Antimalware systems and firewalls were the traditional methods of securing an IT system. These two security system categories are still needed, but they are not enough. Hackers have new techniques to damage a system, and they often facilitate regular manual access by the hacker onto the network and its endpoints.
The major hacker groups in the world have boiler rooms full of workers trying to trick company employees into giving away their system access credentials. They also maintain teams of programmers and analysts to design new software packages that can access logging systems and remove indicators of their presence.
Here is our list of the seven best hacker detection software packages:
- SolarWinds Security Event Manager EDITOR’S CHOICE A standards-compliant log manager and SIEM system that includes file integrity management and a threat intelligence feed. It runs as a virtual appliance. Get a 30-day free trial.
- Exabeam A nest generation SIEM that has a market-leading threat intelligence feed and includes automated processes for intrusion remediation. This is a cloud-based service.
- ManageEngine Log360 A SIEM system and log manager that unifies security monitoring for many sites plus cloud resources. Available for Windows Server.
- LogRhythm A next-generation SIEM that is available as a cloud service, as an appliance, or as a software package for Windows Server.
- Rapid7 Insight Platform, This bundle of cloud-based services combined with endpoint-resident elements creates a complete cybersecurity system, including a SIEM.
- Splunk Enterprise Security This is a SIEM expansion of the well-known log capture and event searching system. It installs on Windows and Linux.
- FireEye Helix A cloud-based security platform that includes a range of tools that consists of a SIEM for intrusion detection.
Hacking is now a big-budget enterprise, and the successful teams that thrive need to recover their initial project costs by making the most out of system access. These teams can gain regular access to private networks for years, regularly inspecting data files for anything that could prove profitable and even acquiring system resources for their use.
Hackers can move into a corporate IT system and become familiar and comfortable with all facilities as any regular user. You might have hackers on your system that have been there for longer than many of your employees. You don’t know about these intrusions because they are masked. These unwelcome guests are called “Advanced Persistent Threats” (APTs). You need to adopt new security strategies now to detect and block those hackers.
Advanced persistent threats
An APT is challenging to spot because hackers use valid user accounts or implement persistence and cloaking routines to cover their tracks and keep their backdoor open. The activities of the hacker also include malware processes. This is because APT intruders develop toolkits to facilitate activities.
The hacker activity might not relate directly to the business. Those targets are not broken into for the value of their data but the usefulness of their equipment and services. Examples of these facilities hijacking include mining for cryptocurrencies and the construction of underworld VPNs.
Although all major VPN providers say they do not log user activities and ensure total anonymity, this is not always true. Hackers make doubly sure that they cannot be traced by not bothering with commercial VPN services but setting up their own instead. Hacker cloaking tools delete activity logs related to the connections through an APT host, enabling hackers to mask their actual locations while attacking other networks. Similarly, cryptocurrency miners remove all indicators of their activities, leaving system administrators mystified about why their electricity bill has rocketed.
Hacker detection systems
Two types of software were designed to detect hacker activity. In truth, these two types are one category but using two different names. These are Intrusion Detection Systems (IDSs) and Security Information and Event Management (SIEM) packages.
SIEM combines two strategies, and there are two types of IDSs. The two methodologies encapsulated by SIEM are Security Information Management (SIM) and Security Event Management (SEM). SIM scours all logs for abnormal activity, and SEM reads packets as they pass over the network, looking for suspicious indicators. The two types of IDSs are host-based intrusion detection systems (HIDS), which scour through logs, and network-based intrusion detection systems (NIDS), which watch live network traffic for signs of trouble.
So, when you are looking for hacker detection software, you should focus on either an IDS or a SIEM. Both IDS and SIEM have evolved in step. Intrusion Prevention Systems (IPSs) can interact with other security systems, such as access rights managers or firewalls, to automatically shut down hacker access. SIEMs have acquired the same capability. The collaborative mechanism to close hacker accounts in a SIEM system is called SOAR, short for “Security Orchestration, Automation, and Response.” SIEM packages that include this ability are called “next-gen SIEMs.”
