SQLMap is a free tool that checks on database vulnerabilities. If you run a website, you’re vulnerable to a range of SQL-based hacker attacks that can compromise the database that lies behind many site functions. If hackers can break into your network and infect an endpoint, they can also use SQL injection techniques to compromise those databases that support back-office functions.
Your database lies at the heart of your business information system. It drives data sharing in ERP systems and stores sensitive data, such as customer records and turnover information. To fully understand potential vulnerability in this area, you need to know what an SQL injection attack is.
SQL injection attacks
SQL (pronounces “sequel”) is the Structured Query Language. It is the language that programs use to access data in a relational database. The language also includes commands to update or delete data held in database tables.
For end-users, access to a database is through a form, which will either be in a Web page or in the front-end of a piece of business software. The field into which you enter a query in a Google page is an example of this. The code behind the screen takes the input that users type into the field and wrap it in an SQL query. This then gets submitted to the database to extract matching records.
Hackers have discovered ways to put a full SQL statement or a clause of a statement into an input field. This can fool the query processing mechanisms embedded into the form and pass an entire SQL instruction on to the database rather than submitting the input as a query value.
This cheat is called “SQL injection” and it can give hackers full access to your database, bypassing the controls that are built into the coding of the application or Web page that contains the input field.
SQL injection attacks can enable hackers to steal the entire database or update values. The option to change data in a database enables hackers to steal money. Imagine if a customer was able to change the balance on an account from a negative sum to a positive amount. In automated systems, this would trigger a payment and the hackers could abscond with that money before anyone in the business becomes aware of the error.
Classifying SQL injection attacks
The Open Web Application Security Project (OWASP) creates a list of the top 10 system vulnerabilities that is regarded as the definitive list of weaknesses to look for. Vulnerability scanners promise to check for the OWASP Top 10. SQL Injection is the top threat listed by OWASP. The organization breaks that category down into four types.
- Classic SQL Injection
- Blind or Inference SQL Injection
- DBMS-specific SQL Injection
- Compounded SQL Injection
These categories are broken down further by the industry. A Classic SQL Injection attack is also known as an In-band attack. This category includes two possible methods – Error-based SQLI and Union-based SQLI.
Compound SQL Injection attacks add on another type of hacker attack to the SQL Injection activity. These are:
- Authentication attacks
- DDoS attacks
- DNS hijacking
- Cross-site scripting (XSS)
In the interests of brevity in this guide – which is focused on sqlmap – the definition of these attack strategies will not be covered here.
Checking for SQL injection vulnerabilities
Sqlmap enables you to try out the types of attacks that hackers implement on databases. This lets you see whether or not your systems are protected against attack.
Hackers are constantly inventing new attack strategies. However, the ways relational databases and SQL operate mean that there are only so many types of attacks that will work. In other words, new attacks are always variations on a theme. If you have a tool that can ensure protection against generic categories of attack, you can be sure that you have uncovered all possible vulnerabilities.
A sqlmap check attempts an attack in each of a number of categories – there are six in total. If one of these attacks succeeds, you know that you have a serious problem and part of the interface that fronts your database needs to be re-written to block that attack.
The types of attacks that sqlmap attempts are:
- Boolean-based blind SQL injection
- Time-based blind SQL injection
- Error-based SQL injection
- Union-based SQL injection
- Stacked queries
- Out-of-band attacks
The definitions used by the sqlmap developers don’t map exactly to the categories used by OWASP. The list includes both types of Classic SQL injection and both types of Blind SQL injection.
The stacked queries attack strategy performed by sqlmap should cover what OWASP terms DBMS-specific attacks. The Combined attack category of OWASP isn’t relevant to the SQL Injection-focused sqlmap detection system.
Logically, if you can ensure that your system isn’t vulnerable to an SQL injection attack, it automatically won’t be vulnerable to a combined attack. However, you should use other pen testing tools to check whether your site is vulnerable to DDoS attacks, XSS, or DNS hijacking. All systems are permanently liable to authentication attacks – you need to ensure a secure identity and access management strategy in order to protect your business from the threat of authentication cracking.
