Attack surface monitoring tools help you to identify the risks that your software presents to data security.
Attack surface analysis and protection is the software equivalent of vulnerability management, which focuses on device settings and operating system exploits.
Here is our list of the eight best attack surface monitoring tools:
- Rapid7 InsightVM EDITOR’S CHOICE Part of a security platform, this vulnerability manager can be supplemented by a research feed that sweeps records for third-party risk. This is a cloud-based system.
- Bugcrowd Asset Inventory A hacker-developed asset tracking service can read through supporting service layers and monitor their security. This is a SaaS system.
- Digital Shadows SearchLight A threat intelligence research service that looks through hacker message boards and other Dark Web channels to reveal planned attacks on their clients.
- CoalFire Attack Surface Management A capable asset tracking system that looks at the weak points in external systems that can provide entry points for hackers. This is a managed service.
- OWASP Zed Attack Proxy an accessible and highly regarded vulnerability scanner that a free Attack Surface Detector can enhance. Available for Windows, macOS, and Linux.
- Burp Suite Enterprise An excellent vulnerability scanner can be added to with the free OWASP Attack Surface Detector. Available for Windows, macOS, and Linux.
- ImmuniWeb Discovery A combination of a vulnerability scanner, an attack surface monitor, and a tailored threat intelligence feed based on tracking hacker intel. This is a cloud-based service.
- CyCognito Attack Surface Management A cloud-based external asset discovery service performs continuous penetration testing on exposed program units. This system also includes third-party risk assessments and system hardening recommendations.
You can read more about each of these systems in the following sections.
Attack surface monitoring tools provide Attack Surface Management (ASM). This is a continuous process because there are new exploits discovered all of the time. ASM involves two phases of research. First, you need to know what data you hold and what sensitivity ranking each piece of data holds. Secondly, you need to have an accurate software inventory.
With complete system documentation in place, an attack surface monitoring tool can start to search for the typical inroads that hackers are known to use. DevOps environments can integrate ASM into their CI/CD pipeline to head off potential problems with new functions and features.
Attack surface monitoring
The development of new attack strategies by hackers means that attack surface monitoring can’t sit still. You also have an issue with further data services and software packages to watch over. No system is static, and so attack surface monitoring needs to be an ongoing task.
The field of attack surface monitoring is relatively new. There aren’t many tools available for this task at the moment. If you are not satisfied with the few attack surface monitoring tools currently available, you could rely on a vulnerability scanner because some of these also cover software vulnerabilities.
One step back from outright attack surface monitoring and vulnerability management, you could rely on Intrusion Detection Systems (IDSs). These look for any malicious activity on your system, including data theft events. Another category of software that would come in useful as an attack surface monitoring substitute is data loss prevention (DLP). The critical aim of attack surface monitoring is to protect data stores from unauthorized access, which is the same as DLP systems.
The best attack surface monitoring tools
The blur between vulnerability management and attack surface management means that some vulnerability scanners advertise themselves as attack surface monitors. At the same time, many vulnerability managers also offer attack surface monitoring without explicitly using that term in their product descriptions.
What should you look for in an Attack surface monitoring tool?
We reviewed the market for attack surface monitors and analyzed the options based on the following criteria:
- A system that checks software for vulnerabilities
- A service that identifies out-of-date software versions
- A monitoring tool that logs data access by software
- A monitor that can distinguish between valid user activity and suspicious account activity
- A service that reduces the risk of sensitive data loss or disclosure
- A free trial or a demo version for a no-cost assessment
- A comprehensive tool that protects sensitive data by identifying software security weaknesses
As the term “attack surface” is relatively new. We don’t rely on that phrase being in the name or description of a security system included in our considerations.
