Business processes and decision-making require information as input. While databases have innovated data sharing, much of the important information that needs to circulate to keep your business operating is still file-based.
You need to share files internally and also send files containing essential business documents out to customers and suppliers. If you process credit cards or have some involvement in the US health sector, then you need to be particularly careful with how you handle files the contain Personally Identifiable Information (PII). Similarly, businesses that trade in the EU need to secure and track files containing PII and control where the recipients of files are physically located.
Here is our list of the five best encrypted file sharing services:
- SolarWinds Serv-U Managed File Transfer Server EDITOR’S CHOICE This file server system protects uploads and creates a secure file distribution service through links for access to files on the server. It runs on Windows Server and Linux. Get a 14-day free trial.
- Files.com A cloud platform for file management that enables encrypted transfers, secure storage, collaboration, and link sharing.
- Citrix ShareFile This cloud platform includes encryption for file transfers, storage, and link sharing and can also run process automation.
- FTP Today A secure file server platform, based in the cloud that implements encryption on all aspects of file sharing.
- Tresorit A cloud platform that manages secure file distribution and collaboration and includes encrypted storage space.
There are a lot of issues that you need to cover when assessing file sharing services for use by your company. You need to ensure that information gets to where it is needed without breaking laws and industry standards. Information security is an important priority and encrypted file sharing is fundamental to that goal.
Encryption for file sharing systems
There are three points of vulnerability for files in file sharing systems. Those are when the file is in transit, when the file is at rest, and when the file is opened for viewing through a Web browser. So, there are two types of encryption to examine where considering encrypted file sharing systems.
There are well-established protocols for file transmissions. The oldest protocol available for moving files is called the File Transfer Protocol (FTP). However, this system is not encrypted and not secure. The most commonly used secure protocols used for file transmission are the SSH File Transfer Protocol, which is also known as the Secure File Transfer Protocol (SFTP), and the File Transfer Protocol Secure (FTPS).
The security built into SFTP is called Secure Shell. This is actually a protocol for secure remote access but it has a file transmission protocol built into it, which applies encryption, which is established by SSH to the file transmission packets that occur within an SSH session. The file transfer system doesn’t require a remote terminal session to actually be opened.
FTPS uses the same authentication and encryption services employed for HTTPS. The HTTPS system is the method that makes Web page transmissions secure enough that bank account and credit card details can be passed over the Internet without fear of data theft. That protection system is called Transport Layer Security (TLS).
There are many encryption systems that can be used to protect files on a server. The strongest is probably the Advanced Encryption System (AES). This cipher is considered to be uncrackable in its strongest form, which involves an encryption key that is 256 bits long. Even the weaker 128-bit key would take years to crack by permutation and trial and error, which is called a “brute force attack.” So, AES with a 128-bit key is also, effectively, uncrackable.
Many encrypted file sharing services strengthen security by holding all files on a server and not allowing them to be moved. Instead of sending a file to a recipient, the system sends that person a link to the file’s location on the server. The recipient then views the contents of the file through a Web browser rather than copying it over. Displaying a file in a browser requires that the file’s contents be sent to that browser. This creates a point of vulnerability because snoopers could intercept the transmission. To enforce security, these transmissions are protected by HTTPS, which uses the TLS protection system.
The Best Encrypted File Sharing Services
The requirement to keep information flowing in order to support the business while restricting access to certain data is a difficult mix of priorities. Encrypting files ensures that only authorized personnel and external stakeholders can see the data. Encryption ensures confidentiality because it means that possession of the file is not enough, you also need to be able to decrypt it before the contents are meaningful.
So, encryption goes a long way towards fulfilling the requirement of protecting information from theft. However, that shifts the focus of security measures from access to the file to access to the encryption system.
Effective data encryption is difficult to manage. Therefore, using a file management package that has encryption key control built into it is the most efficient solution available. These systems can tie in with your existing access rights management systems to make secure file sharing even more manageable.
What should you look for in encrypted file sharing services?