The best hacker detection software
The best hacker detection systems offer additional services. For example, vendors combine SIEM systems with log management services. Those are useful for data privacy compliance because such standards as PCI DSS, HIPAA, and GDPR require logs to be stored and organized for spot-check auditing. Other providers have assembled platforms that combine antimalware and firewalls with IDS systems.
What should you look for in a hacker detection system?
We reviewed the market for hacker detection software and analyzed the options based on the following criteria:
- A platform that bundles hacker detection in with malware prevention
- A system that includes automated processes to shut down hacker activity
- An intelligence feed that updates the detection methods automatically
- AI-based User and Entity Behavior Analytics (UEBA) to adjust detection methods
- A scalable service that can be used by small and large organizations alike
- A free assessment period offered by a trial, a demo, or a money-back guarantee
- Value for money represented by a price that is reasonable when compared to the functions offered
With these criteria in mind, we looked at the security software market and identified some very attractive packages that you should consider for protection against intruders.
The Best Hacker Detection Software
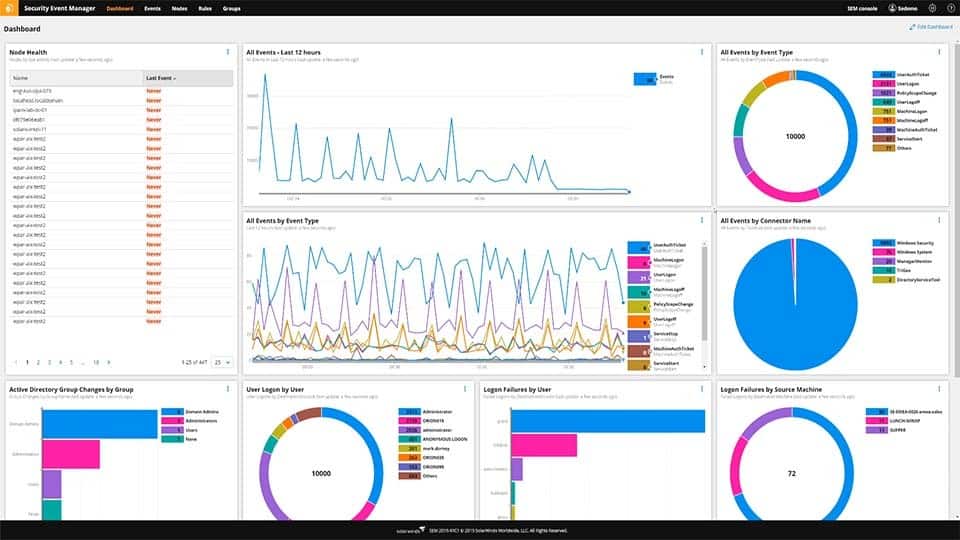
1.SolarWinds Security Event Manager (EDITOR’S CHOICE)
SolarWinds Security Event Manager is a SIEM based on a competent log manager supporting PCI DSS, SOX, HIPAA, GLBA, and NERC CIP. A nice feature of the log manager in this tool is its file integrity monitor that protects all collated log files from tampering by intruders.
SolarWinds manages its threat intelligence gathering service, which shares attack information between its SIEM clients. This feeds into each implementation over the internet, updating threat hunting procedures with new signatures of suspicious activity to look out for.
As the SIEM detects hacker activities, it implements mitigation procedures, which is called Active Response. It also lays down a root cause analysis trace, which acts as a vulnerability manager, enabling systems administrators to harden the system to prevent the same entry point from being exploited again.
The SolarWinds Security Event Manager installs on top of virtualization, which can be Hyper-V or VMWare vSphere. It can also be hosted on an AWS or Azure account. The system is available for a 30-day free trial.
EDITOR’S CHOICE
SolarWinds Security Event Manager is our top pick for a hacker detection system because it provides complete standards-compliant log management and provides a security system. This offers excellent value for money by combining two necessary functions. The security system operates as a SIEM and provides alerts on detecting hacker activity or an automated response mechanism.
Get a 30-day free trial: solarwinds.com/security-event-manager/registration
Operating system: On-premises virtual appliance or virtual cloud server
2. Exabeam
Exabeam NextGen SIEM is a cloud platform that ties together a collection of security tools. The system includes an on-site agent program that collects data and implements solutions. The connection between the agent and the Exabeam server is protected by encryption. A significant part of that source data comes from log messages.
