Containers offer a way of ensuring software solutions – enterprise or otherwise – run smoothly regardless of the environment they are running. For example, thus, they have practical applications when these solutions need to be moved from a development environment into a production one or from a physical one into the cloud. Furthermore, enforcing container security prevents these solutions from being compromised during these migration stages and during their time of residence on temporary hosts.
And, the best way of maintaining the solutions’ integrity is by using the best container security tools we will be seeing.
The seven best container security tools, in brief, are:
- Datadog Easy-to-install, easy-to-use container tool for detecting and investigating threats in real-time. It offers round-the-clock dynamic protection to the whole stack and detailed insights into audit data for threat analysis and proof of compliance.
- Anchore Versatile and open-source container security tool that integrates well; it is fast and efficient and offers CLI interfaces for optimal access. In addition, it performs deep inspections on the entire stack and combines with an array of platforms.
- Capsule8 A purpose-built container security tool for Linux systems residing in the cloud and containers; it can pinpoint triggering issues at the individual container level. Furthermore, enforcing makes it easy to resolve issues.
- Bitdefender GravityZone AI-powered security tool for cloud Linux instances. And yet, it is platform agnostic making it a versatile tool capable of protecting hybrid environments. In addition, it offers forensic auditing for easier troubleshooting and quick issue resolution.
- Sysdig Secure A straight-to-the-point, and open source, security tool that performs scanning in real-time. Although it is already efficient straight out of the box, it is also highly customizable to meet unique requirements.
- StackRox A tool owned by Red Hat, it is deployable in any cloud or hybrid architecture. It leverages machine learning, can be integrated with many platforms, including other container security tools, and can even investigate faulty builds.
- Aqua Security A highly scalable tool that keeps itself updated on the latest threats and vulnerabilities. It can be used to protect both Linux and Windows containers, regardless of their deployment platforms. In addition, it has many advanced threat prevention methods that help keep containers safe.
What are cloud containers?
Before we look at the container security tools, let’s look at what a container is.
Containers can be seen as a type of virtual operating system. They can be used to run everything from small microservices and software processes to larger enterprise-level applications. They are self-contained environments that hold all the necessary dependencies – including libraries, executables, binary codes, and any other necessary configuration files – required to run these applications properly.
“Containerization” helps create a self-sufficient and “contained” environment for the solutions to run in.
Some of the major cloud service providers offer containers as a service (CaaS), with the most popular of them being Amazon (AWS), IBM (Cloud Kubernetes Service), Microsoft (AKS), and, of course… Google (GKE).
The difference between containers and virtual machines (VMs)
A point that might need to be clarified here is the difference between containers and virtual machines (VMs).
Well, first, we can agree that both containers and VMs help improve application portability, empower DevOps, and enable IT services.
But, VMs solve infrastructure problems by leveraging servers, while containers solve application problems by leveraging software assets.
Also, VMs are created by including a guest operating system while the containers adopt their hosting server’s operating system and include only their applications’ required dependencies.
This means VMs are usually bulkier and resource-intensive, while containers are more streamlined and focused on catering to specific applications.
What is container security?
Container security is the process of implementing a security and compliance feature on all the stages of a container’s lifecycle – from creation to maintenance and its eventual destruction.
The process involves scanning container images in the continuous integration and delivery or deployment (CI/CD) pipelines and any existing registries. Once they are up and running, containers also need to be secured along with the host they sit on.
Other features included in container security involve incident responses, with forensic data that shows all activity within the containers, and compliance controls to ensure all necessary audit requirements are met.
What is a container security tool?
A container security tool allows for the management, protection, and security of containerized files, applications, systems, and the networks that connect them.
Administrators use these tools to set automated policies that prevent vulnerabilities from being exploited, unauthorized access, role or privilege abuse, and ensure regulatory compliance to various standards.
But, the bottom line is: container security tools are software solutions designed to protect containers and images.
What are the features of good container security tools?
Some features that helped in determining which container security tools belong on our list include:
- The ability to monitor access roles and permissions.
- A centralized policy management capability to enforce rules.
- Ability to scan whole container stacks as well as image vulnerability detection.