We reviewed the encrypted file sharing services market analyzed options based on the following criteria:
- A security management system that implements secure encryption that is bundled into the file sharing service
- The secure distribution of encryption and decryption keys
- A service that optionally can integrate with existing access rights management systems
- Secure file transfer mechanisms
- Storage security
- A free trial or demo version for a risk-free assessment
- A good mix of functions at a fair price that represents value for money.
An encrypted file sharing service needs to allow easy access to files by authorized users while blocking out others. It is also necessary to ensure that those who are allowed access only appropriately use the information those files contain.
The control over appropriate use has to be implemented through company policy and secure working practices. However, the encrypted file sharing service needs to contribute to those practices. This is achieved by logging all actions and putting in place processes that support data disclosure tracing. We took all of these factors into consideration when researching the market for secure file management tools.
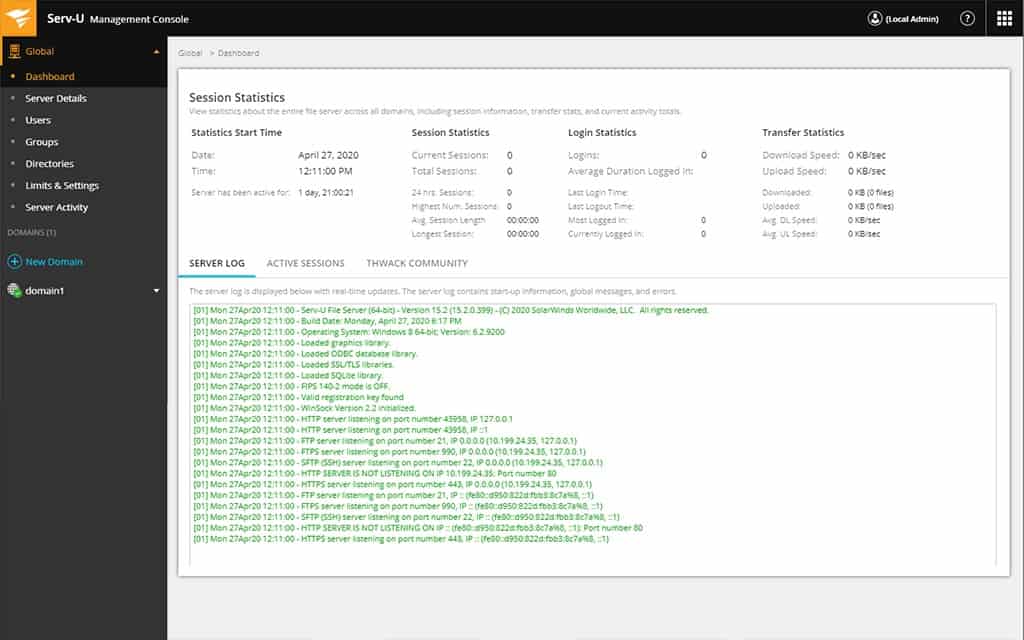
1. SolarWinds Serv-U Managed File Transfer Server (FREE TRIAL)
Serv-U Managed File Transfer Server is a software package that creates a secure file server for your organization. The system creates a central store of files that can be safely distributed or accessed by teams from their central location. The software is able to manage SAN and NAS file server configurations.
The security measures built into the Serv-U Managed File Transfer Server are suitable for use by businesses that need to comply with PCI DSS, HIPAA, FISMA, or SOX. These measures are a combination of access control, encryption, and activity logging.
File transfers to the file server are protected by SFTP or FTPS, which include encryption. The overhead of encryption doesn’t place performance limits on the service – files can be up to 3 GB in size. The service is also able to hand the volumes of traffic that are generated by syncing.
The Managed File Transfer Server doesn’t impose encryption on files stored on the server. However, as this is an in-house system, physical access controls to the server and account access processes make up for that shortfall. Corporate users need accounts to access files on the server. However, this access control can be integrated with the user management services of your existing Active Directory or LDAP systems.
File sharing is implemented through secure link mailing. All users can be authorized via their email addresses. The owner of the file can specify the level of access that a recipient gets and that access can be easily revoked by the file owner or the system administrator. Users access files through any browser or through a special mobile app. This imposes HTTPS encryption on the connection.
