularly |
| Adaptive | Continuous improvement | Organization-wide approach to managing cybersecurity risk | Actively shares information internally and externally |
Table 2.0 The NIST CSF Implementation Tiers and its Components
The Framework Profile
According to NIST, “a Framework Profile enables organizations to establish a roadmap for reducing cybersecurity risk that is well-aligned with organizational and sector goals, considers legal/regulatory requirements and industry best practices, and reflects risk management priorities.” Framework Profiles can be used to describe your organization’s “As-Is State” (current profile) or your desired “To-be State” (target profile) of a specific cybersecurity level. The As-Is State or Current Profile indicates the cybersecurity outcomes currently being achieved. In contrast, the To-be state or Target Profile shows the results needed to achieve the desired cybersecurity risk management goals.
An organization can use profiles to compare its Current Profile against a Target Profile. According to NIST, profiles support an organization’s business requirements and help communicate risk in the organization both internally and externally. In so doing, the organization can see gaps in its cybersecurity posture and identify opportunities for improvement. How quickly an organization responds to the mitigation of those gaps depends on its business needs and risk management processes.

How to Use the NIST Cybersecurity Framework
The NIST CSF is not designed to replace your existing processes but to complement them. An organization can use the Framework as a crucial part of its “systematic process for identifying, assessing, and managing cybersecurity risk.” Using the Framework as a cybersecurity risk management tool, an organization can determine critical service delivery activities and prioritize expenses to maximize the impact of the investment. The following sections present different ways organizations can use the Framework as stated in the Framework document.
- Basic Review of Cybersecurity Practices: The Framework can be used to compare an organization’s current cybersecurity activities with those outlined in the Framework Core. The Framework can also help an organization answer key questions such as where they are and where they are going. Then they can move in a more informed way to strengthen their cybersecurity practices where and when deemed necessary.
- Establishing or Improving a Cybersecurity Program: Although the Framework is not intended to be used as a standalone framework for developing an information security program, it can serve as a foundation for developing a company-wide cybersecurity program. Good security programs are usually built from multiple sources or viewpoints, and the NIST Framework provides many excellent tools to do just that. The Framework can also be customized or paired with other frameworks or standards such as ISO/IEC 27000, COBIT 5, ANSI/ISA 62443, and NIST SP 800-53 to boost your cybersecurity program.
- Communicating Cybersecurity Requirements with Stakeholders: The Framework provides a common language to communicate requirements among interdependent stakeholders responsible for delivering essential critical infrastructure products and services. An organization can use the Framework to communicate its cybersecurity current and desired state through a Current Profile and Target Profile to essential stakeholders.
- Buying Decisions: A Framework can be used to inform decisions about buying products and services. Once a product or service is purchased, the Profile also can be used to track and address residual cybersecurity risk.
- Identifying Opportunities for New or Revised Informative References: The Framework can be used to identify opportunities for new or revised standards, guidelines, or practices where additional Informative References would help organizations address emerging needs.
Conclusion
The NIST CSF is a powerful tool to organize and improve your cybersecurity posture. It is based on well-known standards and practices and represents the best current practice in cybersecurity. Implementation of the framework is voluntary—which means that there is no right or wrong way to do it. If you’re interested in improving how your organization identifies, detects, responds to, and recovers from cyber risk, the NIST CSF is a great tool to integrate into your cybersecurity program. To maximize its benefits, you’ll need to customize and adapt it to meet your organization’s specific business processes and priorities. If you are not sure where to begin, NIST provides many materials you can use to start using the framework.
L’article NIST Cybersecurity Framework Guide est apparu en premier sur Comparitech.
0 Commentaires