- Allowing for a testing environment to capture runtime malware and observe results of policies that are applied.
- Reporting, auditing, and container metadata storage for analysis and proof of compliance.
- Ability to detect runtime malware like unpatched vulnerabilities, insecure configurations, leaked sensitive data, weak credentials, and suspicious activity, including insider threats.
- Price – affordability and the return on investment (ROI) also help decide what solution is worth investing in.
The seven best container security tools
OK; it is time to jump straight in and have a look at the best container security tools:
1. Datadog
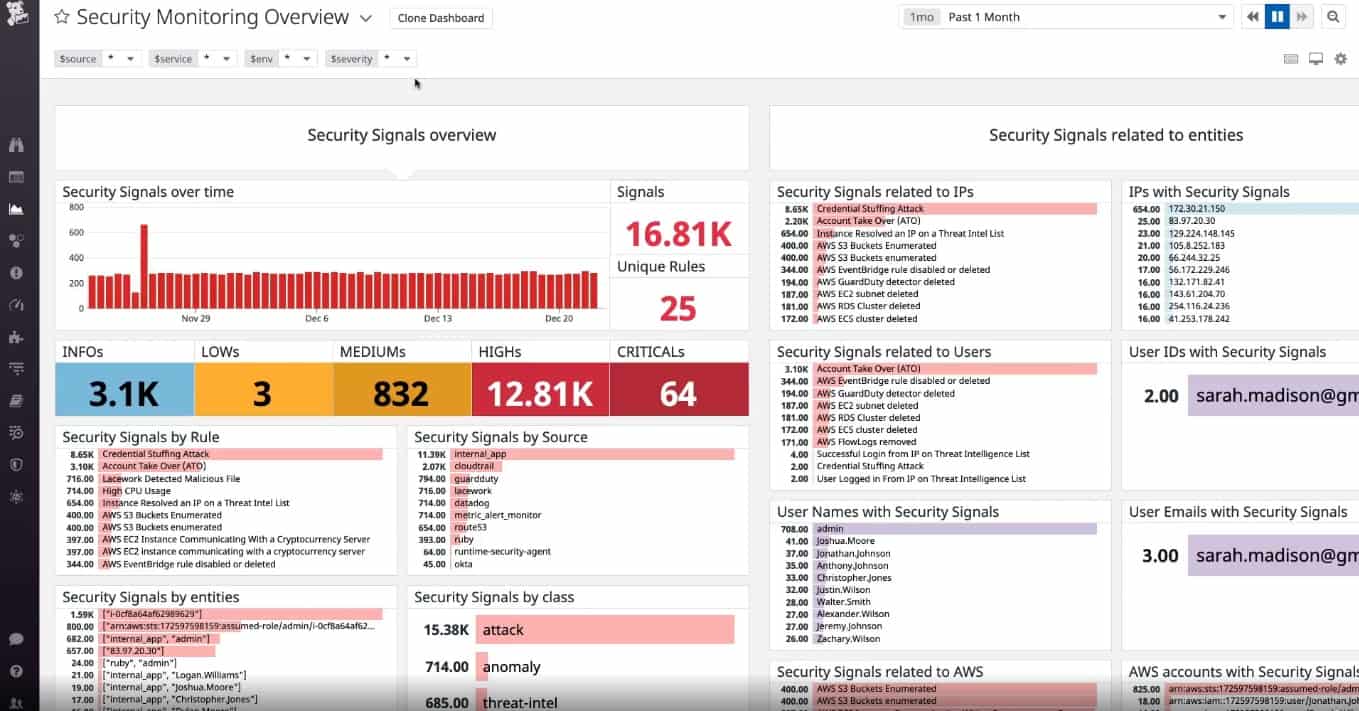
Datadog is a leading provider of SaaS-based data analytics services. The company makes some of the most popular servers and network monitoring and administration tools. They also make Container Security – a container tool for detecting and investigating threats in real-time.
Some of this container security tool’s features include:
- It has the capabilities of protecting the whole stack: applications, containers, hosts, and infrastructure. And since it is itself a cloud security monitoring tool, it adapts easily to dynamic cloud environments.