The sqlmap system checks work with the following DBMSs:
| MySQL | Microsoft SQL Server | Microsoft Access | MariaDB |
| Oracle | PostgreSQL | IBM DB2 | SQLite |
| Firebird | Sybase | SAP MaxDB | Informix |
| MemSQL | TiDB | CockroachDB | HSQLDB |
| H2 | MonetDB | Apache Derby | Apache Ignite |
| Amazon Redshift | Vertica | Mckoi | Presto |
| Altibase | MimerSQL | CrateDB | Greenplum |
| Drizzle | Cubrid | InterSystems Cache | IRIS |
| eXtremeDB | FrontBase | YugabyteDB | Virtuoso |
| Raima Database Manager |
System requirements for sqlmap
You can install sqlmap on Windows, macOS, and Linux.
The sqlmap system is written in Python, so you have to install Python 2.6 or later on your computer in order to run sqlmap. The current version as at July 2021 is 3.9.
To find out whether you have Python installed, on Windows open a command prompt and enter python –version. If you don’t have Python, you will see a message telling you to type python again without parameters. Type python and this will open up the Microsoft Store with the Python package set up to download. Click on the Get button and follow installation instructions.
If you have macOS type python –version. If you get an error message, enter the following commands:
$ xcode-select --install
$ ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)"
$ brew install python3In those lines, the $ represents the system prompt – don’t type that in.
If you have Linux, you will already have Python installed.
Install sqlmap
To install sqlmap:
- Go to the website for the sqlmap project at sqlmap.org.
- If you have Windows, click on the Download .zip file button. If you have macOS or Linux, click on the Download .tar.gz file button.
- Unpack the compressed file.
Your system will automatically name the directory the same as the compressed file. However, this is a very long name, so opt to have the new directory called just sqlmap. It doesn’t matter where on your computer you create that directory.
Running sqlmap
The sqlmap system is a command-line utility. There isn’t a GUI interface for it. So, go to the command line on your computer to use sqlmap. Change to the sqlmap directory that you created in order to run the utility. You do not have to compile any program.
The program that you run in order to use sqlmap is called sqlmap.py. It will not run unless you add an option to the end of the program name.
The options for sqlmap are:
|
-u URL |
The target URL Format: -u "https://ift.tt/3lDahDG" |
|
-d DIRECT |
Connection string for direct database connection Format: -d DBMS://DATABASE_FILEPATH or -d DBMS://USER:PASSWORD@DBMS_IP:DBMS_PORT/DATABASE_NAME |
|
-l LOGFILE |
Parse target(s) from Burp or WebScarab proxy log file |
|
-m BULKFILE |
Scan multiple targets given in a textual file Format: The file should contain a URL per line |
|
-r REQUESTFILE |
Load HTTP request from a file Format: The file can contain an HTTP or an HTTPS transaction |
|
-g GOOGLEDORK |
Process Google dork results as target URLs |
|
-c CONFIGFILE |
Load options from a configuration INI file |
|
--wizard |
A guided execution service |
|
--update |
Update sqlmap to the latest version |
|
--purge |
Clear out the sqlmap data folder |
|
--purge-output |
As above |
|
--dependencies |
Check for missing sqlmap dependencies |
|
-h |
Basic help |
|
-hh |
Advanced help |
|
-- version |
Show the version number |
You can’t run sqlmap without one of those options. There are many other options and it is often necessary to string several options in sequence on a command line.
A full attack requires so many options and inputs that it is easier to put all of those options in a file and then call the file instead of typing them all in. In this scenario, it is a convention to store all of the options in a text file with the extension .INI. You would include this list of options in the command line with the -c option followed by the file name. This method cuts out repeating typing in the whole long command over and over again to account for spelling mistakes or format errors.