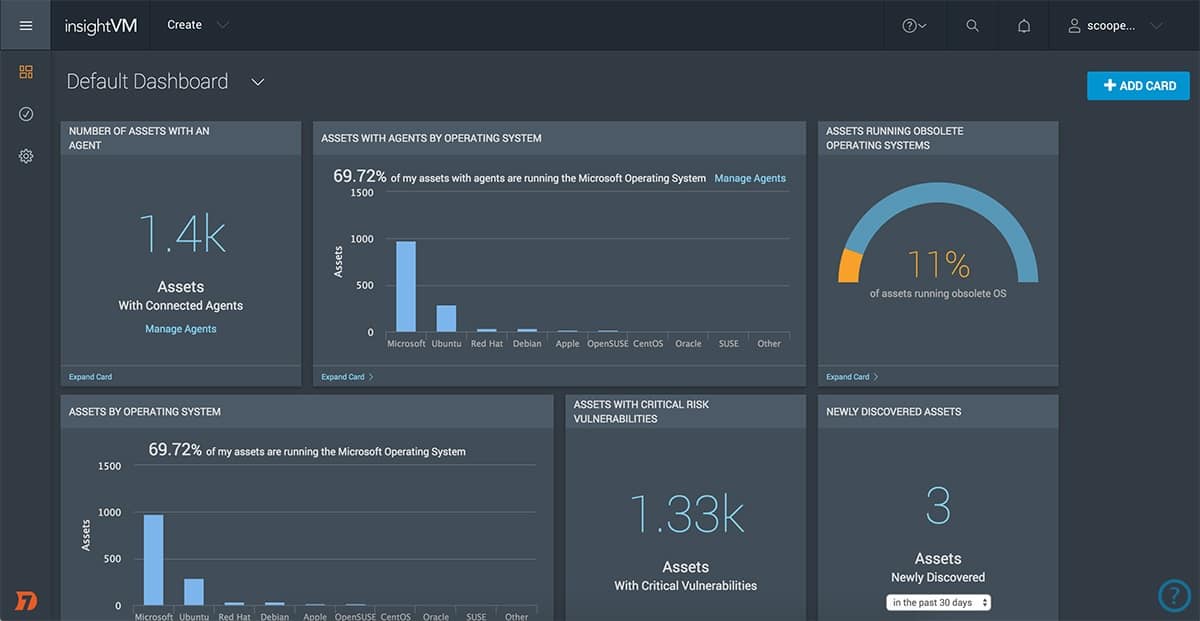
1. Rapid7 InsightVM (FREE TRIAL)
Rapid7 InsightVM is a vulnerability manager rather than an attack surface monitor. However, it has some beneficial features that make it a good tool for external attack surface management. This system scans cloud and virtual systems as well as the endpoints and devices on the network. The tool itself is cloud-based, so it isn’t bound to checking on just one network. It is equally suitable for checking on endpoints on remote sites and even in the homes of telecommuting staff.
Rapid7 has one other feature that can enhance the attack surface assessment capabilities of InsightVM. Project Sonar gathers data loss event notifications and additional information on security problems with different companies. This pool of data can be used to form a third-party risk assessment on the businesses that run services used by the client.
InsightVM is part of a suite of tools that can protect a network from attack, and one of its services, a SIEM tool, includes a threat intelligence feed. This feed identifies any channels currently used by hackers to get into networks. This has software vulnerabilities, which provide an attack surface protection service. Rapid7 offers InsightVM on a 30-day free trial.
EDITOR’S CHOICE
Rapid7 InsightVM with Project Sonar is our top pick for an attack surface monitoring tool because it adds a third-party risk assessment system to a vulnerability scanner. While not being an exact match for an attack surface monitor, the high reputation of Rapid7 in the field of cybersecurity tools and the combination of all of the complementary tools that can be used alongside InsightVM make this a very tempting proposition.
