
Personally Identifiable Information (PII) doesn’t have a universal definition, but we can define it in general terms. PII is information that is tied to an individual, for example, name, address, phone number, email address, Social Security Number (SSN), passport number, bank account number, driver’s license number, and health identifiers. Under some definitions, it can include purely digital identifiers such as IP addresses, usernames, and advertising IDs.
When PII falls into the wrong hands, it becomes a privacy concern and possibly a security risk. PII can be used by companies and governments to track the activity of individuals both online and offline. PII can also be very valuable to criminals as it can assist in carrying out attacks both in the physical world and online.
In this post, we reveal more about what constitutes PII, why you should be concerned, and how to protect your information.
What is PII?
As mentioned, the definition of PII is different depending on which resource you consult. Below we look at how some data privacy regulations define PII.
General Data Protection Regulation (GDPR)
Under the GDPR Article 4, examples of PII include identifiers such as:
- Name
- Identification number
- Location data
- Online identifier
It also talks about factors specific to a person’s identity with respect to the following:
- Physical
- Physiological
- Genetic
- Mental
- Economic
- Cultural
- Social
In Recital 30, the GDPR outlines the following as identifiers:
- IP addresses
- Cookie identifiers
- Other identifiers such as radio frequency identification (RFID) tags
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA doesn’t define PII, but instead defines the similar term Personal Health Information (PHI). According to HIPAA Journal:
PHI is information related to the health status of an individual in relation to:
- the provision of healthcare
- payment for healthcare services
- use in healthcare operations (PHI healthcare business uses)
Examples of PHI include:
- Diagnoses
- Treatment information
- Medical test results
- Prescription information
- National identification numbers
- Demographic information such as birth dates, gender, ethnicity, and contact and emergency contact information
Children’s Online Privacy Protection Act (COPPA)
COPPA outlines rules regarding the collection of data from children. According to the FTC, under COPPA:
“The Rule defines personal information to include:
- First and last name;
- A home or other physical address including street name and name of a city or town;
- Online contact information;
- A screen or user name that functions as online contact information;
- A telephone number;
- A Social Security number;
- A persistent identifier that can be used to recognize a user over time and across different websites or online services;
- A photograph, video, or audio file, where such file contains a child’s image or voice;
- Geolocation information sufficient to identify street name and name of a city or town; or
- Information concerning the child or the parents of that child that the operator collects online from the child and combines with an identifier described above.”
While these definitions vary, the key to PII is that it can be used singularly or collectively to identify a single person. When you consider all of our interactions both online and offline, there is really a huge amount of data out there that could be considered PII. For example, every time you visit a website, cookies (a type of identifier) are placed in your browser. Every time you fill out an online form or post something personal in a public forum, you are sharing PII.
How may PII be exposed?
With all this information floating around, it’s no surprise that it’s easy for some of it to be exposed. When we talk about exposure, the definition depends somewhat on what you’re comfortable with. For example, if you’re okay with companies sharing your information with third parties such as advertisers, then you wouldn’t consider that exposure. On the other hand, others might object to this and prefer that their information is kept within the confines of the company they directly shared PII with.
In general, when we talk about exposure, it can be defined very loosely as the information becoming either publicly-accessible or accessible to someone whom you would not want to view it. With that in mind, here are some of the possible means by which PII may be exposed.
Social media and other public accounts
A lot of personal information is actually leaked by the subject themselves. This is especially true in the age of social media and online forums. Platforms will often ask for a ton of information when you sign up, and if you’re not diligent about adjusting your privacy settings, some of this information can be viewed by everyone in your contacts list or by the entire online world.
That’s not to mention information that you may provide in passing. For example, getting a driver’s license is a super exciting time for a new driver, but giving in to the temptation of posting a photo of your new license online will mean you’re putting a bunch of PII out there.
One problem with social media is you’re not always in control of how much of your information is posted online. Friends or relatives may inadvertently publish some of your personal information such as your birth date or address.