- Even better, it can flag threats and spot misconfigurations in applications, networks, and infrastructure; it even detects threats from workload security events in seconds.
- Although this security tool is highly configurable and can be scheduled to perform scans, its real-time performance also guarantees the continuous discovery of issues and, hence, round-the-clock protection without any intervention required.
- Administrators can respond to threats faster and efficiently filter security triggers based on key attributes such as severity level residence time, the MITRE ATT&CK framework, or even associated entities, like attackers’ IP addresses.
- Container Security integrates well with communication and collaboration platforms like Slack and PagerDuty, making it easier to keep everyone in the loop via shared actionable alerts or collaborate while tackling identified threats.
- Administrators will find it easy to set up and start running this tool – with minimal configuration – as it comes with over 450 vendor-backed integrations, over 350 pre-set detection rules, and other compliance rules to tackle threats misconfigurations, and run-time
- Administrators will also have their threat analysis backed by detailed observability data, including workload data, application logs, infrastructure metrics, and trail audits.
- Finally, they will be able to carry out in-depth analysis with just a few clicks; they can switch between detailed visualizations and telemetry or audit all cloud configurations quickly and from one place.
Try Datadog FREE for 14 days.
2. Anchore
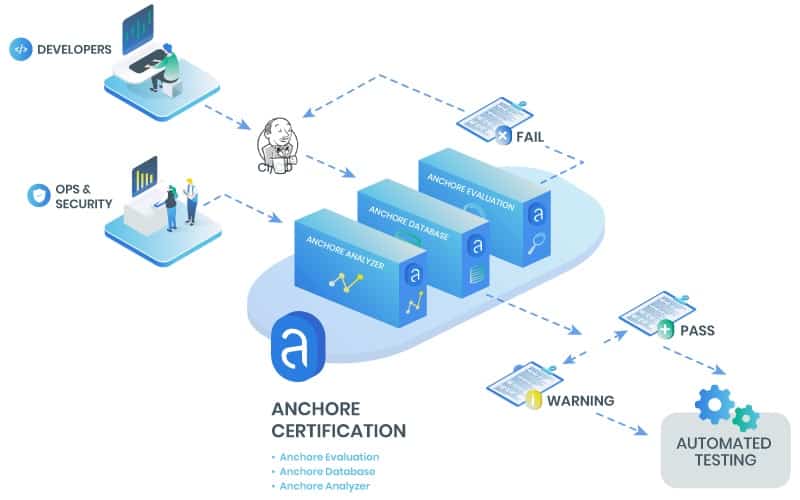
With the Anchore Engine, we get an open-source tool for monitoring the security of container images. Its Enterprise Edition is a complete container security workflow solution that would make any professional administration team happy.
And, as efficient as it is, there is no sacrifice to be made when it comes to speed as it is efficient and requires minimum resources to perform. All administrators need to do is submit a Docker image to Anchore; it will analyze and return details of existing vulnerabilities – if any – in an instant.
Looking at some more features:
- This tool performs as well as it does because it allows for the Anchore Engine to be accessed via a command-line interface (CLI) or REST APIs. The CLI commands can be used to return detailed information on the contents of an image or even scan it to list vulnerability details, threat levels, CVE IDs, and other critical details – without draining resources.
- The Anchore Engine can evaluate Docker images using custom policies which allows for automated validation and certification; it can also certify a Docker image – and report on whether or not it is indeed secure.
- The policies in place – be they custom or default – which can be in the forms of black- or whitelists return “pass” or “fail” results to determine the status of the images and, following which, the necessary actions can be taken.
- It performs deep inspections of container images, OS packages, and software artifacts searching for vulnerabilities, exposed configuration files, image secrets, and unprotected or open ports – to name a few examples of issues it looks out for.
- Anchore is a versatile tool with a handful of setup configurations: it can run as a standalone solution or on orchestration platforms like Kubernetes, Rancher (Kubernetes-as-a-Service), Amazon ECS, or Docker swarms. Anchore is also available as a Jenkins plugin (among many others) to scan CI/CD pipelines.