The cloud platform includes a log server and consolidator. This also stores those log messages so that they can be accessed for standards compliance auditing. The platform consists of a data analysis function that searches messages for signs of intrusion.
Two processes inform intrusion detection. One is the User and Entity Behavior Analytics (UEBA) service. This establishes a baseline for anomaly searches by establishing a baseline of normal behavior on the system. This step can help highlight suspicious hacker activity because unusual behavior by one user account will stand out from the norm.
Threat detection is further enhanced by a threat intelligence feed from SkyFormation, a division of Exabeam. This is a pool of attack experiences that is regularly reaped from more than 30 cloud platforms. So, if an attack happens on one of those systems, your SIEM will instantly be updated with signatures to look out for.
Exabeam includes a SOAR called Incident Responder. This can interact with Active Directory, email servers, and firewalls to block suspicious accounts. You can request a demo of this next-gen SIEM to see how it detects hacker activity.
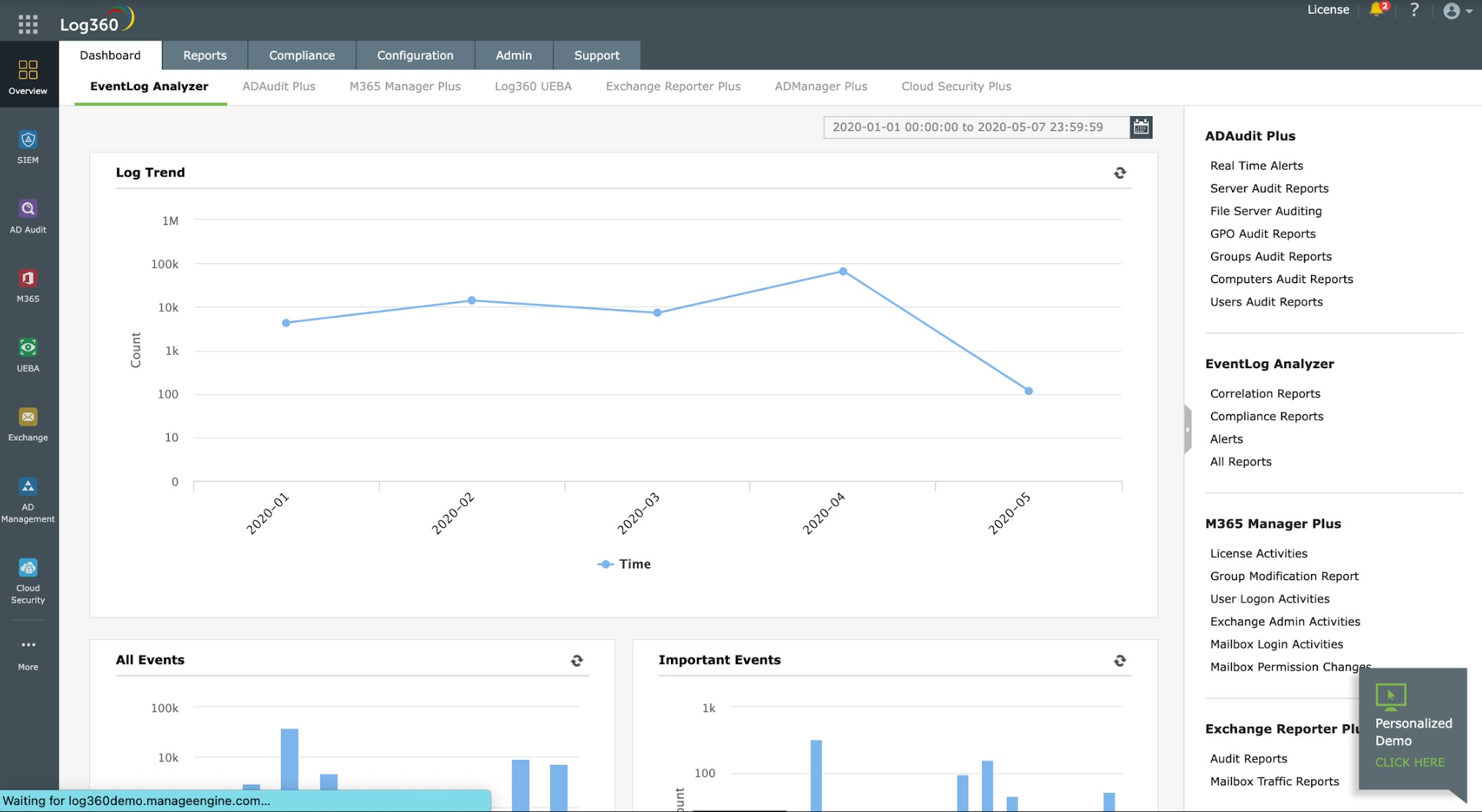
3. ManageEngine Log360
ManageEngine Log360 is a log management system that includes SIEM capabilities. The system also gets external sources of data to look out for hacker activities. These feeds list IP addresses that are associated with hacker attacks performed in other locations.