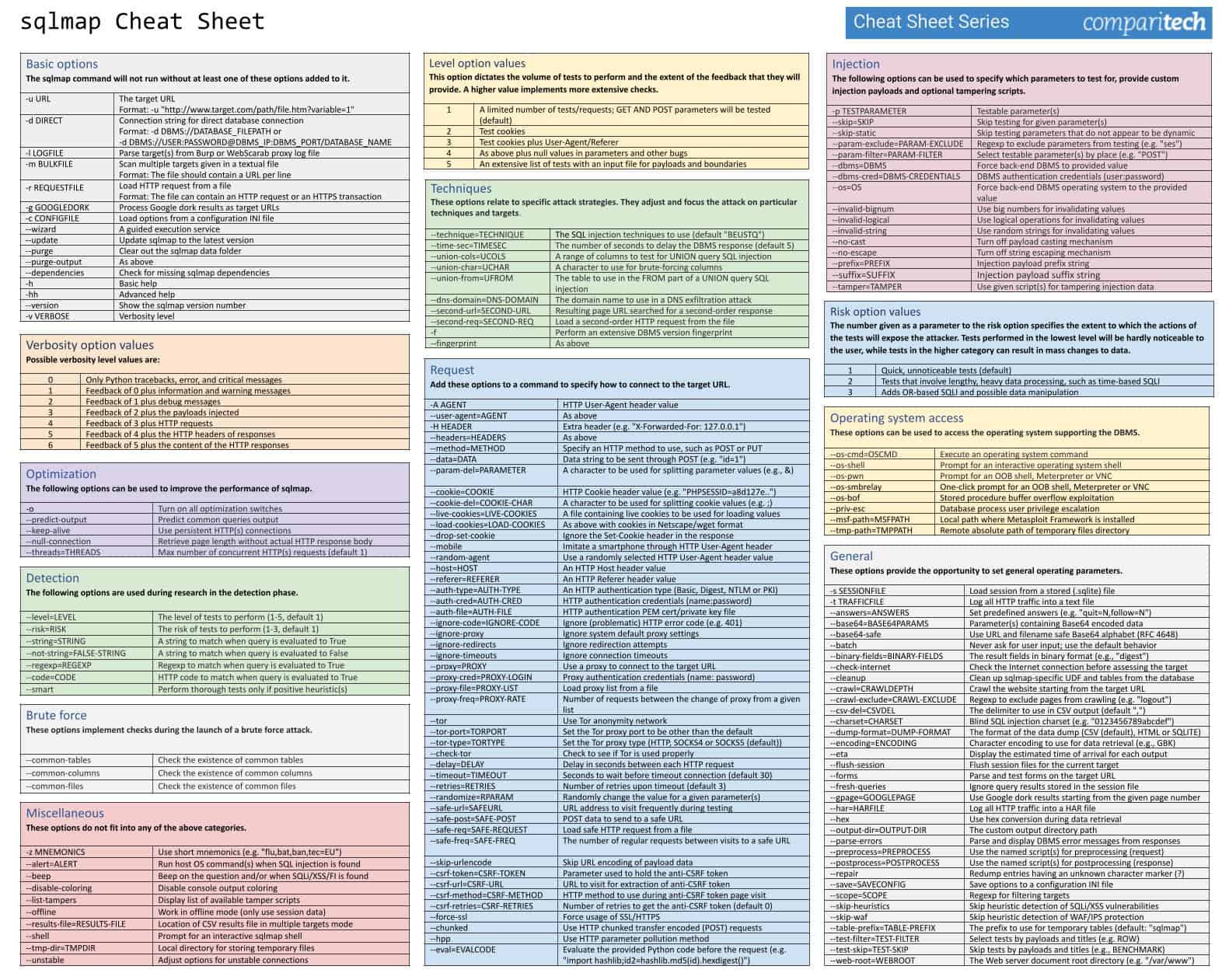
More sqlmap options
There are many other switches that you can add to a sqlmap command. Option parameters that are character-based should be enclosed in double-quotes (“ “), numerical parameters should not be quoted.
In the interests of brevity within this guide, we have presented all of these in a PDF file:
Click on the image above to open the full sqlmap Cheat Sheet JPG in a new window, or click here to download the sqlmap Cheat Sheet PDF.