- This tool integrates well with a wide selection of development tools and platforms – a few examples include Slack, Jira, Oracle, and Microsoft Teams.
Request an Anchore demo for FREE.
3. Capsule8

Capsule8 is the tool for security and compliance control of Linux systems running in any environment, including all cloud computing formats, orchestrators, containers, and CRI-O.
This tool tracks and stops any unsolicited activity in a Linux system that could jeopardize containers. Its detection algorithm was specially created for the cloud and the threats that occur within them.
Some more features include:
- It pinpoints threats that harm the workloads and not just the hosts. For example, the company has a dedicated research team that works on container escapology that continually tests for container escape exploits of Linux kernel vulnerabilities.
- It protects containers from runtime security threats and performance deterrents like program crashes, disabling of native security mechanisms like Security-Enhanced Linux (SELinux), unknown files being executed or starting shells in the containers, and even prevents developers from debugging containers running in a production environment.
- Administrators can create custom policies using container metadata to further extend Capsule8’s protection capabilities while meeting unique environment requirements. Examples of interdiction policies that can be implemented include restricting the containers from writing new files, running new programs after startup, reading cloud metadata, having multiple users, making outbound network connections, and spawning shells.
- The tool makes it easy to pinpoint and troubleshoot triggering events. In addition, it audits and logs container metadata that can be sifted through quickly, thus improving incident response and recovery times.
- Capsule8 operates at the control groups (group) level, unlike most Linux auditing tools that use global configurations. This allows this tool to match every event with a specific control group allowing administrators to detect and identify triggering events at the individual container level.
Request a Capsule8 demo for FREE.
4. Bitdefender GravityZone
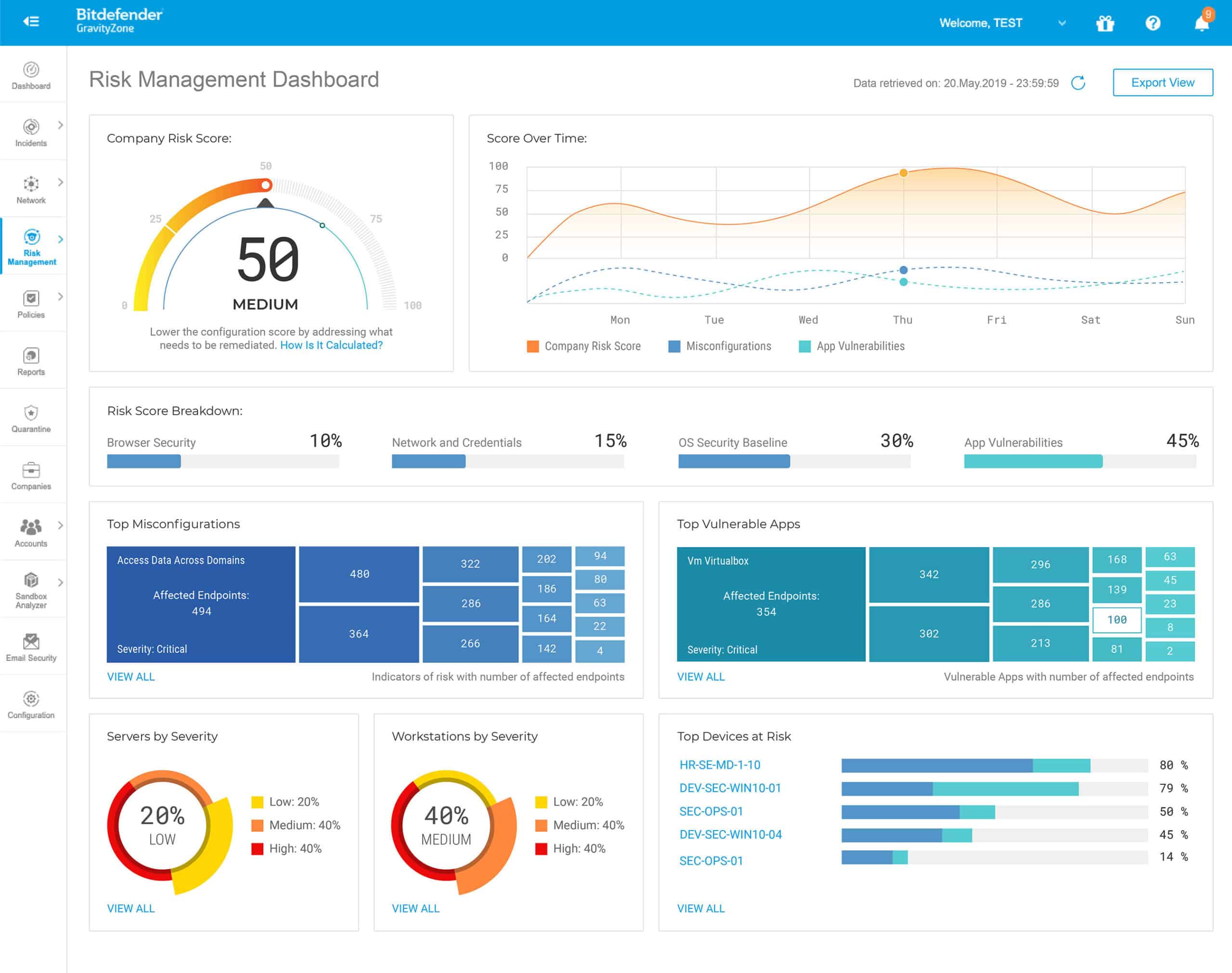
Bitdefender GravityZone is a container security tool that also protects cloud workloads in the Linux environment. It is an AI-powered threat prevention and anti-exploitation solution that is aware of attributes like user, device, and location to provide optimal endpoint threat detection and response (ETDR).
More features:
- Although Bitdefender GravityZone was created for the Linux environment, it doesn’t mean the tool that the endpoint agent requires Linux kernel components; this means it enables deployment of new distributions whenever a move is necessary.