The Log360 accesses all types of logs – Windows Events, Syslog, and application-generated messages. The tool can monitor cloud services because it can gather AWS, Azure, and Exchange Online logs.
SOAR services in Log360 integrate with Active Directory. This not only monitors the access rights manager but also sends shutdown instructions to suspend suspicious user accounts. The system can also interact with IIS and Apache Web servers, and it can monitor activity in Oracle databases. Log360 can query firewalls, routers, and switches, and it is also blocking traffic based on IP address by interacting with those devices.
You can install Log360 software on Windows and Windows Server. There is a free edition of the package, which is limited to monitoring 25 devices and five log sources. You can get a 30-day free trial of the paid version, which is called the Premium edition.
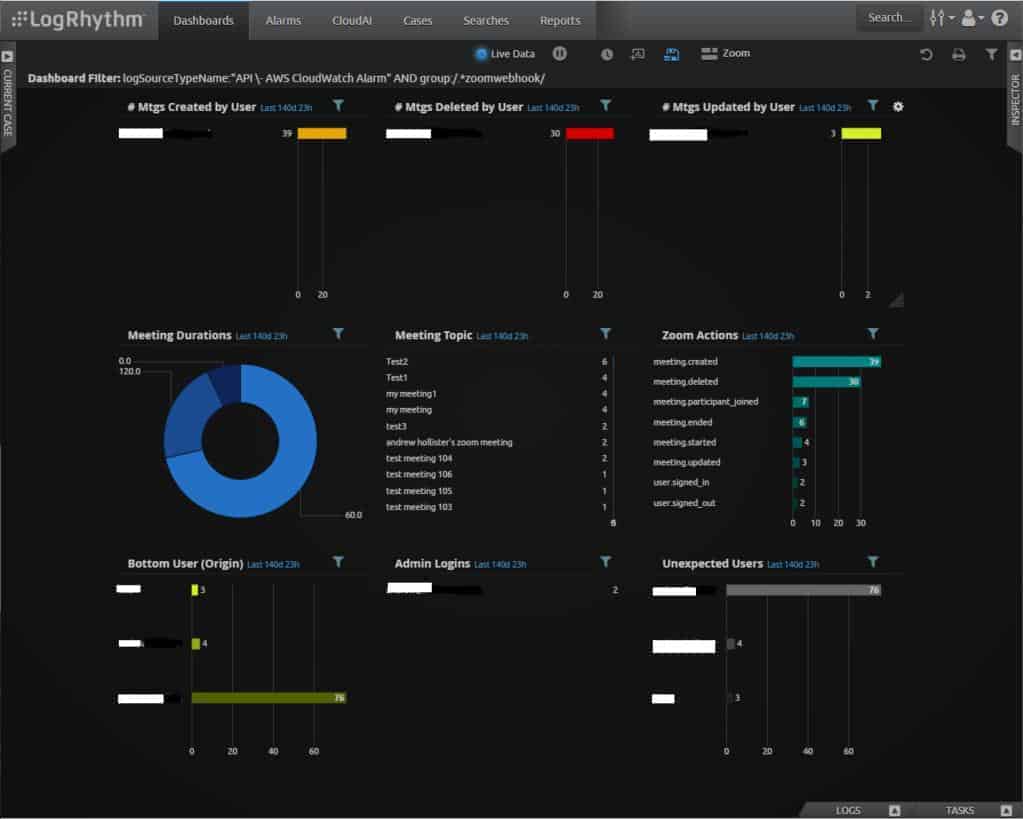
4. LogRhythm
LogRhythm is a full IPS composed of a NextGen SIEM plus a NIDS called network detection and response (NDR). The system includes SOAR capabilities to shut down hacker activity once it has been detected.