Get a 30-day free trial: rapid7.com/products/insightvm/download/
Operating system: Cloud-based
2. Bugcrowd Asset Inventory
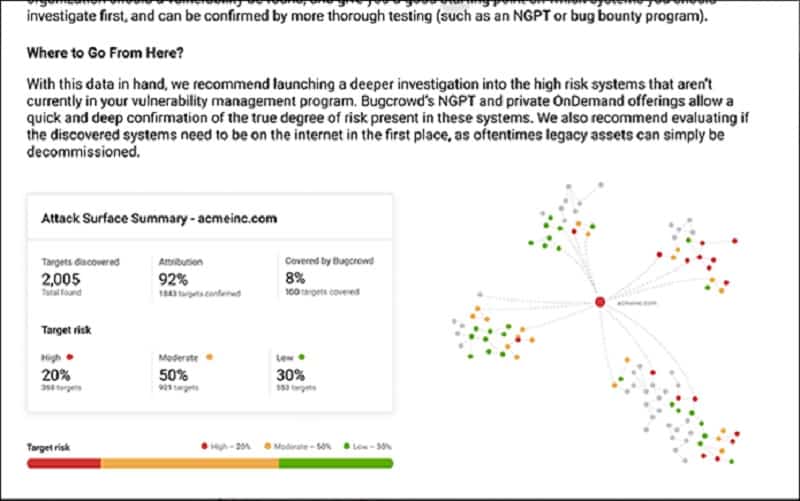
Bugcrowd Asset Inventory is an exciting proposition. This is an automated tool developed by white hat hackers. It is a crawler that searches through linked software packages, and it is used as a pen-testing system to discover the software and services used by a client. This system particularly chains through to all of those APIs and microservices that provide plug-in services for Web page functions.
Bugcrowd explains that a third of all attacks get into a business through software and services that the company’s IT department doesn’t even know that they are using. You can’t protect systems that you don’t see that you use. The system then watches over those newly-discovered assets and alerts the client if it detects any security risks on them.
Customers who want a tailored service can commission human-based searches of their system. This is an actual pen-testing exercise because Bugcrowd puts a bounty on your company’s systems and invites some of the leading whiter hat hackers worldwide to break in, awarding the prize to the first hacker in. This service is called Asset Risk.
Bugcrowd Asset Inventory is a cloud-based service, and you can request a demo to see it for yourself.
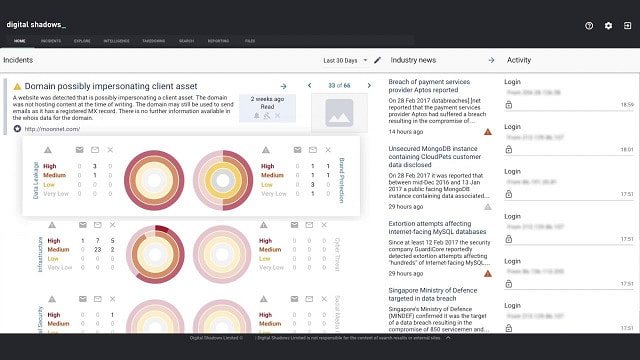
3. Digital Shadows SearchLight
Digital Shadows SearchLight is an attack surface monitoring tool that checks a client’s software assets against circulated intel being shared by known hackers. This is a valuable service for keeping vigilant against external threats. Most threat intelligence feeds record attack strategies that have already been implemented against other companies. SearchLight alerts companies that they are about to be attacked.
You register your outward-facing assets on taking out this service, such as brands, product names, IP addresses, and domains. The SearchLight system then keeps a constant eye out for mentions of these names and addresses. An example of the kind of information that the service can pick up would be the contact details or even the system login credentials of an employee being circulated on the Dark Web.
SearchLight analysts, using crawler and data analysis tools, identify potential attacks on one of the clients that they protect. The type of data detected on a client indicates the direction that an attack will take. With this warning, SearchLight can inform the client of the upcoming episode and which parts of the system to harden in defense.
While not providing a total cybersecurity solution, this is a beneficial service that would be a valuable addition to any attack surface monitoring strategy. You can get a look at Digital Shadow SearchLight on a 7-day free trial.
4. CoalFire Attack Surface Management
CoalFire Attack Surface Management is on this list because the company understands that the significant risk to companies lies in those easy-to-integrate APIs and plug-ins that deliver instant functionality. However, when developing a website or Web service, no one stops to wonder precisely where those functions are run and whether or not their providers have any security in place.
Once a website is up and running, it is tough to unpick and rewrite it. For one thing, such an exercise would be very costly and difficult to justify to the company accountant. CoalFire crawls through websites and lists all of the external services that they have integrated. While automated processes discover all of the chains of assets that contribute towards a client’s systems, human analysts verify these findings.