- On the contrary, this tool is platform-agnostic, meaning it offers consistent insight into all containers and workloads that exist across hybrid or multi-cloud environments; it also supports visibility and control across all workloads, containers, OS, and clouds from a central dashboard and defense system.
- It has advanced prevention, detection, and response technologies to stop all sorts of attacks aimed at Linux systems, including container escape attempts.
- Administrators will find it easy to focus their threat analysis and prevention efforts on any security issues that may occur because of the tool’s context-aware incident reports and forensic data logging capabilities. This results in quicker response and resolution times.
Request a Bitdefender GravityZone demo for FREE.
5. Sysdig Secure
Sysdig Secure is another security tool that performs at all stages of a container’s lifecycle. It offers security and compliance features that can stop known vulnerabilities at their earliest before they can cause substantial damage. Thanks to the tool’s capabilities of integrating scanning into the CI/CD pipelines and registries.
More features include:
- Sysdig Secure is precise and to the point – it can flag newly identified vulnerabilities in real-time and at runtime; it matches them to the affected applications and alerts administrators (or delegated technicians) for a fix.
- It also comes with its preset Docket scanning tools; this means it hits the road running right out of the box and immediately starts identifying high-priority vulnerabilities, misconfigurations, or security terrible
- Alternatively, administrators can create their own custom rules to meet unique requirements; they can even leverage community-developed terrible security detections instead of reinventing the wheel and creating alerts triggered by a wide array of issues.
- Then again, they can extend Falco – Sysdig’s open-source threat detection engine – to create and maintain runtime detection policies; this engine uses machine learning to automatically profile container images making it easier to develop custom policies.
- Sysdig Secure also maps compliance standards to their respective container and Kubernetes environment controls; administrators can schedule on-demand assessments and monitor compliance levels using insightful dashboards and detailed reports.
- These assessments can be done even if the container has been destroyed because this tool taps into the Linux syscalls – this is where low-level data regarding any action taken that involves running programs, connecting to devices, for example, is captured in the form of system log files.
- Being an open-source container security tool, on top of being offered as a SaaS service, Sysdig Secure makes it easy for administrators and especially DevOps teams to integrate it into their workflows and configure it to cover the entire stack – with next to no coding required.
