As your network grows, so does the time administrators spend managing policies across each device. From firewalls to switches and everything in between, this can take a considerable amount of time in an enterprise environment
In the article, we’ll explore the best Network Security Policy Management (NSPM) tools sysadmins can use to cut down the time they spend managing their infrastructure and make life a little easier.
Here is our list of the six best Network Security Policy Management tools:
- SolarWinds Network Configuration Manager EDITORS CHOICE Provides robust security and configuration management across on-premises and hybrid cloud environments.
- AWS Firewall Manager Offers NSPM for AWS environments.
- Change Tracker Gen7 R2 Weaves NSPM with vulnerability management.
- Cisco Defence Orchestrator Solid option, especially for domains that rely heavily on Cisco hardware.
- McAfee ePolicy Orchestrator Offers over 150 integrations, does a good job consolidating multiple security tools into one dashboard.
- Indeni Focus on large-scale infrastructure management – includes features like licensing expiration alerts.
What does a Network Security Policy Management Tool do?
Network security policy management tools help administrators manage devices’ configuration and security settings across their network from a single dashboard. As you can imagine, software like this is potent, especially when networks support thousands of end-users.
NSPM tools can also provide a method for documenting policy changes, auditing network security, and automating policy changes. In some cases, administrators can deploy hardware and configure it through the NSPM tool remotely.
What to look for in a Network Security Policy Management Tool
Some network monitoring tools share a few characteristics of an NSPM but don’t indeed encompass all the features needed to be classified as one. For example, authentic NSPM tools must manage network and firewall configurations, provide an audit log of policy changes, and support frameworks that help meet compliance standards.
In addition to those features, look for products that make it easy to scale your management efforts quickly. For example, automated configuration management can save config files and push them out over the network to ensure all new devices are set up correctly.
Looks for software that supports intelligent alerting for your devices. For example, some NSPM tools can be configured to alert administrators when a policy or setting is changed. This not only helps protect you from misconfiguration but can also alert you of an account takeover or malicious insider activity.
Lastly, NSPM that supports auditing can help technicians cut down on their time troubleshooting issues. A single misconfiguration can cause a wave of helpdesk tickets, especially in a larger environment. By reviewing an audit log of recent changes, NOC technicians can quickly rule out that an internal shift triggered an issue.
With all that said, let’s take a look at our top 6 choices for the best network security policy management tools.
1. SolarWinds Network Configuration Manager (FREE TRIAL)
SolarWinds Network Configuration Manager (NCM) specializes in automating the configuration management of devices and gives sysadmin the power to push updates or roll back and restore devices to a particular state.
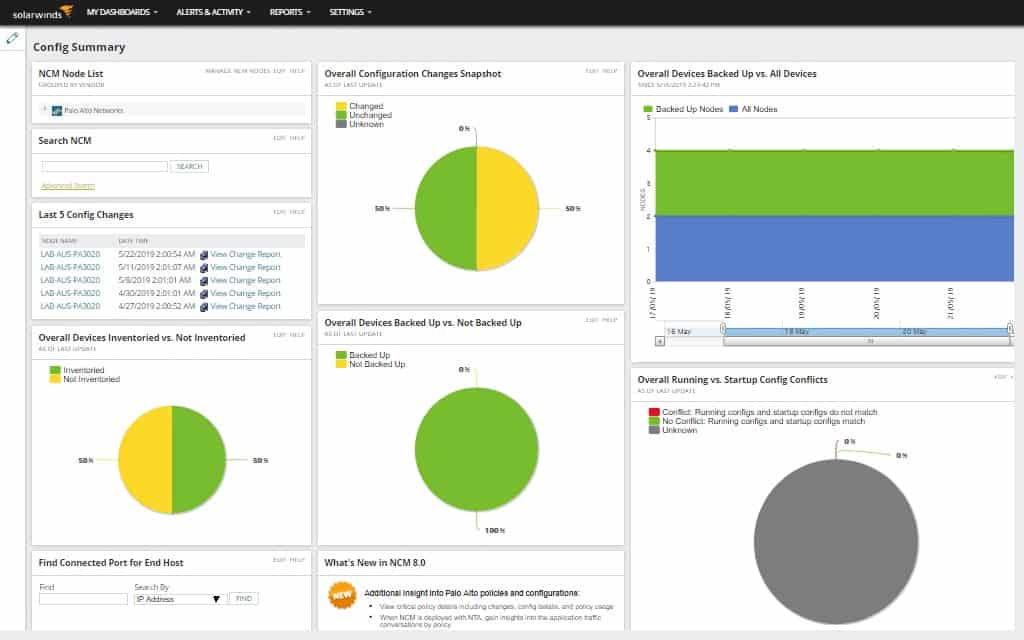
Visually the platform is easy to navigate and makes excellent use of widgets to allow administrators to customize their view or build shared dashboards for network operation centers. I particularly like the bold use of color NCM uses to help key insights stand out over other events.