In other cases, the posting of private information can be malicious. For example, in cases of revenge and other cyberbullying attacks, a bully may post their victim’s home address and phone number, often alongside a message inviting harassment. There’s actually a name for this public sharing of someone else’s information—doxxing—and it’s considered a punishable crime in many jurisdictions.
ISP and government monitoring
Do you know how much of your online activity is being tracked by your Internet Service Provider (ISP)? And do you know if the collected data is being shared with anyone? Most ISPs collect information about the browsing activity of customers, including sites visited, search history, and information about downloads. They can sell this to third parties (mainly advertisers) and can hand it over to law enforcement or other government agencies upon request.
Indeed, ISP monitoring is one way in which governments surveil citizens. In most countries, there are other methods at play too, including the use of biometrics and CCTV. The amount of information that is collected and how it is gathered and handled will depend on local laws. Some governments bypass their own laws by entering into information-sharing agreements with other countries that allow governments to spy on each other’s citizens.
ISPs often enable you to opt out of some data collection. For example, US providers Verizon and AT&T explain how to do this.
Companies collecting and sharing PII
Most websites store information every time you visit, including your IP address and the date, time, and duration of the visit, as well as information about your device and operating system. Many also insert identifiers (known as cookies) into your browser, which can help them track which websites you visit next.
Since the GDPR was introduced, websites serving EU residents are required to notify site visitors of the information they collect. Visitors usually have the option to view (and sometimes adjust settings for) this information or simply accept all cookies. It’s not just EU-based companies that need to do this. Any sites that have visitors from EU countries are included too. That’s why you’ll find most websites you visit, including North American ones, will have cookie policy popups.
Note there is debate about whether an IP address constitutes PII, and really it depends on what principles you’re following. But no matter what the official decision is, the fact remains that an IP address can and has been used to identify individuals.
Data breaches
Unfortunately, even if you’re happy to trust a company with your data, it doesn’t mean they can always keep it private. Even organizations with the tightest security measures come under attack from cybercriminals and are vulnerable to human error. Resulting data leaks and breaches can expose your personal information to criminals or the public.
Depending on the organization, a data breach can result in the leak of a plethora of information, including name, email, phone, home and mail addresses, social insurance number, financial information, medical data, criminal records, account login data, and much more. PII exposed in data breaches often ends up on the dark web for sale to the highest bidder.
Phishing
Another way cybercriminals can access data is through phishing attacks. These can occur against individuals and businesses and involve social engineering to persuade the victim to hand over information.
For example, you may receive an email purporting to be from your financial institution asking you to respond with personal details and financial information. Or the email might ask you to click a link to log into your account. In fact, the link leads you to a phishing site, a fake website designed to steal your information.

Malware
Malware that finds its way onto your device can also threaten to expose PII. Malware can enter your computer or mobile device via a number of means including through a malicious email link or attachment, a malicious link on a website, a popup ad (malvertisement), or someone physically installing it on your device.
Many types of malware are harmless from a data exposure aspect, for example, even most ransomware won’t actually expose the content of your files. But some types of malware, particularly certain forms of spyware, are designed to steal information. Keyloggers, for example, can be used to steal login details, personal information, financial data, and more.
Other cyberattacks
We’ve covered some of the main types of cyberattacks above, but there are others that pose a risk to PII. For example, a man-in-the-middle attack can intercept network traffic and steal or alter data.
Another example is account takeover fraud. Cybercriminals could obtain login credentials from a data breach or guess them in a brute force or credential stuffing attack. Once in an account, a hacker could obtain any information that is held in the account. For example, many ecommerce sites store your credit card information as well as personal data such as your home address.
What are the concerns surrounding PII?
So why should you care if your personal information is exposed? Here are some of the main reasons, some obvious, and others a little less so.
- Government tracking: With the various types of surveillance being conducted, your government (and perhaps those of other countries) could feasibly know your every move.