Files can be uploaded through any secure file transfer client. The Serv-U site includes a downloadable secure FTP client, which is called FTP Voyager. This client is able to use SFTP and FTPS security, imposing encryption on all file transfers to the Serv-U server in your data center.
Serv-U Managed File Transfer Server is available for Windows Server and Linux and it is offered on a 14-day free trial.
EDITOR’S CHOICE
SolarWinds Serv-U Managed File Transfer Server is our number one pick for an encrypted file sharing service because it enables you to set up your own secure file server for corporate file sharing. The system applies encryption to file transfers and enables access to files on the central file storage through secure link mailing. File viewing is protected by HTTPS with its RSA encryption.
Get a 14-day free trial: solarwinds.com/serv-u-managed-file-transfer-server/registration
Operating system: Windows Server and Linux
2. Files.com
Files.com is a cloud platform that provides a file server function for its customers. Each account on the Files.com system gets a secure area of storage space on the server to hold files. There is an administrator account to start off the customer’s experience of the service. The administrator is able to set up individual accounts for the business’s users. The passwords for those accounts are kept confidential in an encrypted password vault and even the account administrator is unable to read them.
All file transfers are protected by FTPS, which includes Transport Layer Security (TLS). This involves encrypting all file transfers with an RSA cipher that has a 2048-bit key. Viewing access to files is conducted by a Web browser using HTTPS. This is also protected by TLS with a 2048-bit RSA cipher. The server space offered by Files.com is hosted by AWS. It is the AWS S3 service, which is encrypted storage space. Amazon S3 uses the Advanced Encryption Standard (AES) with a 256-bit key.
The main usage for Files.com is to centralize file storage and provide. The administrator can set up shared folders or private folders for each user. The users upload their files to the central store and then grant access to others with their system username or by email address. Access to individual files can also be granted to outsiders by email address.
