
VPNs and Tor are both networking technologies that use encryption and proxies to protect your privacy and data from third parties. So is there any point in using Tor and a VPN at the same time?
Yes! Using Tor with a VPN is a good way to maximize privacy, security, and anonymity online.
So how do you set up Tor with a VPN? Easy. Just connect to a VPN first, and then open Tor Browser or your preferred Tor application. This setup is called Tor over VPN or Onion over VPN.
Quick guide to using Tor with a VPN
If you’re using Tor over VPN, privacy and security are likely important to you. If so, then it’s vital to get a VPN that has your back. NordVPN is our top choice. It employs strong encryption and leak prevention, and keeps no identifying logs of your online activity. It even has Tor connectivity built right in. I’ll touch on that later.
If you’re inexperienced with Tor, I recommend getting started with Tor Browser. It’s a free Firefox-based web browser that routes all incoming and outgoing traffic through the Tor network without much additional configuration necessary to start browsing.
Using Tor with a VPN is easy. Just follow the steps below.
Here’s how to use Tor with a VPN:
- Download a suitable VPN, making sure to select the correct version for your device, and launch the VPN client.
- Open the VPN app and connect to any server. You may want to select a server close to your real location for better speeds but any server will protect your privacy.
- Once your VPN is connected launch Tor Browser.
- That’s it! You’re now protected by both the VPN and Tor browser. Note that protection is limited to activity in Tor Browser and does not extend to other apps or services.
How Tor with a VPN works
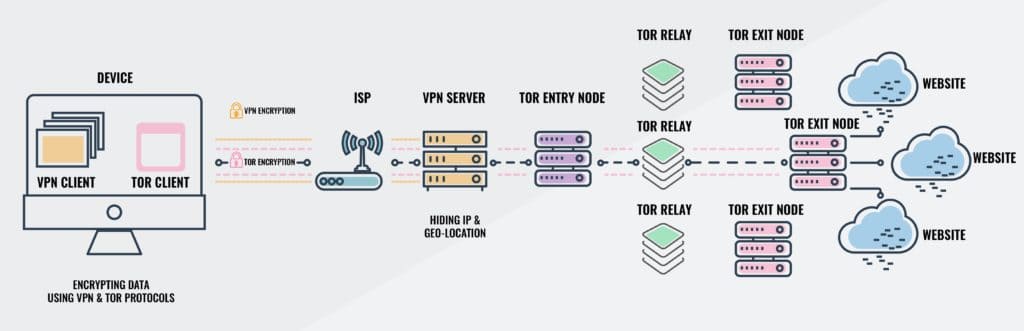
So what’s happening in the Tor-over-VPN setup, exactly? Here’s what the traffic flow looks like for outbound data:
- Data is encrypted by the VPN
- Data is encrypted again by Tor
- Data is sent to the VPN server
- The VPN decrypts the data, but it is still encrypted by Tor
- Data is sent through the Tor network
- If visiting a .onion site on the dark web, data is decrypted upon arriving at its destination. If I visit the clear web, data is decrypted at a Tor exit node and forwarded to the website.
Inbound traffic flow is as follows:
- Data is sent from a website, app, or service
- Tor encrypts the data
- The data is sent through the Tor network to the VPN server
- The VPN encrypts the data again
- The twice-encrypted data is sent from the VPN server to the end user device
- Tor decrypts the data
- The VPN decrypts the data again
Why use a VPN with Tor?
Using Tor with a VPN (onion over VPN) offers several benefits over using either of the two tools alone:
- My ISP can’t see that I’m using Tor
- My VPN provider cannot see what sites I visit or the contents of my connection
- I can access both dark web .onion sites and clear web sites
- I can anonymously surf the clear web
- Tor entry nodes cannot see my real IP address
- I have the option to use the VPN by itself with a normal browser for non-sensitive tasks
But, there are also some drawbacks:
- Websites and apps can see that I’m visiting through a Tor exit node. Some sites might block me or not function well as a result.
- My VPN can see my real IP address and knows I’m using Tor
- I could potentially expose data to compromised Tor exit nodes
- Using a VPN and Tor together will significantly slow down my connection
Note that just because a website or my ISP can see I’m using Tor, it doesn’t mean they can see what I’m actually doing. All my data is encrypted and its destination hidden.
What about VPN over onion?
If we switch up the order in which data is encrypted and transmitted, we get VPN over onion. In this setup, traffic first passes through Tor and then through the VPN, instead of the other way around.
VPN over onion is generally considered less secure and is more difficult to set up, usually requiring assistance from the VPN provider.
But VPN over onion does have its advantages:
- My ISP can’t see that I’m using a VPN
- Clear web sites and apps that normally block Tor traffic will be accessible
- My data is less vulnerable to compromised Tor exit nodes and packet discrimination
But on the downside:
- My ISP can see that I’m using Tor
- I can’t visit dark web .onion sites
- My VPN can see my internet traffic
- Tor entry nodes can see my real IP address
Unlike Tor over VPN, I can’t just set up VPN over Tor without help from my VPN provider. VPN over Tor must be configured on the server so that once data reaches the server, it is then channeled through the Tor network. The vast majority of VPNs do not offer this feature.
VPNs with built-in Tor connectivity
A handful of VPNs come with built-in connectivity for Tor over VPN. That means I don’t need to use Tor browser or any other special apps or tweaks; I just need the VPN app to connect through Tor.
NordVPN is a top-rated VPN provider that offers this feature. NordVPN keeps no identifying logs of your activity and comes with best-in-class encryption. You’ll need to switch to the OpenVPN protocol to access onion over VPN servers.
This feature allows me to use any VPN with Tor, not just Tor Browser. This is especially convenient given that configuring individual applications to use Tor can be tedious and troublesome.
But there is a downside. Compared to the Tor Browser setup discussed above, the VPN provider with built-in Tor connectivity gets an opportunity to log and analyze my data before it’s encrypted by Tor. That could raise privacy concerns for some.
Additionally, users will need to take more care to protect their identities. Using Chrome browser, for example, could still allow websites to identify me through cookies, negating the anonymity benefits of Tor.
See also: Best VPN for Tor
L’article How to use Tor with a VPN: Step-by-step guide est apparu en premier sur Comparitech.

0 Commentaires