Cheetah Digital, a software vendor working on behalf of UK energy and home services provider British Gas, exposed an email server on the web containing 3.6 million British Gas customer email addresses along with timestamps and email subjects. The data, discovered by Comparitech researchers, could be accessed without a password or any other authentication required.
Bob Diachenko, who leads Comparitech’s cybersecurity research team, reported the exposure to British Gas on April 30, 2021. Centrica, British Gas’ parent company, acknowledged the incident, and Cheetah Digital secured the data a day later.
The data, if accessed by malicious parties, could be used to target British Gas customers with scams and phishing emails, using the exposed data to tailor more convincing and personalized messages.
Centrica responded to Comparitech with the following statement:
“We are aware that some of our customer email addresses had been exposed by a third party marketing agency, who then took swift action to ensure this data was removed immediately. We can confirm no passwords or financial information was shared, but email addresses of some customers who had subscribed to marketing notifications had been made visible online. We’re sorry this happened as we take the protection of our customer data extremely seriously and we expect our third-party partners to apply the same high standards. Our supplier has now assured us they have put further measures in place to ensure this can’t happen again“
The software vendor that exposed the data, Cheetah Digital, gave the following statement:
“In early May Cheetah Digital became aware of a misconfiguration in an isolated system that allowed an external security expert to access email addresses belonging to a UK client. The misconfiguration was immediately addressed, fixed, and a formal investigation initiated. The results of the investigation confirmed that access was limited to the external security expert. Cheetah Digital takes the protection of its clients’ data very seriously and is confident the measures and additional safeguards implemented have fully remediated the issue.”
British Gas serves 12 million homes in the UK and is the biggest energy supplier in the country.
Timeline of the exposure
Here’s what we know happened so far:
- April 29, 2021: The database was first indexed by search engines.
- April 30, 2021: Diachenko discovered the data and immediately alerted British Gas as per our responsible disclosure policy.
- May 1, 2021: Cheetah Digital secured the data.
We do not know for how long the server was exposed prior to being indexed by search engines, and we do not know whether any other third parties accessed it during that time. British Gas and Cheetah Digital say they didn’t find any third parties other than Diachenko had accessed the data.
Our honeypot research shows attackers can find and access unprotected servers in a matter of hours.
What data was exposed
British Gas tells Comparitech that the exposed email addresses belonged to customers who subscribed to marketing communications with the company.
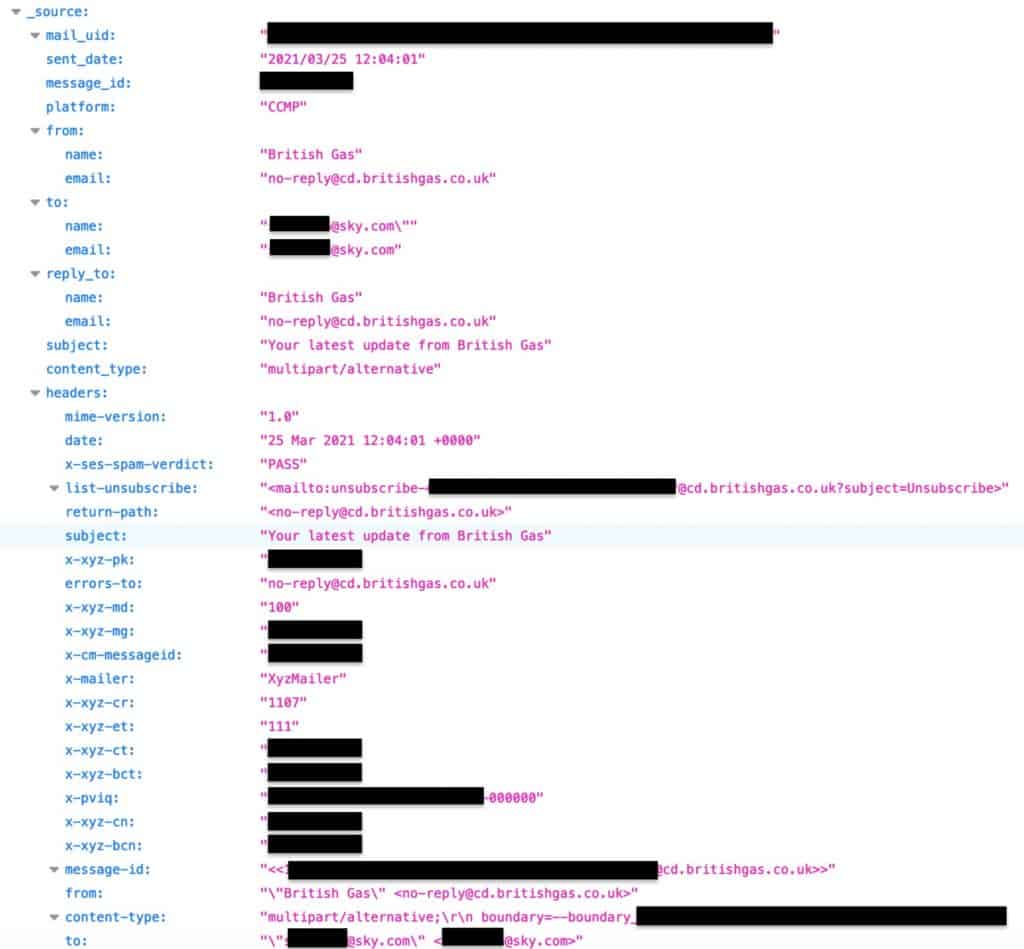
Diachenko found the mail logs exposed on an Amazon Elasticsearch server. In total, 18,065,470 records were exposed. Those records contained about 3.6 million unique email addresses. Each record contained all or some of the following info:
- Customer email address
- Email subject lines
- Dates of emails sent and received
- Message IDs
While we are pleased to report that it appears no payment information, email body contents, passwords, or other customer information was exposed, there are still dangers created by the incident (see below).