With the complete asset inventory in place, the business can develop a defense strategy. CoalFire doesn’t include a SIEM or an intrusion detection system. However, it gives you guidance on the correct defense software that you need for your digital profile.
CoalFire assesses the risk of the connections between a company’s network and remote sites and remote workers along with the extended asset inventory. All of the different circumstances of a business’s operating procedures go into the CoalFire risk assessment, which constitutes a thorough attack surface definition.
5. OWASP Zed Attack Proxy
OWASP Zed Attack Proxy is a free, open-source Web app scanner. The tool searches through a website for the OWASP Top 10 threats. This is an efficient vulnerability, and the Top 10 produced by this organization is the industry touchstone for all vulnerability scanners.
The second project of OWASP that can be plugged into the Zed Attack Proxy makes it an attack surface monitor. This is the Attack Surface Detector. This service can trace through APIs and Web services, making it a great discovery tool for attack surface analysis.
The Detector locates the hosts for discovered applications, and then it notes the parameters for the call and their data types. Another valuable feature of the Detector is that it will scan an app and store its code. The system can be used to regularly rescan those discovered functions and compare its code to the stored version, identifying changes that could introduce new vulnerabilities or even include new backend functions to trace through to.
OWASP Zed Attack Proxy and the OWASP Attack Surface Detector are available for installation on Windows, macOS, and Linux.
6. Burp Suite Enterprise Edition
Burp Suite is a package of penetration testing tools. The system is available in three editions. These are a Community Edition, which is free to use, a paid Burp Suite Professional package of tools, and Burp Suite Enterprise, an automated vulnerability scanner. Burp Suite Enterprise is designed for use by DevOps operations and software development companies.
Burp Suite is presented here as an alternative to the OWASP Zed Attack Proxy. Both tools have excellent reputations, and both are ideal vulnerability scanners. Like the Zed Attack Proxy, Burp Suite Enterprise can be enhanced by the OWASP Attack Surface Detector for free. So, the benefits described above are also available for users of Burp Suite Enterprise.
Burp Suite Enterprise is a sophisticated tool, and it is not free. The service is offered in three packages: Standard, Grow, and Accelerate, with from five to 50 scanning agents, depending on the plan. Burp Suite Enterprise installs on Windows, macOS, or Linux, available for a free trial.
7. ImmuniWeb Discovery
ImmuniWeb Discovery includes various security services that amount to both a vulnerability scanner and an attack surface monitor. This system discovers all software assets on-premises and through to cloud services. It can trace through APIs to find the hosts of the code. It also includes a vendor risk management service by tracking any disclosures or security events experienced by them.
The ImmuniWeb system also scans the Dark Web looking through regular hacker communication channels for credentials sales or intelligence gathering attempts that concern the assets of the service’s clients.
So, the ImmuniWeb service covers both internal weaknesses and external threats. It produces system hardening recommendations and alerts businesses to the shortcomings in their code suppliers.
The ImmuniWeb service is offered in three levels: Express Pro, Corporate, and Corporate Pro. These systems are provided on a monthly subscription, with Corporate Pro being the complete feature package at the highest price. The Corporate Pro system is also available for on-demand scans of third-party systems, which h are charged per assessment. ImmuniWeb Discovery is delivered from the cloud, and you can get a demo of the system.
8. CyCognito Attack Surface Management
CyCognito offers a cloud platform of security tools that include a vulnerability manager and the Attack Surface Manager.
The CyCognito system is an external attack surface monitor. It identifies your public-facing IT assets, principally websites and Web services. The service traces from those initial assets through to the APIs and services that contribute to them. This is a valuable tool in itself because it lets you know exactly what code is contributing to your websites and what companies are behind them.
The system includes third-party risk assessment and an attack surface monitor that operates as an automated vulnerability scanner. The CyCognito system constantly attempts hacks on each point in the chain of services that contribute to your websites, probing them for weaknesses, which can change over time. It ranks each unit’s risk and prioritizes recommendations for hardening the most vulnerable systems that it discovers.
The CyCognito service includes automated processes supported by expert security analysts. You can request a demo of the Attack Surface Management system.
L’article 8 Best Attack Surface Monitoring Tools est apparu en premier sur Comparitech.

0 Commentaires