6.4 percent of the most popular home wi-fi routers sold on Amazon still use the manufacturer’s default administrator credentials, Comparitech researchers found. These routers, which number in the tens of thousands, can be remotely found and attacked using publicly available passwords, granting malicious hackers access to the victim’s home network.
Comparitech’s cybersecurity research team used freely available tools to scan the web for the top 12 home wi-fi router models sold on Amazon. They then used an automated script to attempt to log into each router’s administrative dashboard using the manufacturer’s default credentials.
In total, the researchers found and tested 9,927 routers. 635 were vulnerable to default password attacks.
Our results appear to indicate that some routers could be more insistent than others that users change the default password upon first setting up the device:
| Router model | Successful logins | # Tested |
|---|---|---|
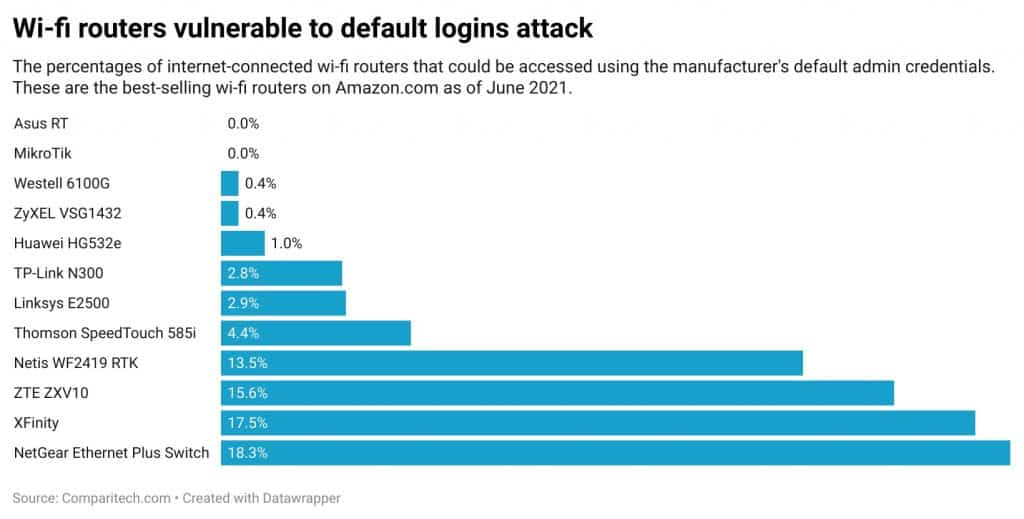
| Asus RT | 0.00% | 307 |
| MikroTik | 0.00% | 463 |
| Westell 6100G | 0.40% | 753 |
| ZyXEL VSG1432 | 0.40% | 1001 |
| Huawei HG532e | 1.00% | 546 |
| TP-Link N300 | 2.80% | 1000 |
| Linksys E2500 | 2.90% | 1000 |
| Thomson SpeedTouch 585i | 4.40% | 998 |
| Netis WF2419 RTK | 13.50% | 1000 |
| ZTE ZXV10 | 15.60% | 859 |
| XFinity | 17.50% | 1000 |
| NetGear Ethernet Plus Switch | 18.30% | 1000 |
AsusRT and MikroTik models could not be accessed at all despite hundreds of tests, indicating they require users to change their default passwords before an internet connection is allowed through. This is ideal from a cybersecurity perspective.
On the other end of the spectrum, roughly one in six ZTE ZXV10, XFinity, and NetGear Ethernet Plus Switch routers were found to be vulnerable to default password attacks unless the default admin password is changed.
What’s the threat?
If a bad actor gains access to your wi-fi router’s administrator panel, they could launch a number of attacks:
- DNS hijacking – DNS, or domain name system, is what associates domain names like “comparitech.com” into IP addresses that computers use to communicate over the internet. By tampering with DNS entries in the router, an attacker could redirect users to malicious sites and malware downloads without their knowledge.
- Eavesdropping – The attacker can monitor everything the victim does online on every device connected to the router, including what websites they visit and any unencrypted data sent over the network.
- Abuse your connection – The attacker could use the router as a proxy to download pirated content, visit illicit sites, or access illegal material. You could be suspected of or held liable for these activities.
These are just a sample of a long list of potential threats. If a router is compromised, so is every device connected to it.
How to change your wi-fi router’s default administrator password
Remember that your wi-fi router’s administrative password is (or should be) different from the password you use to connect to the internet. The administrative username and password are used to log into the device’s administrative dashboard, where you can manage your router’s settings and features.
Changing your router’s admin password is critical to your home’s cybersecurity. Be sure to create a unique and strong password.
You can usually access your router’s administrative panel by connecting to it normally using wi-fi or LAN. Then, open a web browser and type “192.168.0.1” or “192.168.1.1” (no quotes) into the URL bar, and press Enter. In most cases, this leads to the router dashboard login page.
Here are official resources on how to change administrative passwords for every vulnerable router in the study:
- TP-Link WR841N
- Westell 6100G (this product line seems to have been transferred to NetGear)
- Netis WF2419 RTK
- Linksys E2500
- Huawei HG532e
- XFinity XB6-T
- ZyXEL VSG1432-B101
- NETGEAR Ethernet Plus Switch (GS108PEv3)
- Thomson SpeedTouch 585i / TR-069
- ZTE ZXV10
Most router manufacturers can do better
Although some of the onus is on the consumer to change their default password, router makers should be more insistent that they do so.
The most obvious solution is to require users to change the router’s default admin password upon first setting the device. Before a public internet connection is allowed, the user must change the password.
Routers could also implement two-factor authentication to access administrator accounts. A one-time code sent to the owner’s smartphone would be required to log in.
Research methodology
This research was carried out in June 2021.
Researchers focused their efforts on the top 12 router models sold on Amazon.com. The marketplace results were filtered to find the most popular and frequently bought models.
They found the IP addresses of these routers on the internet using ZoomEye and Shodan.io, search engines that scan the web for specific internet-connected devices.
The manufacturer’s default login credentials for all models in the study were gathered from publicly accessible websites.
Researchers began by individually checking the publicly-obtained default credentials for each router model, ensuring the credentials were valid.
They then wrote automated scripts to attempt logins on the entire set of collected IP addresses.
Logins were recorded as successful or unsuccessful, giving us the results in the table above.
We did not access or modify the router in any way beyond the scope of our study, which only checked for a successful login using default credentials.
L’article One in 16 home wi-fi routers tested vulnerable to default password attacks: report est apparu en premier sur Comparitech.
0 Commentaires