SolarWinds NCM can automatically crawl a network through auto-discover and build a live inventory list of all your managed devices. Information such as vendor, serial number, and firmware version is easily accessible from a single place. This feature can be used as a form of inventory management in conjunction with your NSPM strategy.
I like that that the platform aims to keep things simple without taking away any features or tools. For instance, if you think a configuration change has caused an issue, you can use NCM to view a side-by-side comparison of your set policy versus what a device has currently. Furthermore, these changes are automatically highlighted and can be reverted quickly.
This view also helps you read into the context of the change, which is just as important as fixing it. Understanding the nature of what was changed and why you can take the correct action to stop it from reoccurring. For example, changes can be made by malware, misinformed staff, insider threats, or simply a lousy policy update. These changes can be paired with alerts, allowing you to always stay on top of the most impactful changes across your network.
NCM helps you stay proactive by providing a simple framework for backing up configurations and maintaining a collection of configuration options to restore to. The platform supports hundreds of different vendor devices that can all be managed from a single place. You can quickly see devices with issues from the configuration management tab—understanding and pushing out changes to that device from a known-good backup file.
The platform offers automated configuration backup that takes snapshots periodically. You can use this to track changes and compare them to your “golden standard” image. This also comes in handy when a device inevitably needs to be replaced. Rather than sending a tech on-site, a staff member can simply plug the device into the network. NCM can automatically identify the device, catalog it, and allow you to push your saved config file to it.
Pros:
- Built for medium to enterprise size networks, with features designed to streamline troubleshooting and improve TTR and overall productivity
- Can automatically discover new devices on the network and provide templated health reports for immediate insights upon installation
- Offers configuration management, allowing teams to quickly backup and restore changes that may have impacted performance
- Can monitor settings for unauthorized changes and specific teams or managers
- Provides a customizable dashboard that has a host of different options for visualizing network performance
Cons:
- Not designed for home networks, this is an enterprise tool built for system administrators and network technicians
SolarWinds Network Configuration Manager starts at $1687.00 and is available through both subscription and perpetual licensing. In addition, you can test out NCM for yourself through a 30-day free trial.
2. AWS Firewall Manager
For organizations that invest heavily in AWS infrastructure, the AWS Firewall Manager can help push out policies to devices and automatically replicate updates across all other devices. While this tool doesn’t offer much outside of the AWS ecosystem, those who rely on AWS Organizations and other Amazon cloud-based services can use this product to provide NSPM.
AWS Firewall Manager supports nearly all AWS products and services and allows you to enable group rules, policies, and configuration changes in a single place. Once those policies are set, they can automatically be deployed across your entire infrastructure.
AWS Firewall manager does an excellent job at allowing you to push changes globally while still maintaining granular control over specific devices your wish to operate differently. For example, you can drive a global security policy change but easily make an exception for your development environment if needed.
One of the best features of this product is its autoconfiguration settings. Newly created resources and devices can automatically inherit your latest set of global configurations. You can also use this same methodology to meet compliance requirements quickly. For example, to meet US Department of Treasury’s Office of Foreign Assets Control (OFAC) regulations, you could deploy a rule to block embargoed countries across your environment.
Pros:
- Supports nearly all AWS devices and infrastructure
- Offers autoconfiguration across multiple accounts and services
- Simple integration into AWS products
- Can quickly implement global policy changes
Cons:
- Is limited to AWS environments
- Technical support fees can be expensive
- Would like to see more “done for you” templates and access rules
3. Change Tracker Gen7 R2
Change Tracker Gen7 R2 provides NSPM through a series of services and combines this offering with security options such as breach detection, file integrity monitoring, and vulnerability management. Additionally, the platform supports multiple deployments, including on-premises and hybrid cloud environments.
Change Tracker aims to provide security through system integrity, with a significant part of policy and configuration management. Device configuration and files can be continuously monitored through the platform, allowing users to push out changes and recover to previous states. In addition, users can set automated planned change rules to revert to a golden image if unauthorized modifications are detected.
The platform help organizations minimize their risk of attack and meet compliance standards through continuous configuration monitoring paired with CIS-based recommendations. This combination lets businesses perform vulnerability mitigation while also managing their configuration policies.
The platform does a great job at assisting sysadmin to make informed policy changes by offering custom security recommendations based on best practices and compliance standards. These recommendations can also alert admins to configuration drift and failed policy updates.
Breach protection helps raise the alarm to unauthorized changes but only does so when it identities changes that are malicious. This is a great feature, as many systems can alert administrators to changes but fail to read the context behind the change.
Change Tracker accomplishes this by using behavioral analytics and baseline monitoring to provide a layer of threat intelligence behind config changes. Additionally, since breach activity is much different than a failed policy update, users can set custom automation and alerts to respond to breach incidents specifically.