There are two parts of the LogRhythm system that are resident on the monitored site. These are SysMon, a log data collector, and NetMon, a network traffic monitor. These elements feed source data into the analytical engine of the SIEM.
The LogRhythm cloud-based platform for hacker detection is called the XDR Stack. The layers in the stack are AnalytiX, which consolidates uploaded log messages and then searches through them for signs of intrusion, DetectX, which applies threat intelligence, and RespondX, which is the SOAR. The threat mitigation part of RespondX is called SmartResponse Automation. It suspends user accounts in Active Directory and updates firewall tables to block communication with specific IP addresses.
The system can be deepened with extra modules. These are User XDR, a UEBA module, and MistNet, a network-based intrusion detection system.
Although LogRhythm is a cloud-based SaaS platform, it is possible to get the system as a software package for Windows Server or as an appliance. You can request a live demo of the cloud service.
5. Rapid7 Insight Platform
Rapid 7’s Insight Platform is a cloud-based platform of hacker detection tools based on a next-gen SIEM. The modules of the platform can each be subscribed to individually. The SIEM tool is called InsightIDR – IDR stands for Intrusion Detection and Response. It includes UEBA for the elimination of false-positive reporting and more accurate anomaly detection. Hacker detection rules are constantly updated by a threat intelligence feed.
While all of the data processing of InsightIDR takes place on the cloud, there needs to be an agent program installed on your site to interact with that remote service. The communication channel between these two parts of the service is encrypted. The primary data source for InsightIDR comes from logs. All of the log messages from your network and endpoints get uploaded to a log server, putting all of these into a standard format. The IDR then searches through these messages for indications of hacker activity.
InsightIDR includes a deception technology module. This sets up false paths and honey pots to trap hackers. This protects stores of sensitive data by diverting hackers, and it also makes hackers easier to find.
You can get a look at the Rapid7 Insight platform on a 30-day free trial.
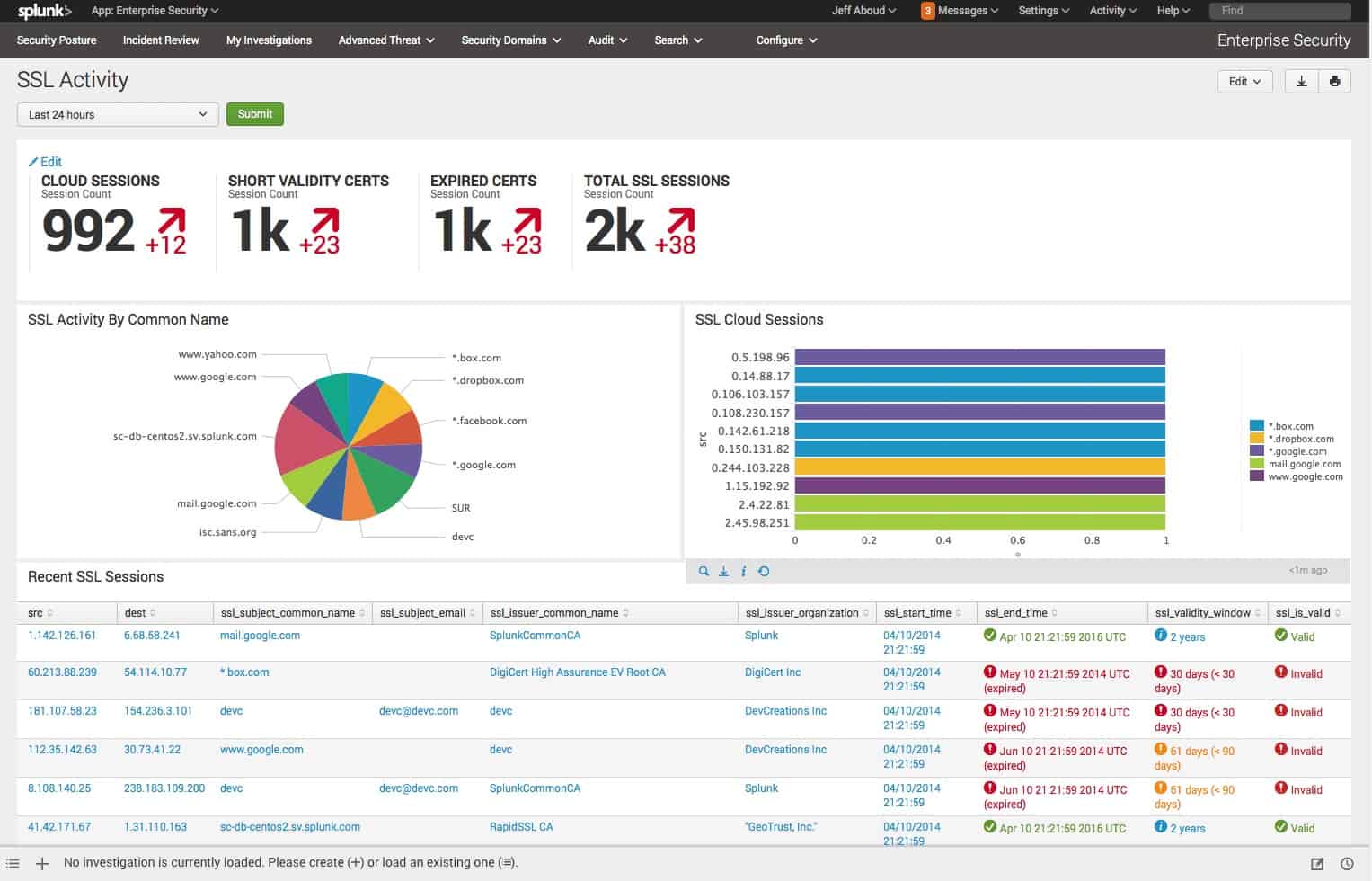
6. Splunk Enterprise Security