- Big data uses: Personal data is often collated into giant datasets that are analyzed to reveal things like trends and patterns in human interactions and behavior. Many people simply don’t want their information to be a part of this.
- Advertiser targeting: Some users don’t mind seeing targeted ads on every site they visit. For others, it makes them feel that their privacy has been violated.
- Privacy of children: Even if you’re not too concerned about your own data, chances are you’d rather not have governments and other organizations tracking your children online.
- Safety concerns: Many people could be put at risk by having their personal information exposed. For example, activists, journalists, victims of crime, or people in witness protection need to be very careful with certain data.
- Employment: Even though laws are in place to prevent employers from discriminating on the basis of certain factors, it probably still happens.
- Fraud: Leaked personal information can be used by cybercriminals in various types of fraud including identity theft and credit card fraud.
- Stalking and bullying: Stalking, bullying, and other forms of harassment can be perpetuated if the perpetrators have access to personal information about their victims.
In general, the more of your PII that’s circulating, the greater the risk of it falling into the wrong hands or being misused.
How can you protect PII?
As you can see, there are a ton ways your data can be exposed and there are also many scary prospects for its use. Thankfully, there are lots of simple steps you can take to protect your PII.
Here’s how to protect your PII:
- Use common sense
- Tighten privacy settings
- Review privacy policies carefully
- Learn to spot malicious emails and messages
- Use strong passwords and 2FA
- Close old accounts
- Use a VPN
- Only visit HTTPS sites
- Utilize privacy tools
- Protect your wifi router
- Use an antivirus
- Keep software up to date
- Protect sensitive documents
- Request information from companies
- Remove yourself from people searches
Let’s look at each of these in more detail:
1. Use common sense
One of the easiest ways to avoid disclosing your PII is to think carefully before sharing it. First and foremost, don’t go publishing your information publicly online such as in social media posts or chat forums. Also consider if you really need to fill out that online form or survey.
If you’re a parent, it’s important to have conversations with your children about what information they share on social media or on message boards and chat groups.
2. Tighten privacy settings
As well as avoiding publicly posting PII on social media, you should make sure to regularly review your privacy settings. Be sure to disable any settings that result in details like your date of birth, email, or phone number being made public. Yes, it’s nice to get all those birthday wishes from acquaintances you forgot existed, but is it really worth having this information floating around on the web?
Along the same lines, be wary of people you don’t know on social media who try to connect with you. If you accept their request, they’ll be able to see all the information your real friends can. If you have any suspicions about another user, you can simply block them.
3. Review privacy policies carefully
Yes, it can be a pain to review the privacy policy of every site you visit or organization you create an account with. But if you want to make sure your information is safe, then it’s a necessary evil. Some sites make it easier than others to opt out of data collection, but do so wherever possible.
Making a point of only choosing reputable companies is a good start, but we have seen many cases of even seemingly trustworthy companies doing shady things with their users’ data. Plus, no matter how reputable they are, there is still a chance they could be breached.
4. Learn to spot malicious emails and messages
Avoid sending phishers sensitive information by learning how to spot phishing emails. Most reputable companies (especially financial institutions) will never ask you to send personal information in an email.
Also learn to look for emails with malicious links or attachments. Attachments or links can contain malware and some links can lead you to phishing sites.
Note that attackers don’t only use email. Many will send similar messages via text or through messaging apps.
5. Use strong passwords and 2FA
You probably hear this advice over and over again, but it really is crucial to use strong passwords. It’s crazy that many people still use things like “123456” and “qwerty” as their password for important accounts. Weak passwords are easy to guess using brute force attacks. Strong passwords are at least eight characters in length and should contain a mixture of numbers, symbols, and upper and lower case letters.
It’s also important to use a different password for every account. If someone finds your password to one account, perhaps using a brute force attack or through a data breach, they could use credential stuffing to hack into other accounts. This technique involves using a known set of credentials for one account to try to log into other popular platforms.
Worried about remembering all these strong passwords? A password manager really is a must-have tool these days. It will securely store all your passwords and autofill them when you need them.