Pros:
- Combines NSPM with proactive security features
- Leverages machine learning to detect breaches and account takeovers
- The interface is easy to use
Cons:
- Reporting on a single device could be made easier
- Error messages could be more descriptive to provide faster remediation
- Must contact the sales team for pricing and demo
4. Cisco Defence Orchestrator
Cisco Defence Orchestrator is designed to make managing Cisco firewalls easy across on-premises networks and cloud environments. Currently, the platform can manage security policies across multiple environments, including Cisco Adaptive Security Appliance (ASA), Cisco Firepower, Meraki MX, and Amazon Web Services (AWS).
The product offers continuous scanning across each environment to monitor the supported devices for changes. Once a device is added to the inventory list, Defence Orchestrator highlights inconsistencies, misconfigurations, and other errors so you can quickly change them. A nice added feature is that the platform can also identify changes that can improve performance, allowing you to enhance your security and network performance in a single solution.
Like other NSPMs, Cisco Defence Orchestrator offers low-touch deployment of new devices. Since the platform automatically identifies new hardware, administrators don’t need to travel on-site or have firewalls shipped to them for configuration.
Firmware updates, image upgrades, and configuration changes can all be easily pushed out per device, per group, or globally. This flexibility is great for larger environments and allows MSPs to customize their settings in a way that can be tailored to each client.
On the backend, Cisco provides detailed insights and alerts based on changes identified across the environment. For instance, the tool can identify ransomware, DDoS attacks, insider threats, and even crypto mining within the network.
Pros:
- Great support for environments that heavily use Cisco hardware
- Provides end to end visibility paired with remediation suggestions
- Can easily view uptimes and see when changes were last made
Cons:
- Would like to see more support for other devices/environments
- Could use better insights and daily reports
- Could use more customization options around the dashboards views
- Need better automation options.
5. McAfee ePolicy Orchestrator
McAfee ePolicy Orchestrator strives to provide a single web-based platform for all your security tools and configuration management options. Currently, the McAfee ePolicy Orchestrator supports on-premises environments, AWS cloud deployments, and even a SaaS version managed entirely by Mcafee staff.
Visually McAfee does a great job at providing a clean and clutter-free dashboard that is easy to use. Preconfigured reports easily display metrics like unresolved threats, software status, and recent configuration changes in a single place. In addition, devices can be added via auto-discovery or manually, giving your organization more control over how devices are collected. This option can be helpful, especially in a BYOD environment.
The NSPM works by embracing the native policy and security controls across each vendor and consolidates that access to a single dashboard. This allows you to control everything from Microsoft Defender policies to firewall NAT rules in a single place. This same technique is also used to provide infrastructure maintenance and management at scale.
The platform does an excellent job of highlighting key issues while suggesting recommendations and helping sysadmin improve their workflows. In addition, the platforms come with several pre-configured automated responses designed around specific compliance standards and general best practices.
This lets you get started quickly with the platform without spending hours building rules from scratch. While I am not a fan of McAfee endpoint antivirus, I have to say I was impressed by the quality and ease of use that ePolicy Orchestrator brought to the table.
Pros:
- Great visualizations and central dashboard
- Supports auto-discover as well as manual device collection
- Offers over 150 integrations into different platforms
Cons:
- Would like to see more one-click remediation options
- Onboarding can be made smoother with more assistance and more done for your settings
- Can be taxing on CPU and memory resources
6. Indeni
Indeni focuses on providing automated infrastructure management and security management for on-premises hardware and the cloud for AWS and Terraform environments. The platform is designed to help fix everything from configuration issues to non-compliance in a single platform.
Indeni can also detect systems and environments that are at risk of low availability. This is a good feature for managed service providers or data centers that support many additional customers. The platform can make suggestions that can improve your potential uptime and avoid any unnecessary downtime from a breach or misconfiguration. The platform also does an excellent job at making insights searchable and organizing historical data in a way that makes it simple to demonstrate compliance and review security issues.
Pros:
- Easy to use interface
- Can identity non-compliance
- Supports high availability, great for MSPs and data centers
- Supports config validation and testing before publishing
Cons:
- Would like to see more integration and automation support by default
- The web UI could use improvement
- More preconfigured automated remediation options would be useful
Which Network Security Policy Management Tool is right for you?
We reviewed our top six choices for NSPM tools, but which is the best tool for you? We found SolarWinds Network Configuration Manager to provide the best onboarding experience, ease of use, and ability to automated configuration and security settings with the least amount of issues in almost all cases. In addition, unlike other NSPM tools, SolarWinds NCM supports a vast range of devices and multiple cloud and hybrid cloud configurations.
The one exception is for organizations that own minimal infrastructure and operate almost entirely in AWS. In that case, AWS Firewall Manager offers NSPM services seamlessly across all AWS accounts. The caveat is that AWS Firewall Manager is limited only to AWS.
Do you automate your security policies and configurations? If so, let us know what tools you use for the job in the comments below.
L’article 6 Best Network Security Policy Management Tools est apparu en premier sur Comparitech.





0 Commentaires