The file distribution service operates through the permissions granting screen for files. The Files.com system emails out a link to each person who has been granted access. Those recipients then view the file through a browser connection that is protected by HTTPS. The file itself does not move and is not duplicated. The service uses a similar system to secure email attachments. When a user attaches a file to an email, Files.com uploads that file to its storage area and places a link to that location in the email.
You can assess Files.com on a 7-day free trial.
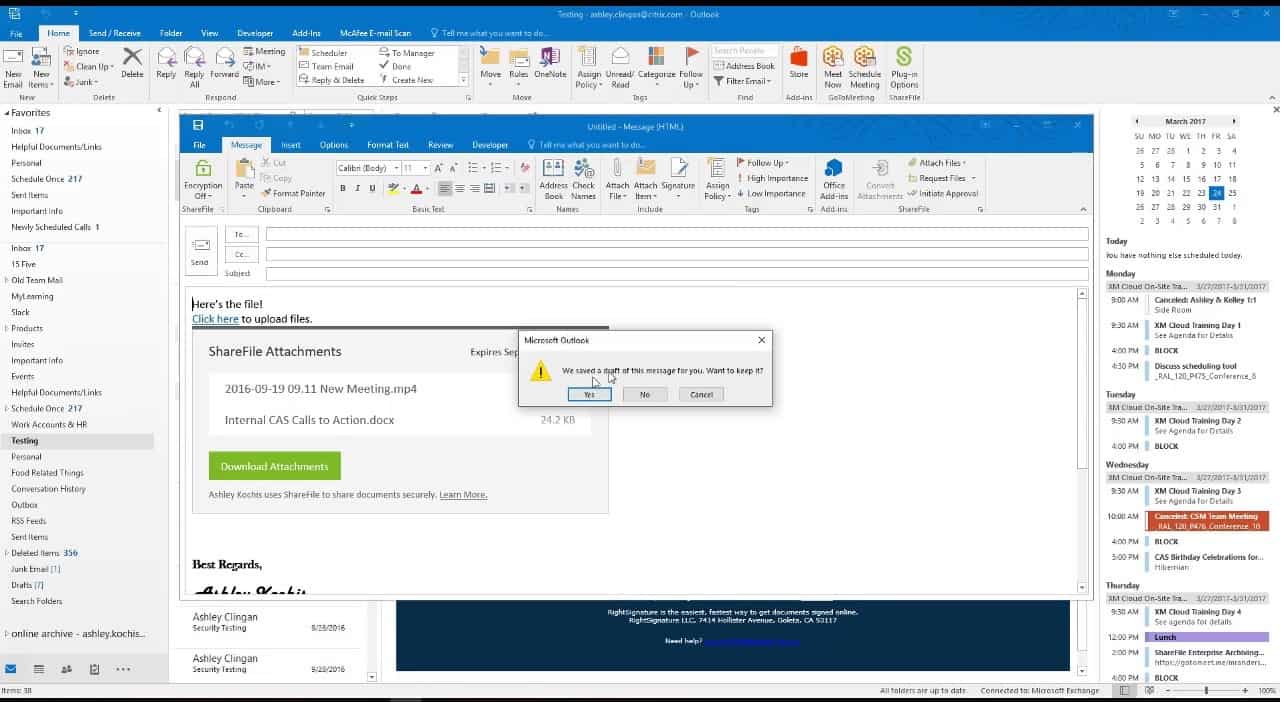
3. Citrix ShareFile
Citrix ShareFile is a cloud platform that offers a number of methods for encrypted file sharing. The service revolves around secure storage space allocated to each client’s account. This file space is unlimited and is protected by 256-bit AES encryption. The administrator of the account can set up password-protected accounts for each of the business’s staff.
Uploads to the ShareFile server are all encrypted individually with a 256-bit AES cipher and then protected in transit by TLS that creates an FTPS connection. The system can transfer files up to 100 GB in size. Once on the server, the files do not move. Instead, users mail out links for secure access. These permissions can be revoked by the file owner or the administrator at any time.
ShareFile integrates with Office 365. This allows groups of users to collaborate on the composition of documents and store them securely. ShareFile also integrates with email applications. It removes any attachments, uploads them to the client’s file space, and inserts a link to the file into the email. Access through a browser to files on the server is protected by HTTPS.
All actions on files are logged with a timestamp and the identity of the user involved. You can a 30-day free trial of Citrix ShareFile.
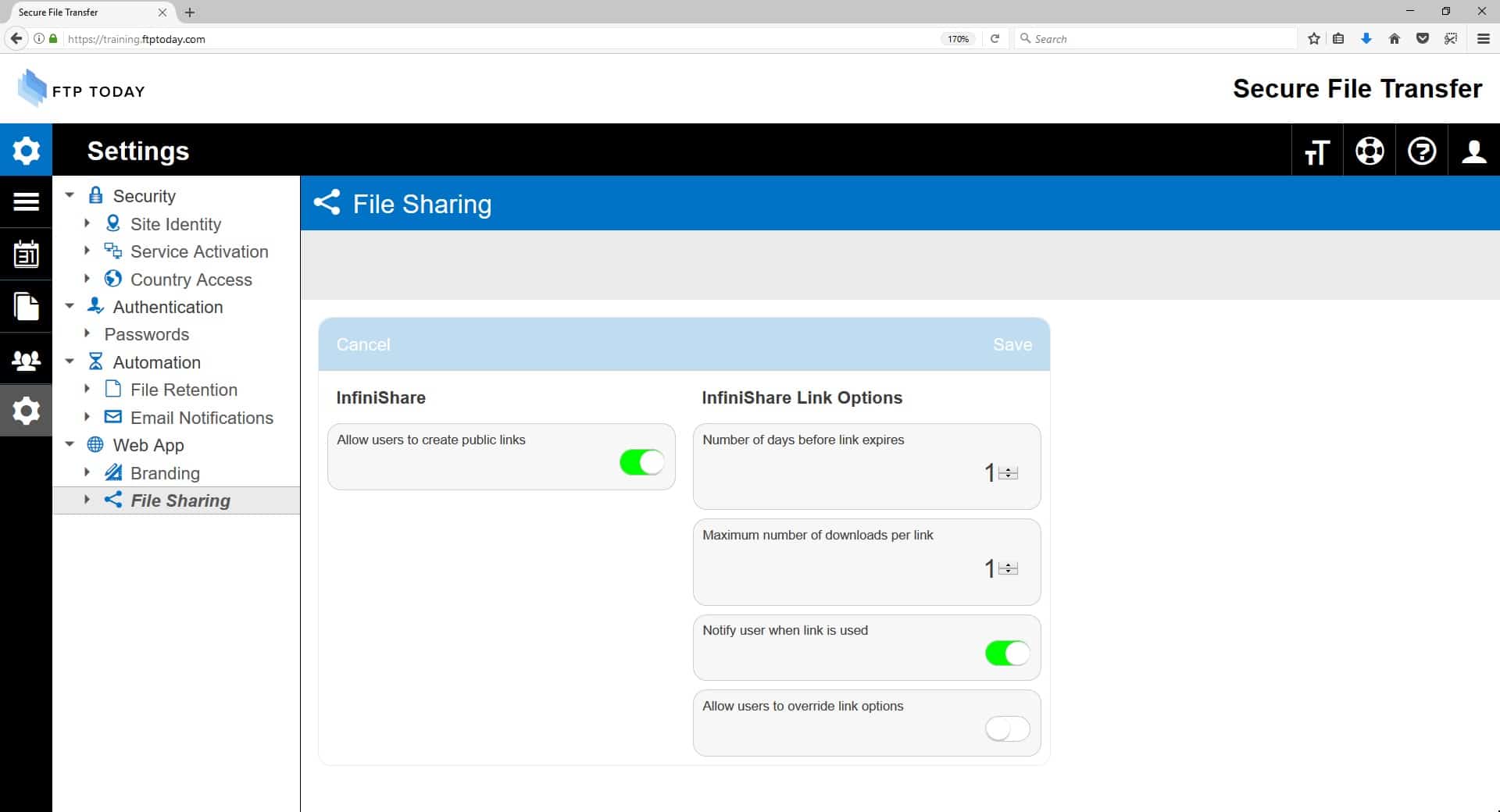
4. FTP Today
FTP Today is a hosted secure file transfer sharing system that includes cloud storage that is protected by 128-bit AES encryption. Transfers are conducted by FTPS, using TLS with a 2048-bit RSA encryption cipher.
FTP Today protects all of its servers with security software and that adds extra protection to all of its customer accounts. Each account has a separate operating system and the service is protected by firewalls and an Intrusion Detection System (IDS).
Access to files is facilitated via a link and through a browser protected by HTTPS.