Running an SQL injection attack scan with sqlmap
The large number of options available for sqlmap is daunting. There are too many options to comb through in order to work out how to form an SQL injection attack. The best way to acquire the knowledge of how to perform the different types of attacks is to learn by example.
To experience how a sqlmap test system proceeds, try the following test run, substituting the URL of your site for the marker <URL>. You need to include the schema on the front of the URL (http or https).
$ sqlmap.py -u “<URL>” --batch --bannerThis command will trigger a run-through of all of the sqlmap procedures, offering you options over the test as it proceeds.
The system will show the start time of the test. Each report line includes the time that each test completed.
The sqlmap service will test the connection to the Web server and then scan various aspects of the site. These attributes include the site’s default character set, a check for the presence of defense systems, such as a Web application firewall or intrusion detection systems.
The next phase of the test identifies the DBMS used for the site. It will attempt a series of attacks to probe the vulnerability of the site’s database. These are:
- A GET input attack – this identifies the susceptibility to Classic SQLI and XSS attacks
- DBMS-specific attacks
- Boolean-based blind SQLI
- The system will ask for a level and a risk value. If these are high enough, it will run a time-based blind SQLI
- An error-based SQLI attack
- A UNION-based SQLI if the level and risk values are high enough
- Stacked queries
In answer to the banner option used in this run, sqlmap completes its run by fetching the database banner. Finally, all extracted data with explanations of their meanings are written to a log file.
As you can see, without many options given on the command, the sqlmap system will run through a standard series of attacks and will check with the user for decisions over the depth of the test as the test progresses.
A small change in the command will run the same battery of tests but by using a POST as a test method instead of a GET.
Try the following command:
$ sqlmap.py -u “<URL>” --data=“id=1” --bannerPassword cracking with sqlmap
A change of just one word in the first command used for the previous section will give you a range of tests to see whether the credentials management system of your database has weaknesses.
Enter the following command:
$ sqlmap.py -u “<URL>” --batch --passwordAgain, you need to substitute your site’s URL for the <URL> marker.
When you run this command, sqlmap will initiate a series of tests and give you a number of options along the way.
The sqlmap run will try a time-based blind SQLI and then a UNION-based blind attack. It will then give you the option to store password hashes to a file for analysis with another tool and then gives the opportunity for a dictionary-based attack.
The services will try a series of well-known user account names and cycle through a list of often-used passwords against each candidate username. This is called a “cluster bomb” attack. The files suite of sqlmap includes a file of payloads for this attack but you can supply your own file instead.
Whenever sqlmap hits a username and password combination, it will display it. All actions for the run are then written to a log file before the program ends its run.
Get a list of databases on your system and their tables
Information is power and hackers first need to know what database instances you have on your system in order to hack into them. You can find out whether this basic information can be easily accessed by intruders with the following command:
$ sqlmap.py -u “<URL>” --batch --dbsThis test will include time-based, error-based, and UNION-based SQL injection attacks. It will then identify the DBMS brand and then list the database names. The information derived during the test run is then written to a log file as the program terminates.
Investigate a little further and get a list of the tables in one of those databases with the following command.
$ sqlmap.py -u “<URL>” --batch --tables -D <DATABASE>Enter the name of one of the database instances that you got from the list in the first query of this section.
This test batch includes time-based, error-based, and UNION-based SQL injection attacks. It will then list the names of the tables that are in the specified database instance. This data is written to a log file as the program finishes.
Get the contents of one of those tables with the following command:
$ sqlmap.py -u “<URL>” --batch --dump -T <TABLE> -D <DATABASE>Substitute the name of one of the tables you discovered for the <TABLE> marker in that command format.
The test will perform a UNION-based SQL injection attack and then query the named table, showing its records on the screen. This information is written to a log file and then the program terminates.
Explore the Cheat Sheet
The commands shown in this guide are just the start. Successful execution of these tests will give you the confidence to look through our sqlmap Cheat Sheet PDF and try other SQL injection tests.
L’article sqlmap Cheat Sheet est apparu en premier sur Comparitech.
0 Commentaires