Splunk is a widely used free network data analysis tool. It can be extended by a SIEM system, which is charged for. That system is called Splunk Enterprise Security. The data feeds into this service are live network traffic inspections and system log messages.
The dashboard for Splunk Enterprise Security shows live system statistics gathered by the analytical engine as new data feeds are processed. The system will raise an alert if it detects unusual activity that could indicate the presence of a hacker. The detection system, called Asset Investigator, homes in on specific locations on the system. This gives you a range of options on what you want to do to deal with the suspected intrusion.
The Splunk Enterprise Security package includes an automated response module called the Adaptive Operations Framework. This interacts with other systems to automatically black hacker activity when it is detected.
Splunk Enterprise Security installs on Windows or Linux, and you can get it on a 60-day free trial. There is also a SaaS version called Splunk Cloud. That service can be assessed on a 15-day free trial.
7. FireEye Helix
FireEye Helix is a threat detection platform delivered from the cloud. This is the next-generation SIEM service. It includes a user and entity behavior analytics module that tracks suspected hacker activity called lateral movement detection. This links together events are occurring on different parts of the system that only seem suspicious once examined in combination.
The system also relies on a threat intelligence feed that adapts threat hunting procedures with information about attacks that have recently been discovered on the techniques of other companies. The threat detection and linked mitigation responses are connected in a chain that is laid out in a “playbook.” This dictates how the SIEM system operates, and it is possible to create your playbooks.
Playbooks can also be adapted by integrations, which allow Helix to interact with other tools on your system, both for data collection and responses. This service is suitable for those businesses that need to follow a specific data privacy standard because the playbooks can all be automatically adjusted according to a standards setting in the service’s dashboard.
FireEye has constructed a self-guided tour of the Helix platform.
L’article 7 Best Hacker Detection Software est apparu en premier sur Comparitech.


0 Commentaires