To back up your account security, many platforms offer Two-Factor Authentication (2FA) or Two-Step Verification (2SV), both of which incorporate an additional step into the account login process. For example, you might be required to enter a verification code sent to your phone or email, use a fingerprint, or even enter a special USB key. We recommend using these options wherever possible. The extra step can seem like a pain, but it can save you a lot more hassle in the long run.
6. Delete old accounts
Let’s face it, most of us have at least a few and possibly dozens of accounts we set up and forgot about. Ideally, if you’re not using an account anymore, you should try to delete it. These accounts could be holding information that’s valuable to criminals, for example, a username and password combo you use on another account, or personal or financial information.
Many platforms make it difficult to delete or even deactivate old accounts, so you may have to contact the company directly. Again, this can be tedious, but it’s worth it to avoid having your data out there.
7. Use a VPN
A Virtual Private Network (VPN) is a handy tool that will prevent snoopers from viewing your internet traffic. This is great for everyday use as it stops your ISP from building a profile around your browsing activity for sale to third parties.
VPNs route your traffic through a secondary server in a location of your choice, replacing your IP address with one from the VPN server. This means that your browsing activity logged by your ISP is tied to the VPN IP address, not your real one. Plus websites you visit can’t see your real IP address.
A VPN encrypts all traffic flowing to and from the device it’s installed on. This is especially important when connected to public wifi. These networks are notoriously unsecure and prime spots for hackers to steal information, such as personal details or banking data. When your traffic is encrypted, even if it’s intercepted, it will be unreadable. We recommend NordVPN as a great all-rounder.
Note that some VPNs actually collect data on users. This might include their real IP address, the IP address of the VPN server they connect to, and even which websites they visit. This can be shared with third parties such as advertising agencies or governments. If you don’t want to be tracked, be sure to look out for a VPN with a strict no-logs policy.
8. Only visit HTTPS sites
Another tip, especially if you’re not using a VPN, is to only visit HTTPS sites. This is particularly important to look out for if you’re entering any personal or financial information into a site. A site marked HTTPS has an SSL certificate so you can be fairly sure it’s reputable and that communications between your browser and the site are secure.
To make things easier, you can use the extension HTTPS Everywhere. If HTTPS is available for a given site, this extension will ensure that’s the version you visit.
9. Utilize privacy tools
There are lots of great privacy tools available designed to help keep your PII private. Some top tools to consider are ad-blockers and anti-tracking extensions.
Ad-blockers prevent pesky ads that can invade privacy and pose a security threat in terms of malware. Anti-tracking extensions block third-party trackers to help you browse more privately. Some tools such as Adblock Plus combine both ad-blocking and anti-tracking functionality.
You can also use a private search engine if you’d rather not have your search history tied to your IP address.
10. Protect your wifi router
Anyone who has access to your home wifi network could feasibly snoop on your internet traffic. Bear in mind anyone who has used the wifi in your home in the past will have your password, including friends, family, roommates, ex-partners, and possibly cleaners, technicians, contractors, and other workers. Plus, if you haven’t changed your default password, strangers may even be able to access your network.
Change your default password and be cautious about who you share it with. You can also use a VPN on your home network as an added layer of protection. You can even use a VPN router to encrypt traffic to and from all internet-connected devices in your home.
11. Use a firewall and antivirus
Firewalls and antivirus software can help protect your device against spyware and other types of malware. A firewall provides a first layer of defense by monitoring traffic leaving and entering ports on your device. It rejects certain traffic based on set security parameters. Most operating systems have a software firewall and some home routers have a built-in hardware firewall. Just make sure yours are enabled. You may want to consider a third-party firewall for extra protection.
An antivirus is another great tool for preventing malware. It looks out for known threats and blocks them from executing on your system. Depending on the antivirus tool you use, it might automatically remove malware too. That said, antivirus programs aren’t guaranteed to stop threats so you still need to be vigilant.