As well as securing files in transit and on the server, FTP Today offers administrators a range of tools to protect data. It is possible to suspend user accounts immediately and revoke access to files. The system offers geofencing, which prevents authorized users from accessing files if they are physically located outside an allowed area. This is particularly useful for implementing GDPR. It is also possible o block access from specific domains or IP addresses.
You can assess FTP Today with a live demo version or contact the Sales Department to get a 14-day free trial.
5. Tresorit
Tresorit is a file server platform based in the cloud. The service is based on cloud storage space with three editions. The Business Standard users get 1TB of space and Business Plus users get 2 TB. The highest plan, called Enterprise is a tailored plan. Whichever plan you choose, that space is encrypted for protection and access requires login credentials that include multifactor authentication.
Each file stored on the Tresorit server is encrypted individually, each with a different key, so a user can’t get access to any file without specific permission. That encryption takes place before the file is uploaded and uses a 256-bit AES cipher. The file’s encryption gets regenerated with a different key every time the file is changed or when the group of users permitted to access it changes.
Users are invited to access a file through a list of email addresses of permitted accessors. Each directory is called a tresor. It is a sync file that exists both on the owner’s device and on the Tresorit server. A tresor is encrypted by 4096-bit RSA public key encryption in both local and remote locations.
Permission can be graded to allow or block editing and access rights can easily be revoked both by the file owner and by the system administrator. Users grant access to colleagues and outsiders through their email addresses. The system tracks the status of files and, if any changes are made by anyone other than the owner, a message is generated to notify the owner and also write an entry into a log file.
The same processes that protect uploaded files are also applied to email attachments. Those get uploaded to the Tresorit server and then referenced by a secure link that gets written into the email. Uploading and file viewing are protected by TLS.
You can assess the Tresorit system on a 14-day free trial.
L’article 5 Best Encrypted File Sharing Services est apparu en premier sur Comparitech.

0 Commentaires