Dangers of exposed data
British Gas says there was no evidence of malicious activity during the exposure, though we still recommend affected customers take precautions.
British Gas customers should be on the lookout for phishing emails from scammers posing as British Gas or a related company. Fraudulent emails will try to trick victims into clicking a link to a phishing site. The site will appear legitimate in order to convince victims to enter a password or payment information, which is then stolen.
Here are a few tips for spotting phishing emails:
- The sender tries to instill a sense of urgency in the victim. If you feel rushed, stop to consider it might be a scam. For a utility, this might include threats about delinquent bills, necessary upgrades or repairs, refunds, or suspending your service.
- Check the domain (whatever comes after @) of the sender’s email for spelling errors. Compare it against official British Gas email addresses.
- Never click on links or attachments in unsolicited email.
- Don’t be afraid to call British Gas directly to ask about the email
The data could also be used in utility fraud, in which the fraudster signs up for a utility or continues existing service in someone else’s name. No names or other personal info was contained in the database however, so such an attack would likely require additional info.
About British Gas and Cheetah Digital
British Gas is the biggest energy supplier in the UK, providing electricity and gas to more than 12 million homes and businesses. It is a subsidiary of Centrica Plc.
This isn’t British Gas’ first data incident. Previous incidents leaked more sensitive info but happened on a much smaller scale:
- In 2015, it exposed the email addresses and passwords of 2,200 customers.
- In 2017, British Gas announced that a third-party website exposed the login details of 1,600 customers.
Cheetah Digital is a US-based software vendor founded in 1998. It specializes in marketing and customer engagement, including analyzing market data and deploying targeted marketing campaigns. Its other clients include Walgreens and Shell (neither of which were affected by this incident).
Why we reported this data incident
Comparitech researchers routinely scan the internet for vulnerable databases containing personal information. When we find such an unprotected database, we immediately start an investigation to determine who is responsible for it, who is impacted, what types of data are exposed, and what potential consequences the data subjects might face as a result.
Once we identify the owner, we promptly send an alert per our responsible disclosure policy so that the data can be secured as quickly as possible. We then publish an article like this one to raise awareness and curb harm to end users.
Previous data incident reports
Comparitech has published many data incident reports like this one, such as:
- India visa agency exposes 6,500 traveler’s visa applications on the web
- Utah COVID-19 testing service exposes 50,000 patients’ photo IDs, personal info
- Car dealer marketing service Friendemic exposes 2.7 million consumer records
- Gym chain Town Sports exposes 600,000 records of members and staff
- Prison phone service Telmate exposes messages, personal info of millions of inmates
- Social media data broker exposes nearly 235 million scraped profiles
- UFO VPN exposes millions of logs including user passwords
- 42 million Iranian “Telegram” phone numbers and user IDs were breached
- Details of nearly 8 million UK online purchases leaked
- 250 million Microsoft customer support records were exposed online
- More than 260 million Facebook credentials were posted to a hacker forum
- Almost 3 billion email address leaked, many with corresponding passwords
- Detailed information on 188 million people was held in an unsecured database
- Over 2.5 million CenturyLink customer records leaked
L’article British Gas software vendor exposes 3.6 million customer email addresses on the web without a password: report est apparu en premier sur Comparitech.


0 Commentaires