12. Keep software up to date
One way malware can get onto your device is through the exploit of known vulnerabilities. Developers are constantly patching software weaknesses, but those patches only work if you apply updates to your software.
Do you find they interrupt your workflow? Many operating systems and applications enable you to set up automatic updates at a time that’s convenient for you, for example, while you’re sleeping.
13. Protect sensitive documents
Most of us will have a ton of PII stored on our computers and mobile devices. If these are lost, stolen, or accessed by someone else, there’s a chance the information could be used for nefarious purposes. Encryption can be a great solution for ensuring your data is protected even if your device falls into the wrong hands.
For mobile devices, simply locking it with a strong passcode can go a long way. On your computer, it’s a good idea to encrypt particularly sensitive documents such as tax documents and application forms. File encryption software enables you to selectively encrypt files and folders such that they can only be accessed with a password.

14. Request information from companies
Depending on where you’re located, you may have the right to find out exactly what information a company has stored about you. You should also be able to request that the information be deleted. It is worth noting that rules tend to be different for children.
Depending on where you live, you can ask Google to remove your personal information from search results. Here’s the form for users located in the EU. Unfortunately, it’s not as simple for users in the US and information has to meet certain criteria before Google will remove it.
15. Remove yourself from people searches
There may already be a ton of your PII floating around on the web that you don’t know about. People search engines like Intelius and TruthFinder store data on residents of the US and similar tools exist in the UK, Canada, and other countries. While it may seem hopeless, you can actually apply to have your information removed from these sites.
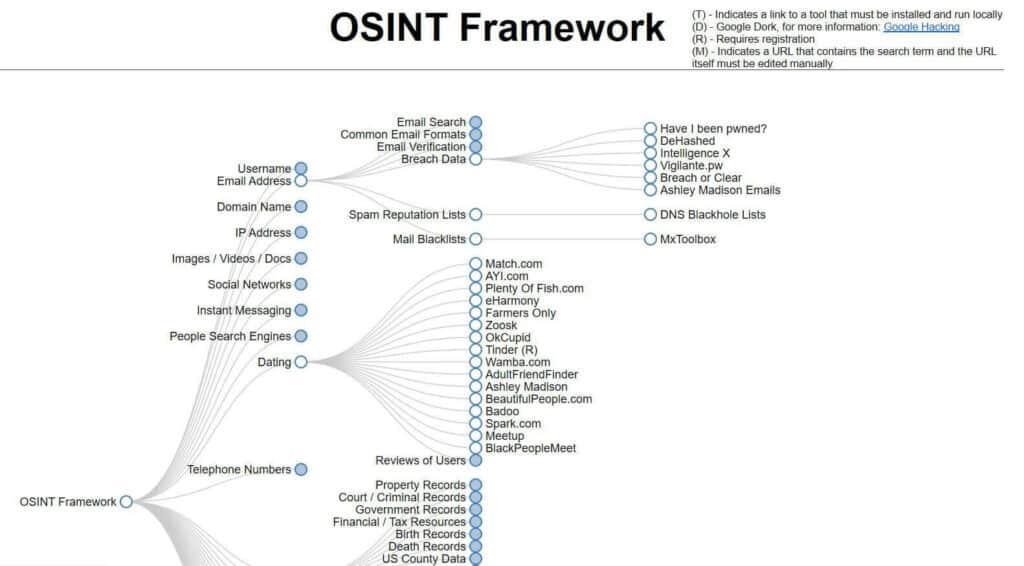
And it’s not just people search engines that hold information about you. You may be surprised to find out where your information is floating around. Looking at the OSINT (Open-Source Intelligence) framework is a real eye-opener for some.
This framework maps out the many places that people could discover information about you. It has positive uses such as helping to locate missing persons or learn about suspected criminals, but it could just as easily be used for nefarious purposes. It makes sense to use the OSINT framework to your advantage to stay one step ahead of criminals.
L’article What is PII and how can you protect it? est apparu en premier sur Comparitech.




0 Commentaires