Try Sysdig Secure for FREE.
6. StackRox
The very first indication that StackRox is indeed one of the best container security tools available today would be the mere fact that, early in 2021, Red Hat acquired the company it calls “a leader and innovator in container and Kubernetes-native security.”
Well, StackRox is a container security solutions provider that monitors and protects Linux containers regardless of where they are deployed – on-premises, in the cloud, or hybrid architectures.
But that’s not it. Let’s have a look at a few more indicators:
- StackRox is a platform that leverages machine learning-based AI techniques running on a hybrid cloud infrastructure to guard containers against threats continuously.
- Its protection involves end-to-end security processing, including vulnerability management, threat detection, incident response, and even network segmentation as an example of actions to be taken in case of a threat.
- It covers the entire stack – including the containers, images, and Kubernetes – and all the running applications in them; it has a built-in image scanner, for example, that discovers vulnerabilities in them regardless of the languages used.
- The tool identifies vulnerabilities in running deployments – also in real-time.
- StackRox can be used as the primary, stand-alone container security tool or be integrated into existing solutions like Google Cloud Container Analysis or Quay and even other tools like Anchore.
- Troubleshooting and analyzing issues are easy because this tool includes search capabilities in its reporting, allowing filtering for specific information, thus cutting response times.
- When it comes to compliance, there are standards-specific checks for meeting requirements like HIPAA, PCI, and NIST – plus over 300 controls and compliance assessments that can be implemented to ensure audit readiness at all times.
- And finally, StackRox allows administrators to have complete control over their builds – they can fail a build if they find any errors or vulnerabilities in them; in fact, the tool helps them by providing developer details about what critical error caused a build to fail and what to do to fix it.
Request a StackRox demo for FREE.
7. Aqua Security
With Aqua Security, we get a scalable security solution created to protect containerized applications at any stage of their life cycles – from development to deployment.
The tool updates its threat awareness using information from sources like the Common Vulnerabilities and Exposures (CVE) dictionary, vendor update advisories, and research entities – both public and private. This makes it a formidable tool against any current threats and reduces false positive detections.
Here are some more features:
- Aqua Security is highly versatile – it protects both Linux and Windows containers. Even better, it doesn’t matter if the containers are running in VMs, on bare-metals, or as CaaS – they all come under this tool’s protection scope thanks to its purpose-built runtime instrumentations for each environment.
- It offers the in-depth discovery of malware that prevents attacks from malicious code hidden in open source packages and third-party images that could result in credential theft, crypto-mining, or data breaches.
- Analysis of container images is done dynamically using secure, isolated sandboxes where anomalies are examined and monitored closely to spot even the most advanced malware technologies that are usually undetectable using static scanners.
- Policies can be drafted based on the results of both static and dynamic scans that help identify the secure images that can be pushed further down the process workflow or even run in the production environment; the results are gauged and ranked based on a combination of severity (of malware or vulnerability), presence of confidential data, and access to root privileges or permissions before their secure (or unsecured) statuses are determined.
- On the other hand, Aqua makes sure images remain inaccessible using digital signatures; once it has been signed, an image can no longer be changed – which helps stop many attack methods, including (but not limited to) zero-day attacks.
- It has runtime controls that detect and prevent suspicious activities like port scanning and connections to host IP addresses or domains with bad reputations.
- Overall, this tool offers advanced risk mitigation, access limitation based on behavioral profiling, limiting of a “blast radius” – the threat attack surface – using nano-segmentation (i.e., segmenting applications to the most granular extent possible), encrypted secrets delivery, and much more.
Try Aqua Security for FREE.
Why do we need container security tools?
Now that we have seen the seven best container security tools let’s close by visiting why an organization needs to install one.
It comes down to making sure all applications going through the development phase can leverage containers without being compromised – and keeping these containers secure is akin to keeping an organization’s mission-critical software secure.
Let us know if you think a container security tool should be included in this list. Leave us a comment below.
L’article The 7 Best Container Security Tools for 2021 est apparu en premier sur Comparitech.

0 Commentaires